Prisma SD-WAN
Enable IoT Device ID in Prisma SD-WAN
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
- Prisma SD-WAN Controller
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.1
- 5.6
- Prisma SD-WAN Controller
- Prisma SD-WAN On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Enable IoT Device ID in Prisma SD-WAN
Learn how to enable IoT Device Visibility in Prisma SD-WAN. It also lists
details such as IP address, MAC address, vendor details, and so on, for greater
visibility.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma SD-WAN with Strata Cloud Manager supports IoT device visibility to identify devices in your
network. Prisma SD-WAN branch ION devices inspect packets, extract
information, and generate messages to send to Strata Logging Service in a
specific format.
IoT Security obtains this information
from Strata Logging Service and lists all the devices discovered in its
portal. It also lists details such as IP address, MAC address, vendor details, and
so on, for greater visibility. Device Security must have visibility into network
traffic to discover, identify, and monitor the network behaviors of devices.

When integrating IoT Security with Prisma
Access, Device Security relies on the Traffic logs that Prisma Access provides to analyze traffic at the branch sites that Prisma Access serves. Although Prisma Access can log outbound and inbound
traffic from the sites it protects, it can't log traffic that never reaches it; that
is, the traffic between devices at the same branch site.
Of
particular importance to Device Security is network traffic with services such as
DHCP and ARP that link an IP address assigned to a device with its MAC address. In
an environment where devices are assigned IP addresses dynamically through DHCP,
it's difficult to use IP addresses alone to track the network activity of devices
because they can each have multiple IP addresses over a period of time. By having
visibility into DHCP traffic, Device Security can update the IP address of a
device when it changes. Similarly, by having visibility into ARP traffic (gratuitous
ARP announcements, for example),Device Security can track how IP addresses
correspond to device MAC addresses.
Once Device Security has an IP
address-to-device mapping, it can use its AI and machine learning engines to monitor
and analyze the network activities of the device over time. It can form a baseline
of the normal device network behaviors, determine its identity, inform you of any
known vulnerabilities, and detect anomalous network behaviors indicating risk.
When a DHCP server is at a branch site, DHCP traffic will never reach Prisma Access. Neither will ARP traffic, which only occurs within a Layer 2
broadcast domain. But, it's possible for ION devices at branch sites to see DHCP
traffic. If they’re in the same Layer 2 broadcast domain, then the branch ION
devices can also see the ARP traffic that devices generate. When integrated with Device Security, Prisma SD-WAN ION devices log this traffic and
forward their logs to Strata Logging Service where Device Security
accesses them for analysis.
To support IoT device visibility in Prisma SD-WAN, you need the following licenses and subscriptions in
the same tenant service group (TSG) that Prisma SD-WAN belongs to:
Device Security depends on the information extracted
from the IoT device traffic, such as DHCP & ARP, for device classification and
risk assessment. Prior to Release 6.3.1, users adopting Device Security lacked
visibility into the traffic generated by IoT devices that was local to the branch,
or traveled via WAN links outside of Prisma Access. This limited the scope of
visibility to directly connected devices or to packets that traversed the Prisma SD-WAN branch ION device.
Starting with Release 6.3.1, Prisma SD-WAN supports the discovery of
devices not directly connected to the Prisma SD-WAN branch ION
devices. The system uses SNMP (Simple Network Management Protocol) with LLDP (Link
Layer Discovery Protocol) to discover IoT devices within a branch network.
Prisma SD-WAN does not support Cisco Discovery Protocol (CDP) to
discover devices.
With LLDP, each IoT device transmits its device
information to its neighboring networking devices (such as switches and routers).
This information is available in the Management Information databases (MIBs). The
ION device launches an SNMP MIB (management information base) query to retrieve the
IP address and MAC address entries of the IoT devices.
The ION device then retrieves the LLDP neighbors of the
neighboring devices, one at time to get their IP or MAC address bindings. This
process of recursively discovering the devices known as “crawling” continues until
the ION device discovers all its neighbors.
