SaaS Security
Begin Scanning a Google Cloud Storage App
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
-
-
- Begin Scanning an Amazon S3 App
- Begin Scanning a Bitbucket App
- Begin Scanning a Box App
- Begin Scanning ChatGPT Enterprise App
- Begin Scanning a Cisco Webex Teams App
- Begin Scanning a Confluence App
- Begin Scanning a Confluence Data Center App
- Begin Scanning a Dropbox App
- Begin Scanning a GitHub App
- Begin Scanning a Gmail App
- Begin Scanning a Google Cloud Storage App
- Begin Scanning a Google Drive App
- Begin Scanning a Jira App
- Begin Scanning a Jira Data Center App
- Begin Scanning a Microsoft Azure Storage App
- Begin Scanning a Microsoft Exchange App
- Begin Scanning a Microsoft Teams App
- Begin Scanning Office 365 Apps
- Begin Scanning a Salesforce App
- Begin Scanning a ServiceNow App
- Begin Scanning a ShareFile App
- Begin Scanning a Slack Enterprise App
- Begin Scanning a Slack for Pro and Business App
- Begin Scanning a Workday App
- Begin Scanning a Zendesk App
- Begin Scanning a Zoom App
- Perform Actions on Sanctioned Apps
- API Throttling
- Configure Classification Labels
- Microsoft Labeling for Office 365
- Google Drive Labeling
- Configure Phishing Analysis
- Configure WildFire Analysis
- Fine-Tune Policy
-
- What is an Incident?
- Filter Incidents
- Configure Slack Notification Alerts on Data Security
- Security Controls Incident Details
- Track Down Threats with WildFire Report
- Customize the Incident Categories
- Close Incidents
- Download Assets for Incidents
- View Asset Snippets for Incidents
- Modify Incident Status
- Email Asset Owners
- Generate Reports on Data Security
- Integrate CIE with Data Security
- Search in Data Security
-
-
- View Usage Data for Unsanctioned SaaS Apps
- SaaS Visibility Application Attributes
- How SaaS Security Inline Determines an App's Risk Score
- Identify Risky Unsanctioned SaaS Apps and Users
- Generate the SaaS Security Report
- Filter Unsanctioned SaaS Apps
-
- SaaS Policy Rule Recommendations
- App-ID Cloud Engine
- Guidelines for SaaS Policy Rule Recommendations
- Apply Predefined SaaS Policy Rule Recommendations
- Create SaaS Policy Rule Recommendations
- Enable SaaS Policy Rule Recommendations
- Monitor SaaS Policy Rule Recommendations
- Delete SaaS Policy Rule Recommendations
- Modify Active SaaS Policy Rule Recommendations
- Manage Enforcement of Rule Recommendations on Strata Cloud Manager
- Manage Enforcement of Rule Recommendations on Panorama
- Tag Discovered SaaS Apps
- Apply Tag Recommendations to Sanctioned Apps
- Change Risk Score for Discovered SaaS Apps
- Troubleshoot Issues on SaaS Security Inline
-
-
- Onboarding Overview for Supported SaaS Apps
- Onboard an Aha.io App to SSPM
- Onboard an Alteryx Designer Cloud App to SSPM
- Onboard an Aptible App to SSPM
- Onboard an ArcGIS App to SSPM
- Onboard an Articulate Global App to SSPM
- Onboard an Atlassian App to SSPM
- Onboard a BambooHR App to SSPM
- Onboard a Basecamp App to SSPM
- Onboard a Bitbucket App to SSPM
- Onboard a Bito AI App to SSPM
- Onboard a BlueJeans App to SSPM
- Onboard a Box App to SSPM
- Onboard a Bright Security App to SSPM
- Onboard a Celonis App to SSPM
- Onboard a Cisco Meraki App to SSPM
- Onboard a Claude App to SSPM
- Onboard a ClickUp App to SSPM
- Onboard a Codeium App to SSPM
- Onboard a Cody App to SSPM
- Onboard a Confluence App to SSPM
- Onboard a Contentful App to SSPM
- Onboard a Convo App to SSPM
- Onboard a Couchbase App to SSPM
- Onboard a Coveo App to SSPM
- Onboard a Crowdin Enterprise App to SSPM
- Onboard a Customer.io App to SSPM
- Onboard a Databricks App to SSPM
- Onboard a Datadog App to SSPM
- Onboard a DocHub App to SSPM
- Onboard a DocuSign App to SSPM
- Onboard a Dropbox Business App to SSPM
- Onboard an Envoy App to SSPM
- Onboard an Expiration Reminder App to SSPM
- Onboard a Gainsight PX App to SSPM
- Onboard a GitHub Enterprise App to SSPM
- Onboard a GitLab App to SSPM
- Onboard a Google Analytics App to SSPM
- Onboard a Google Workspace App to SSPM
- Onboard a GoTo Meeting App to SSPM
- Onboard a Grammarly App to SSPM
- Onboard a Harness App to SSPM
- Onboard a Hellonext App to SSPM
- Onboard a Hugging Face App to SSPM
- Onboard an IDrive App to SSPM
- Onboard an Intercom App to SSPM
- Onboard a Jira App to SSPM
- Onboard a Kanbanize App to SSPM
- Onboard a Kanban Tool App to SSPM
- Onboard a Krisp App to SSPM
- Onboard a Kustomer App to SSPM
- Onboard a Lokalise App to SSPM
- Onboard a Microsoft 365 Copilot App to SSPM
- Onboard a Microsoft Azure AD App to SSPM
- Onboard a Microsoft Exchange App to SSPM
- Onboard a Microsoft OneDrive App to SSPM
- Onboard a Microsoft Outlook App to SSPM
- Onboard a Microsoft Power BI App to SSPM
- Onboard a Microsoft SharePoint App to SSPM
- Onboard a Microsoft Teams App to SSPM
- Onboard a Miro App to SSPM
- Onboard a monday.com App to SSPM
- Onboard a MongoDB Atlas App to SSPM
- Onboard a MuleSoft App to SSPM
- Onboard a Mural App to SSPM
- Onboard a Notta App to SSPM
- Onboard an Office 365 App to SSPM
- Onboard Office 365 Productivity Apps to SSPM
- Onboard an Okta App to SSPM
- Onboard an OpenAI App to SSPM
- Onboard a PagerDuty App to SSPM
