SaaS Security
Assess Meeting Security
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Assess Meeting Security
Open the Meetings page in SSPM to view the meeting bots that SSPM detected in
meetings hosed by Zoom and Microsoft Teams. Use the information to identify risky bots and
take action.
Meeting bots are powerful tools that can significantly enhance virtual
collaborations. They excel at real-time transcription, creating accurate records of
discussions as they happen. They can automate note-taking, generate concise
summaries, and create lists of follow-up actions. By handling these tasks, they
enable participants to focus more on the content of the meeting, leading to more
productive and engaging discussions. Some meeting bots provide meeting analytics,
such as metrics on each participant's contribution and the emotional tone of
conversations.
Although meeting bots can improve meeting efficiency, they also pose significant
risks to organizational security and privacy. They can join meetings undetected,
potentially recording sensitive conversations without consent, leading to data
breaches and confidentiality violations. Users can add meeting bots to calendars,
which enables the bots to join meetings automatically and to get meeting schedules,
participants, and topics. This ability could also expose proprietary data to
unauthorized parties.
To help you address the threats posed by meeting bots, the Meetings page in SSPM
gives you visibility into the meeting bots that accessed meetings in the following
virtual meeting platforms:
- Zoom
- Microsoft Teams
SSPM also detects the users who have synced meeting bots to their calendar (Google
Calendar or Outlook) to automatically join meetings.
Prerequisites: To enable SSPM to scan these meeting platforms and calendar
applications for meeting bots, you onboard the Zoom, Office 365, and Google
Workspace apps to SSPM.
- Onboarding Zoom enables SSPM to detect bots in Zoom meetings.
- Onboarding Office 365 enables SSPM to detect bots in Microsoft Teams meetings, and also enables SSPM to access Microsoft Outlook calendars to detect which users have synced meeting bots to their Microsoft Outlook calendar.
- Onboarding Google Workspace enables SSPM to detect which users have synced meeting bots to their Google calendar.
If you onboarded these apps to SSPM before SSPM introduced
this meeting bot detection feature, you must re-onboard them to enable meeting bot
detection.
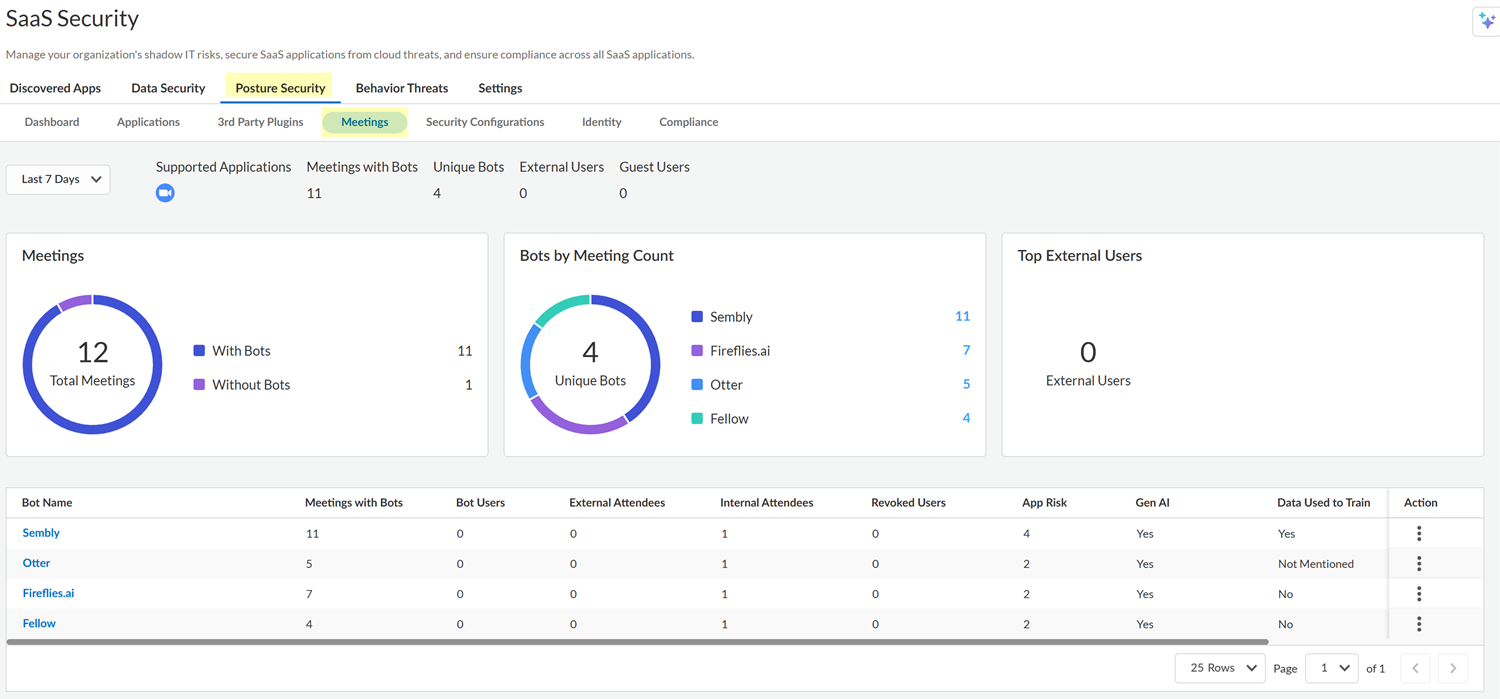
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityMeetings.The Meetings page displays information about the meetings in which bots were present and also displays information about bot users. Bot users are the users who have synced a meeting bot to their calendars, which enables the bot to join the user's calendar meetings automatically.