The ION device sends the discovered IP or MAC address bindings (along with
information such as VLAN, subnets, and so on) as part of the Enhanced Application
logs (EAL) to Strata Logging Service. Device Security consumes these logs
and provides visibility in the Device Security portal.
You might need to modify security in the IoT devices to
allow SNMP from a new source.
The following steps explain how to onboard Device Security and Prisma SD-WAN to Prisma Access as add-ons and how Prisma SD-WAN ION devices extend Device Security visibility into
their branch sites.
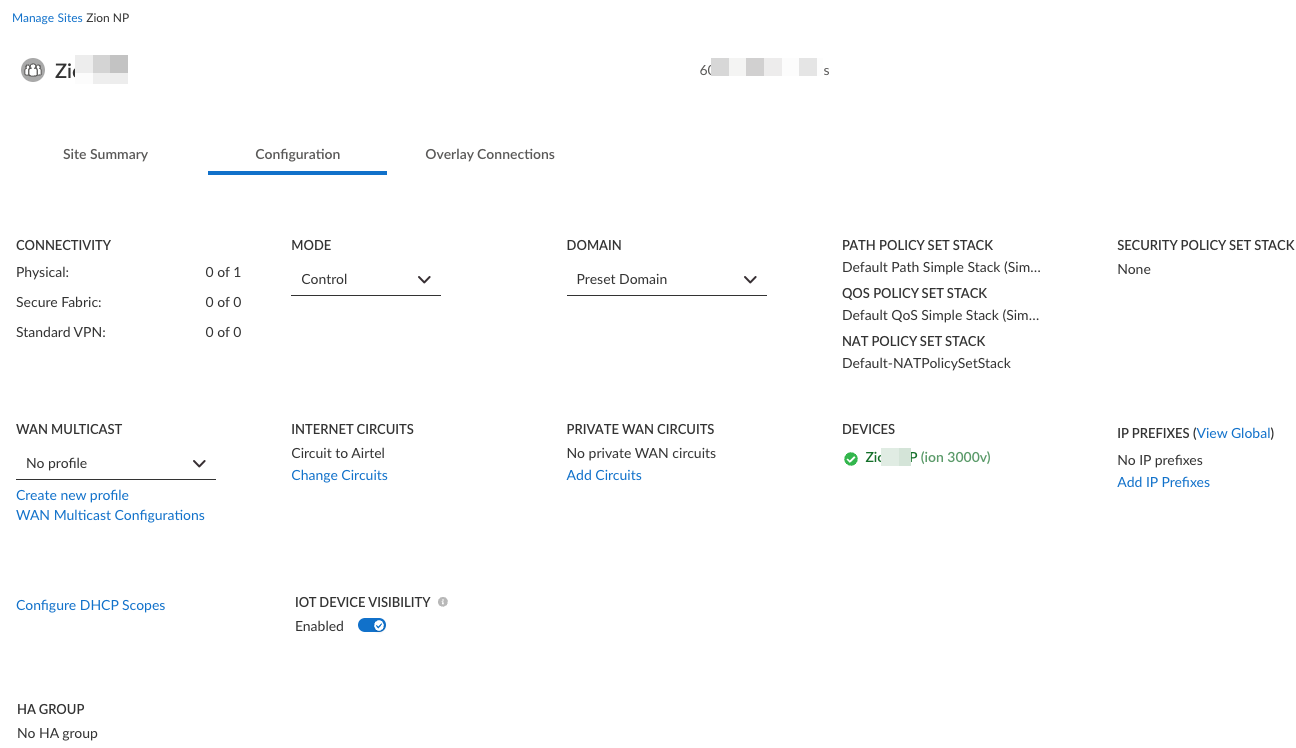
- Add Device Security and Prisma SD-WAN as Prisma Access add-ons.Follow the steps in Activate a License for Panorama-Managed , and ensure to include Device Security and Prisma SD-WAN as add-ons. You can onboard them together or at different times.When you onboard and enable both Device Security and Prisma SD-WAN to a Prisma Access (Managed by Panorama) account, the Prisma SD-WAN Controller automatically enables IoT device visibility on ION devices at all branch sites that belong to the corresponding tenant service group (TSG). The Prisma SD-WAN Controller learns the ID and FQDN of the Strata Logging Service instance in its TSG and automatically gets the device certificate and distributes it to ION devices to use when authenticating themselves to Strata Logging Service. The controller then instructs the ION devices to log the DHCP and ARP traffic they detect on their networks and forward their logs to Strata Logging Service.ION devices send ARP Traffic logs by default but you must configure them as either a DHCP relay agent or DHCP server to send DHCP Traffic logs to Strata Logging Service.Device Security accesses the log data in Strata Logging Service and uses machine learning algorithms to analyze it. Through its analysis, Device Security discovers and identifies devices on the network and deduces their usual network behaviors. Device Security generates alerts when there is anomalous network activity and detects device vulnerabilities and potential threats. You can view the results of its analysis in the IoT Security portal.