- Onboard a Perplexity App to SSPM
- Onboard a Qodo App to SSPM
- Onboard a RingCentral App to SSPM
- Onboard a Salesforce App to SSPM
- Onboard an SAP Ariba App to SSPM
- Onboard a ServiceNow App to SSPM
- Onboard a Slack Enterprise App to SSPM
- Onboard a Snowflake App to SSPM
- Onboard a SparkPost App to SSPM
- Onboard a Tableau Cloud App to SSPM
- Onboard a Tabnine App to SSPM
- Onboard a Webex App to SSPM
- Onboard a Weights & Biases App to SSPM
- Onboard a Workday App to SSPM
- Onboard a Wrike App to SSPM
- Onboard a YouTrack App to SSPM
- Onboard a Zendesk App to SSPM
- Onboard a Zoom App to SSPM
- Onboarding an App Using Azure AD Credentials
- Onboarding an App Using Okta Credentials
- Register an Azure AD Client Application
- View the Health Status of Application Scans
- Delete SaaS Apps Managed by SSPM
-
-
-
- New Features Introduced in December 2024
- New Features Introduced in November 2024
- New Features Introduced in October 2024
- New Features Introduced in August 2024
- New Features Introduced in July 2024
- New Features Introduced in June 2024
- New Features Introduced in May 2024
- New Features Introduced in April 2024
- New Features Introduced in March 2024
- New Features Introduced in January 2024
-
- New Features Introduced in November 2023
- New Features Introduced in October 2023
- New Features Introduced in September 2023
- New Features Introduced in August 2023
- New Features Introduced in July 2023
- New Features Introduced in June 2023
- New Features Introduced in May 2023
- New Features Introduced in April 2023
- New Features Introduced in March 2023
- New Features Introduced in January 2023
-
- New Features Introduced in December 2021
- New Features Introduced in October 2021
- New Features Introduced in September 2021
- New Features Introduced in August 2021
- New Features Introduced in July 2021
- New Features Introduced in June 2021
- New Features Introduced in May 2021
- New Features Introduced in March 2021
- New Features Introduced in January 2021
Begin Scanning a Google Cloud Storage App
Add the Google Cloud Storage app for GCP (Global Cloud
Platform) to Data Security to begin scanning and monitoring
assets for possible security risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Before you begin scanning a Google Cloud Storage app, you must create a service account and
enable administrator and client API access.
To connect the Google Cloud Storage app to Data Security and begin scanning assets, you need
to:
- Create a service account from Google Cloud Console or use an existing service account.
- Enable administrator and client API access from Google Admin Console.
- Add the Google Cloud Storage app to Data Security.
- Configure initial scan settings.
Support for automated remediation capabilities varies by SaaS application.
- Create a Service Account for Google Cloud Storage
- Use an Existing Project and Service Account
- Add Google Cloud Storage App
- Identify Risks
- View Scan Settings for Project and Buckets
- Customize Google Cloud Storage App
Create a Service Account for Google Cloud Storage
You must create a service account before you
can add the Google Cloud Storage app; alternatively, you can
Use an Existing Project and Service Account
instead. As you prepare
the Google Cloud Storage account, take note of the following values,
as they are required to add the Google Cloud
Storage app
on Data Security. Each web interface might
refer to the value by a different name.Item | Web interface | Description | ||
|---|---|---|---|---|
Google Cloud Console | Google Admin Console | SaaS Security | ||
Google administrator email | Google account | Google account | Administrator email | The Google account you used to log in to Google Cloud Console to create the service account in
Google Cloud Storage. You will use this same Google account
to log in to the Google Admin Console when to enable API
client access. You specify this email on Data Security
when adding the Google Cloud Storage app. |
Private Key | Private key | n/a | Certificate | A P12 format private key certificate issued
from your Google service account. This required certificate is uploaded
on Data Security when adding the Google Cloud Storage app. |
Private Key Password | Private key password | n/a | n/a | The default password for the new private
key. |
Client ID | Client ID and Unique ID | Client ID | n/a | The client ID automatically displays on
Google Cloud Console when enabling Google Cloud Storage domain-wide
delegation, on Data Security when you add the Google Cloud Storage app,
and on Google Admin Console when enable API client access. |
Service Account ID | Email and Service account ID | n/a | Service account ID | The service account ID is automatically generated on the Google Cloud Console when you create the
service project and is partly based on the service account
name you assign. You will specify the service account ID on
SaaS Security web interface when you add the Google Cloud
Storage app. |
- Log in to Google Cloud Console as the Google Cloud Storage administrator.If you have not used the Google Cloud Console before, Agree to the Google Cloud Platform Terms of Service. Otherwise, proceed to the next step.