![]() The information that the Meetings page displays depends on which apps (Zoom, Office 365, or Google Workspace) you onboarded to SSPM and when you onboarded them. After you onboard one or more of these apps, SSPM will scan your app instances at regular intervals for a set of predefined meeting bots. If you onboarded Office 365 or Google Workspace, SSPM will scan users' calendar histories to detect which users have added meeting bots to their calendar. Initially, the Meetings page shows only information about users who have added bots to their calendar. SSPM will display information about bots that were present in meetings only after new meetings are held, and SSPM runs its meeting scans.Inspect the information displayed in the upper section of the dashboard for a high-level summary of bot usage on your tenant.This information includes the following information:
The information that the Meetings page displays depends on which apps (Zoom, Office 365, or Google Workspace) you onboarded to SSPM and when you onboarded them. After you onboard one or more of these apps, SSPM will scan your app instances at regular intervals for a set of predefined meeting bots. If you onboarded Office 365 or Google Workspace, SSPM will scan users' calendar histories to detect which users have added meeting bots to their calendar. Initially, the Meetings page shows only information about users who have added bots to their calendar. SSPM will display information about bots that were present in meetings only after new meetings are held, and SSPM runs its meeting scans.Inspect the information displayed in the upper section of the dashboard for a high-level summary of bot usage on your tenant.This information includes the following information:- The Supported Applications, which are the meeting platforms that SSPM is periodically scanning for meetings with bots and for bot users. The Meetings page displays information only for these meeting platforms.
- The number of Meetings with Bots present. A bot might be present because the bot has joined automatically from a bot user's calendar, or because a meeting participant added it to the live meeting. For bots that joined from an internal bot user's calendar, SSPM can detect the bot user. SSPM can't detect a user who added a bot to a live meeting, or if an external user or guest user added the bot.
- The number of Unique Bots that SSPM detected across all meetings.
- The number of External Users, which are users outside of your organization that the meeting organizer included in the meeting invite list. These users might be bot users, but because they are outside of your meeting platform's tenant, the Meetings page won’t include them in the statistics for bot users. You can compare the External Users by Meetings with Bots Present, to the Meetings with Bots for an indication of whether external users are inviting bots to meetings more frequently than internal users are inviting bots. However, the fact that an external user was present in the same meeting as a bot does not necessarily mean that an external user added the bot.
- The number of Guest Users, which are users who accessed the meeting through a meeting link. For example, a meeting invitee might have provided the guest with the meeting link. Because the guest is accessing the meeting through a meeting link, the meeting organizer probably did not explicitly include them in the meeting invite list. Because the meeting organizer did not invite the guests through the calendar application, SSPM can’t identify the guest user's email address.
In the table in the lower section of the Meeetings page, view the statistics for individual meeting bots.Along with statistics for Meetings with Bots, Bot Users, External Attendees, and Internal Attendees, the table shows an App Risk score, which Palo Alto Networks has calculated from various attributes of the meeting bot application. The App Risk score is within a range of 1-5, with 1 representing the lowest risk and 5 representing the greatest risk.For more information about a particular meeting bot, click its name in the Bot Name column.A flyout window displays a description of the meeting bot, the meetings in which the bot was present, and the bot users.Take action on bots that might be a risk to your organization.If you have determined that you don’t want to allow a particular meeting bot in your organization, you can revoke the bot's access to calendar applications. Revoking access will prevent the bot from joining meetings automatically from the calendars of all bot users.If you linked SSPM to an issue tracking system, you can, instead of revoking the bot, create a ticket to investigate the bot usage further. For example, you could open a ticket to get more information from the bot users.