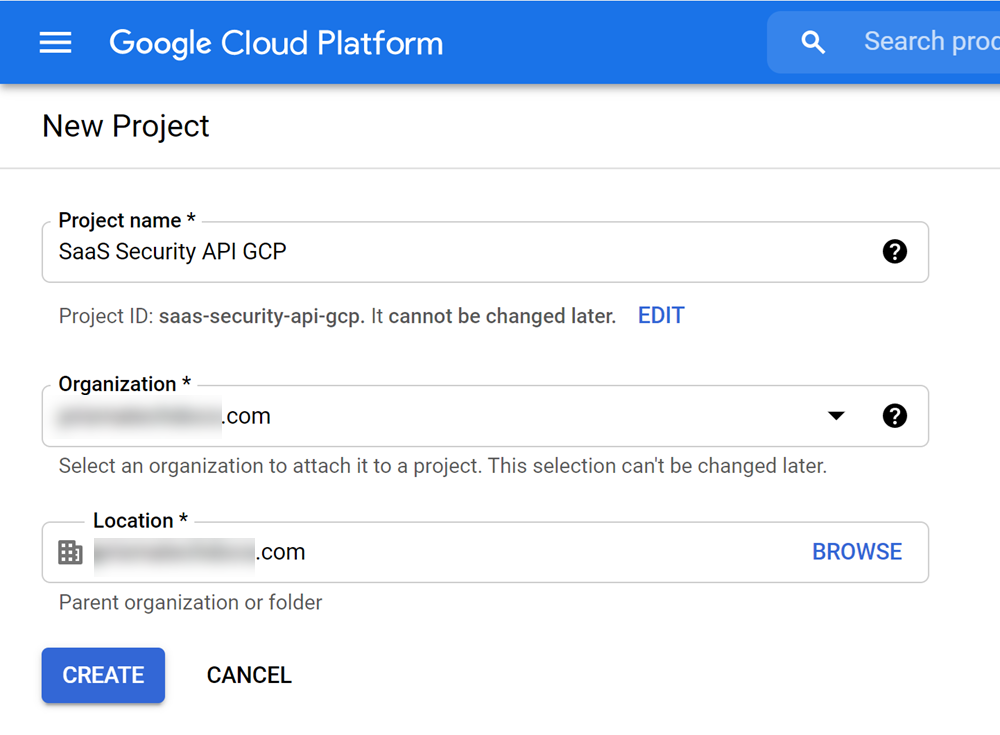
- Create a new project from GCP.
- In the drop-down at the top of the screen, open your project list, then NEW PROJECT.
- Name your project (for example, Data Security GCP), select your organization (domain), then CREATE the project.

- Authorize OAuth consent for the new project.
- Select APIs & ServicesOAuth consent screen.
- Select the project you created above.
- Select Internal user type, then CREATE.
- Specify an App name (for example, Data Security) and User support email.
- Click + ADD DOMAIN, then specify Authorized domain—the domain name for your Google administrator email, to authorize.
- Specify Developer contact information, then SAVE AND CONTINUE.
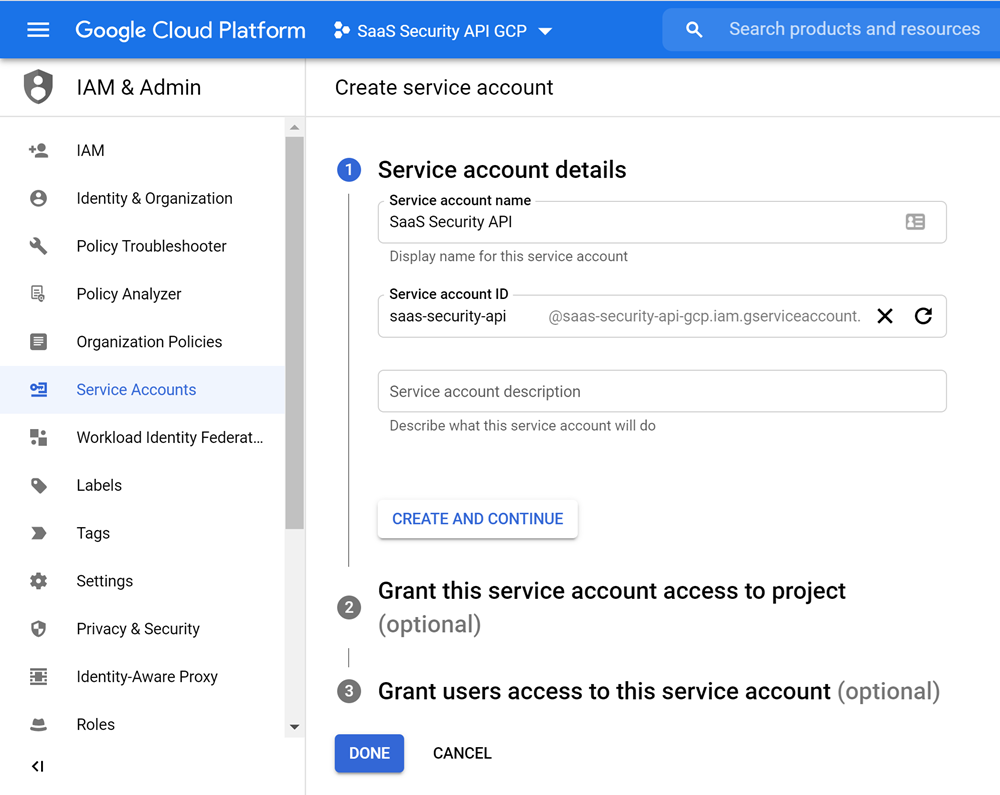
- Create the Service Account Key for the new project.
- Select APIs & ServicesCredentialsCREATE CREDENTIALS.
- Select Service account and specify a Service account name (for example, Data Security), which automatically populates the Service account ID, then CREATECONTINUEDONE, authorizing no optional permissions or access.

- Enable Domain-wide Delegation for the new service account.GCP creates a service account client when domain-wide delegation is enabled on a service account.
- Select APIs & ServicesCredentials.
- In Service Accounts, locate the service account, then Edit service account.
- Record the Email, which you’ll use to specify the Service account ID later on SaaS Security web interface.
- Select Enable Google Domain-wide Delegation, then SAVE.If prompted to provide a value in Product name for the consent screen field, you did not perform3and4as instructed. GCP is very particular.

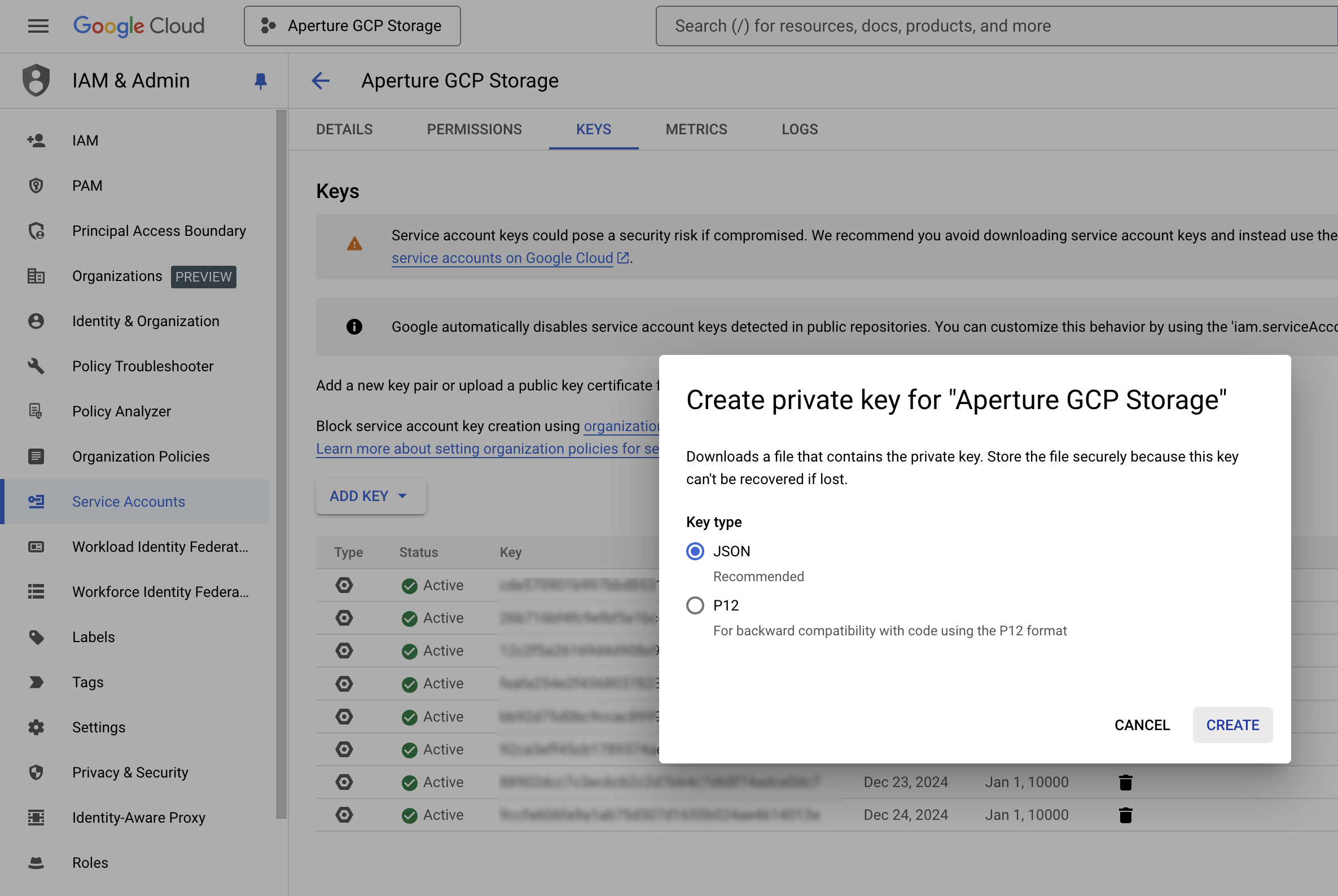
- Select KEYSADD KEYCreate new keyJSONCREATE.The key is downloaded automatically on your device. Upload the key during onboarding.

- Store the JSON key in a secure location as the key can't be recovered if lost.Data Security requires this key when youAdd Google Cloud Storage App.
- Save your changes.
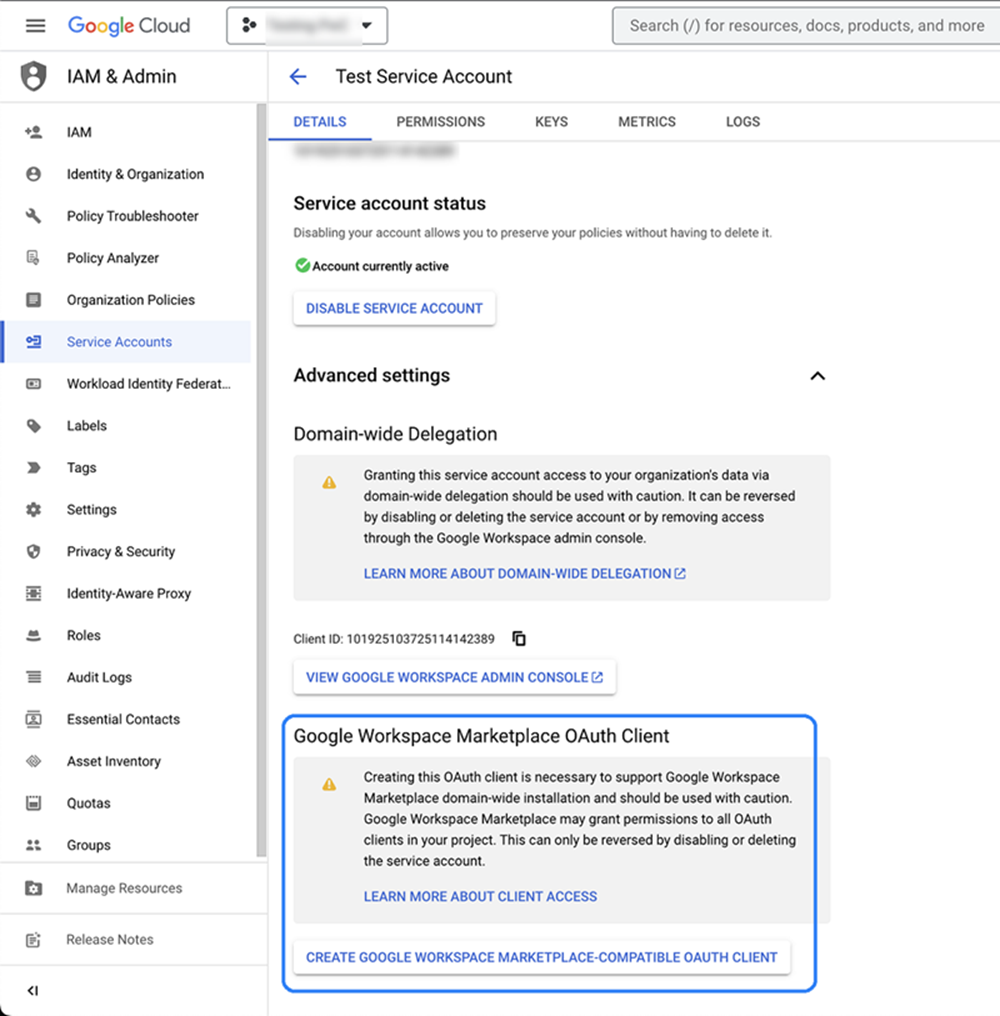
- To create a service account client, select Service AccountsAdvanced settings. Click CREATE GOOGLE WORKSPACE MARKETPLACE-COMPATIBLE OAUTH CLIENT. You’ll then be able to see the same client in the OAuth 2.0 Client IDs list.

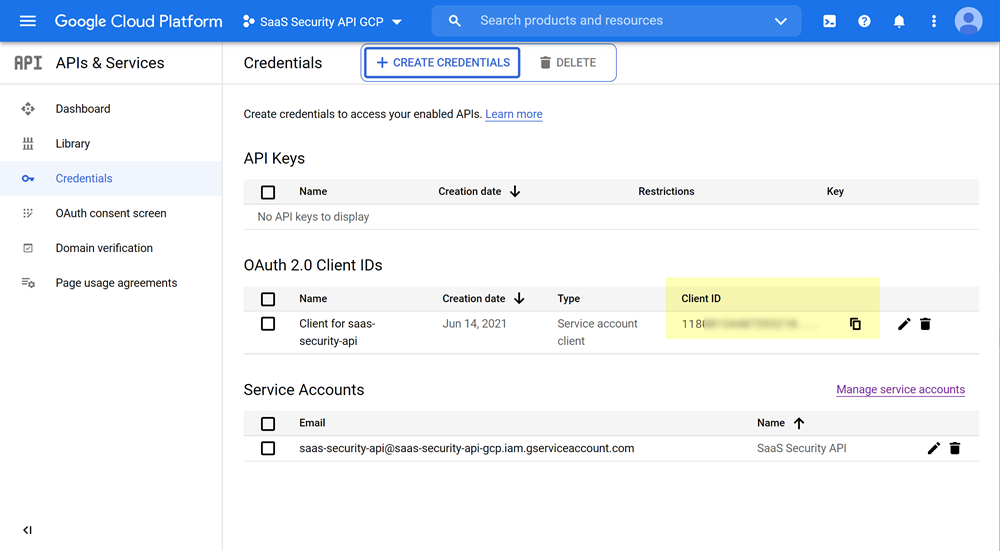
- Retrieve and save the Client ID for the new service account client.
- Select APIs & ServicesCredentials.
- In OAuth 2.0 Client IDs, locate the client, then copy and save the Client ID.

- Enable API access for the new service account.
- Select the project.
- Select APIs & Services+ ENABLE APIS AND SERVICES.
- Search for and ENABLE the following APIs:
- Google Admin SDK API
- Google Cloud Resource Manager API
- Google Cloud Storage API
- Google Cloud Pub or Sub API
- Google Identity and Access Management (IAM) API
- Google Cloud Logging API
- Provide the local admin account with the required roles.You’ll use this admin account to onboard Data Security. This admin account does not need to be a Super Admin; however, the admin account does require minimum permissions at the organization level—Storage Admin and Security Admin permissions.
- Log in to Google Cloud Console as Super Admin.
- At the top of the screen and in the project list, select your organization.
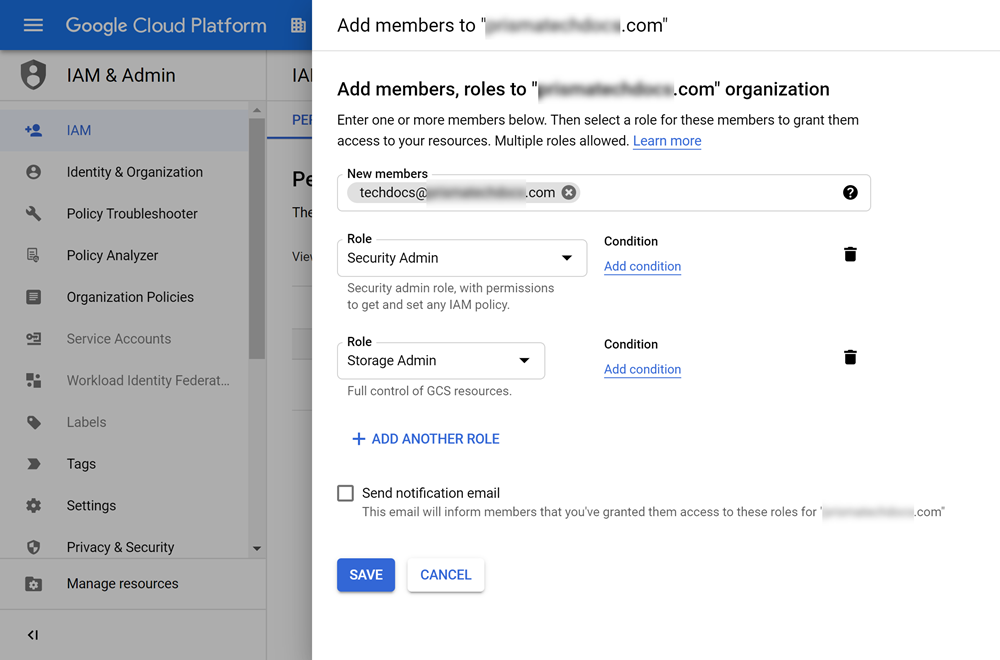
- Select IAM & AdminIAM, then + ADD.
- Add your account as Security Admin and Storage Admin.

- Enable API client access to Google Cloud Storage.
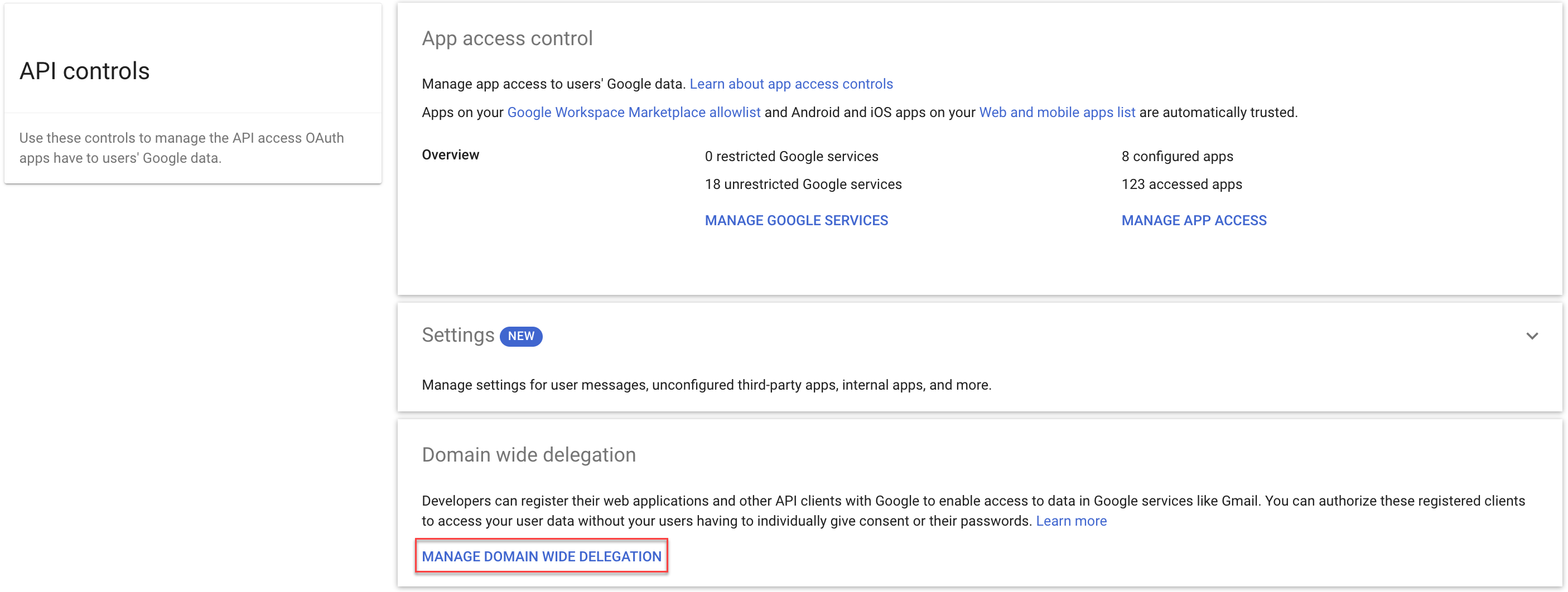
- Log in to Google Admin Console as the Google Cloud Storage administrator.The admin console isn't the same as the cloud console that you’ve been accessing up to this point in this procedure; rather, the admin console is a different console.
- Select SecurityApp access control (API Controls)Domain wide DelegationMANAGE DOMAIN WIDE DELEGATION.Trust internal, domain-owned apps isn't needed for onboarding the Google Cloud Storage app; however, GCP web interface enables this setting by default. You can safely disable this setting if you want.

- Click Add new, then specify Client ID and required scopes.
- In Client Name, specify the Client
ID that you recorded in 7.
- In One or More API S copes, copy and
paste the following scope, then AUTHORIZE access
to data in Google services.https://www.googleapis.com/auth/admin.directory.user.security,https://www.googleapis.com/auth/cloud-platform,https://www.googleapis.com/auth/devstorage.read_write,https://www.googleapis.com/auth/admin.directory.group
- In Client Name, specify the Client
ID that you recorded in
- Proceed toAdd Google Cloud Storage App
Use an Existing Project and Service Account
If you want to onboard the Google Cloud Storage app using an existing GCP project and service
account, set up your admin account as the project IAM owner and service account
owner. If you don’t have an existing project or service account,
Create a Service Account for Google Cloud Storage
instead.- Log in to Google Cloud Console as Super Admin.
- Set permissions for the existing project.
- In the drop-down at the top of the screen, open your project list, then select your existing project.
- Select IAM & AdminIAM.
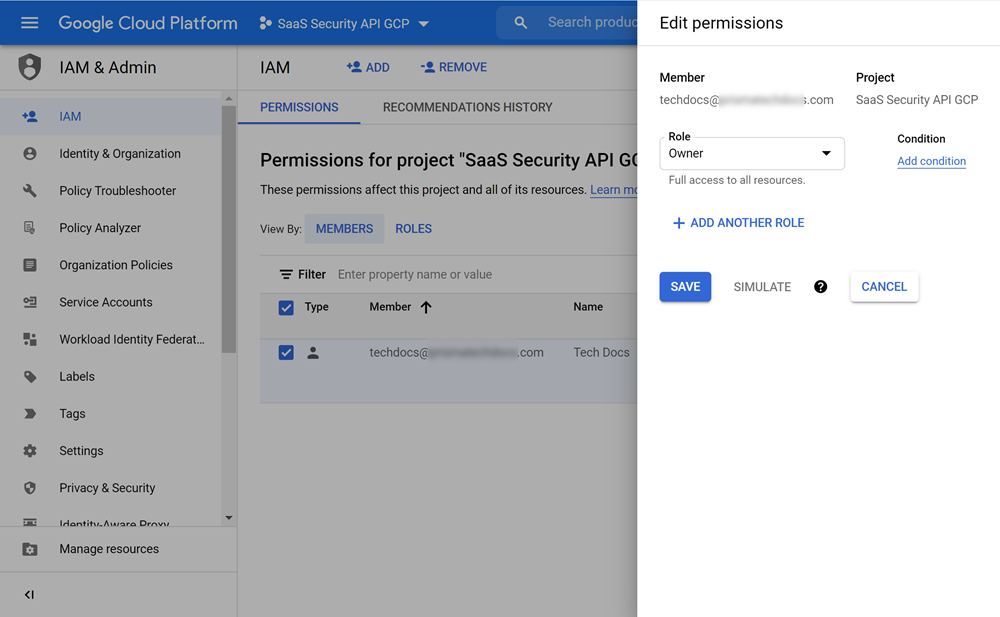
- In PERMISSIONSMembers, locate and Edit your membership, which is your admin account.If you can't quickly locate your admin account in the Members table, click + ADD to use the New members search tool.
- Set Role to Owner.

- Set permissions for the existing service account.
- Select IAM & AdminService Accounts.
- Click on your service account, then PERMISSIONS.
- In Members table, locate and Edit your membership, which is your admin account.If you can't quickly locate your admin account in the Members table, click + GRANT ACCESS to use the New members search tool.
- Set Role to Owner.
- Verify that the Oauth Consent settings outlined in3are correct.
- Proceed toAdd Google Cloud Storage App.
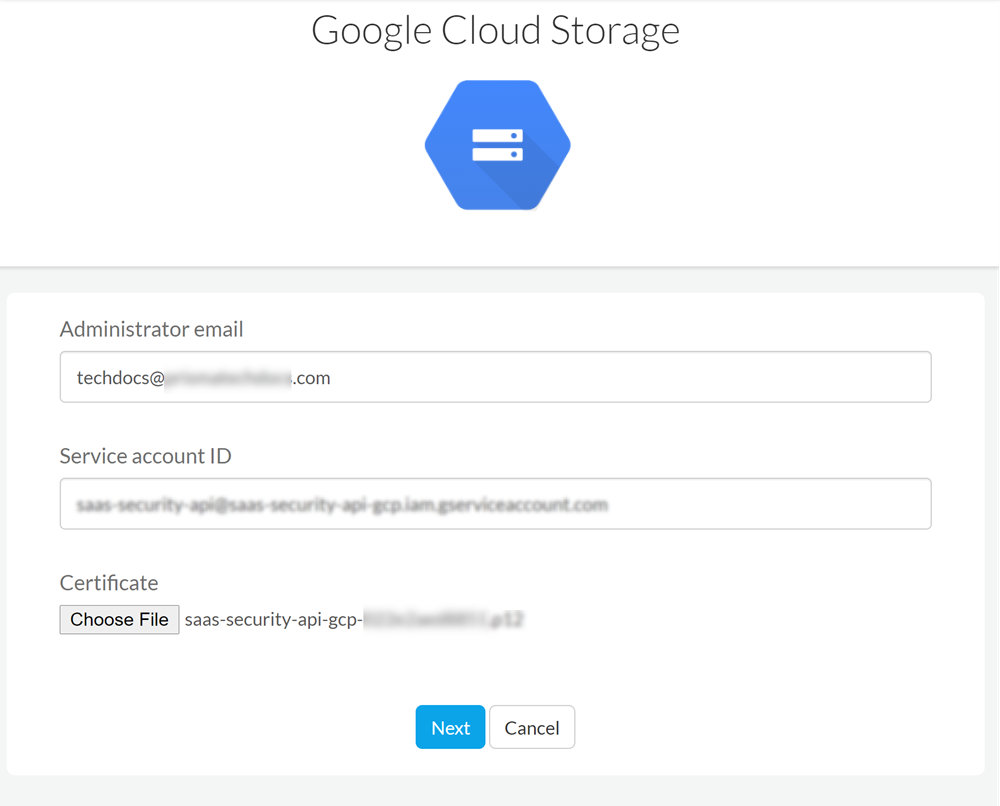
Add Google Cloud Storage App
Before you add the Google Cloud Storage app,
you must
Create a Service Account for Google Cloud Storage
.- Log in to Strata Cloud Manager and select Data SecurityApplicationsAdd ApplicationGoogle Cloud Storage.

- Select Google Cloud Storage and then Connect to Account.
- Enter the Google Administrator email to which you granted roles in9.d.
- Enter Service account ID that you created in4.b.
- Upload P12 Certificate GCP issued in5.e.
- Click Next to add the cloud app.

- Review the initial project scan discoveries and select the projects to monitor.If you Cancel the setup at any time, you must start over again.
- Enable Automatically scan new projects to scan all new projects.
- To select individual projects, select the Project to scan from the list.
- Save your scan setting to proceed scanning all discovered projects.
- Cancel if you don't want to proceed with scanning the discovered projects.
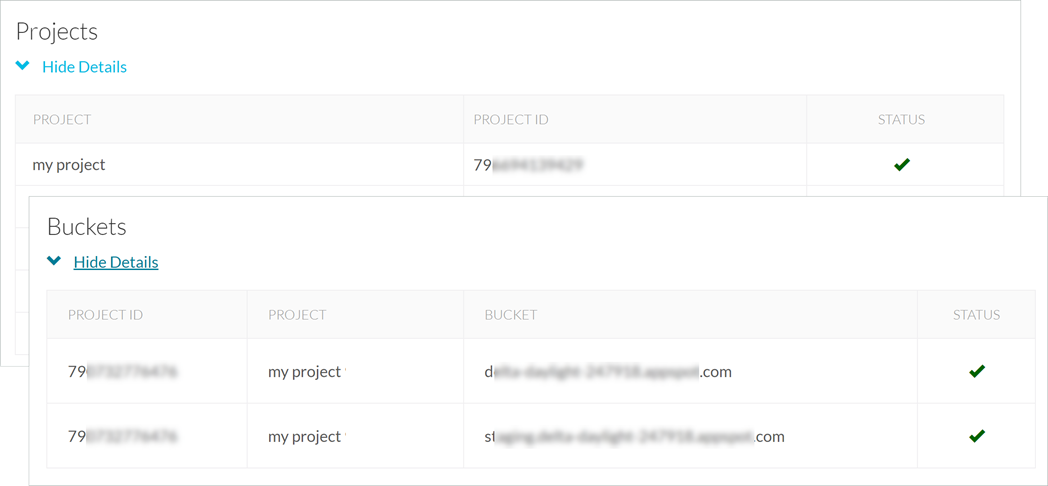
- Review the initial bucket scan discoveries and select the buckets to monitor.
- Enable Scan all current and any new buckets to scan all new buckets.
- To select individual buckets, select the Bucket to scan from the list.
- Save your scan setting to proceed scanning all discovered buckets.
- Cancel if you don't want to proceed with scanning the discovered buckets.After authentication, Data Security adds the new Google Cloud Storage app to the Cloud Apps list as Google Cloud Storage n, where n is the number of Google Cloud Storage app instances that you have connected to Data Security. For example, if you added one Google Cloud Storage app, the name displays as Google Cloud Storage 1. You’llspecify a descriptive namesoon.From this point forward, keep this project exclusively for Data Security. Don't revoke, disable authorization, or change the project in any way. If you do, Data Security stops scanning.
- Proceed toIdentify Risks.
Identify Risks
Select the projects and buckets that you want
Data Security to monitor.
When you add a new cloud app
and enable scanning,
Data Security automatically scans the cloud app against the
default data patterns and displays the match occurrences. You can
take action now to improve your scan results and identify risks.
- Start scanning the new Google Cloud Storage app for risks.
- Monitor the scan results.During the discovery phase, Data Security scans files and matches them against enabled default policy rules.Verify that your default policy rules are effective. If the results don’t capture all risks or you see false positives, proceed to the next step.
- (Optional) Add new policy rules.Consider the business use of your app, then identify risks unique to your enterprise. As necessary, add new:
- (Optional) Configure or edit a data pattern.You can Configure Data Patterns to identify specific strings of text, characters, words, or patterns to make it possible to find all instances of text that match a data pattern you specify.
- Proceed toView Scan Settings for Project and Buckets.
View Scan Settings for Project and Buckets
When you added the cloud app, you configured
the projects and buckets you want Data Security to monitor.
You can view the scan settings for the Projects and Buckets that
are currently being scanned.
- Log in to SaaS Security.
- Select SettingsCloud App and Scan Settings.
- Select a Google Cloud Storage app from the list of Cloud Apps and expand the Projects Buckets to view the scan details.

- Proceed toCustomize Google Cloud Storage AppandFix Google Cloud Storage Onboarding Issues, if necessary.
Customize Google Cloud Storage App
If you plan to manage more than one instance
of Google Cloud Storage app, consider differentiating your instances.
- (Optional) Give a descriptive name to this app instance.
- Select the Google Storage n link on the Cloud Apps list.
- Enter a descriptive Name.
- Click Done to save your changes.
- Proceed toFix Google Cloud Storage Onboarding Issues.
Fix Google Cloud Storage Onboarding Issues
The most common issues related to onboarding the Google
Cloud Storage app are as follows:
Symptom | Explanation | Solution |
|---|---|---|
There are no known issues. | ||