(Optional) Control the sites that can forward logs to the Strata Logging Service from the Prisma SD-WAN web interface.When a TSG for Prisma Access includes both Device Security and Prisma SD-WAN add-ons, it Prisma SD-WAN enables Device Security visibility by default on the ION devices at all the branch sites.However, if you want to disable it on a particular site, pre-logon to Prisma SD-WAN, select ConfigurationPrisma SD-WANBranch Sites, select the site, and toggle IoT Device Visibility off. This disables IoT Device Visibility on all ION devices at that site.
![]() View device information learned from Prisma SD-WAN sites in the Device Security portal.
View device information learned from Prisma SD-WAN sites in the Device Security portal.- Navigate to the IoT Security portal and select the Devices tab to view device details.
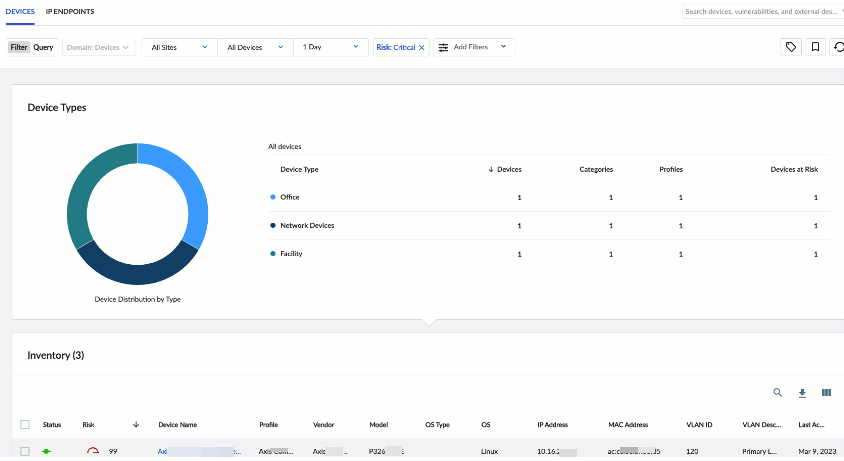
![]() After Device Security receives data in Traffic logs from Prisma SD-WAN ION devices and starts discovering and identifying network-connected devices at branch sites, it displays its findings in the Inventory table on the Devices page in the Device Security portal. For each device thatDevice Security learned from Prisma SD-WAN, it displays various device attributes such as its IP and MAC address, device category, vendor, model, and OS as well as several identifying attributes of the ION devices that provided the logs such as:
After Device Security receives data in Traffic logs from Prisma SD-WAN ION devices and starts discovering and identifying network-connected devices at branch sites, it displays its findings in the Inventory table on the Devices page in the Device Security portal. For each device thatDevice Security learned from Prisma SD-WAN, it displays various device attributes such as its IP and MAC address, device category, vendor, model, and OS as well as several identifying attributes of the ION devices that provided the logs such as:- Prisma SD-WAN site name
- Prisma SD-WAN device name
- Prisma SD-WAN interface name
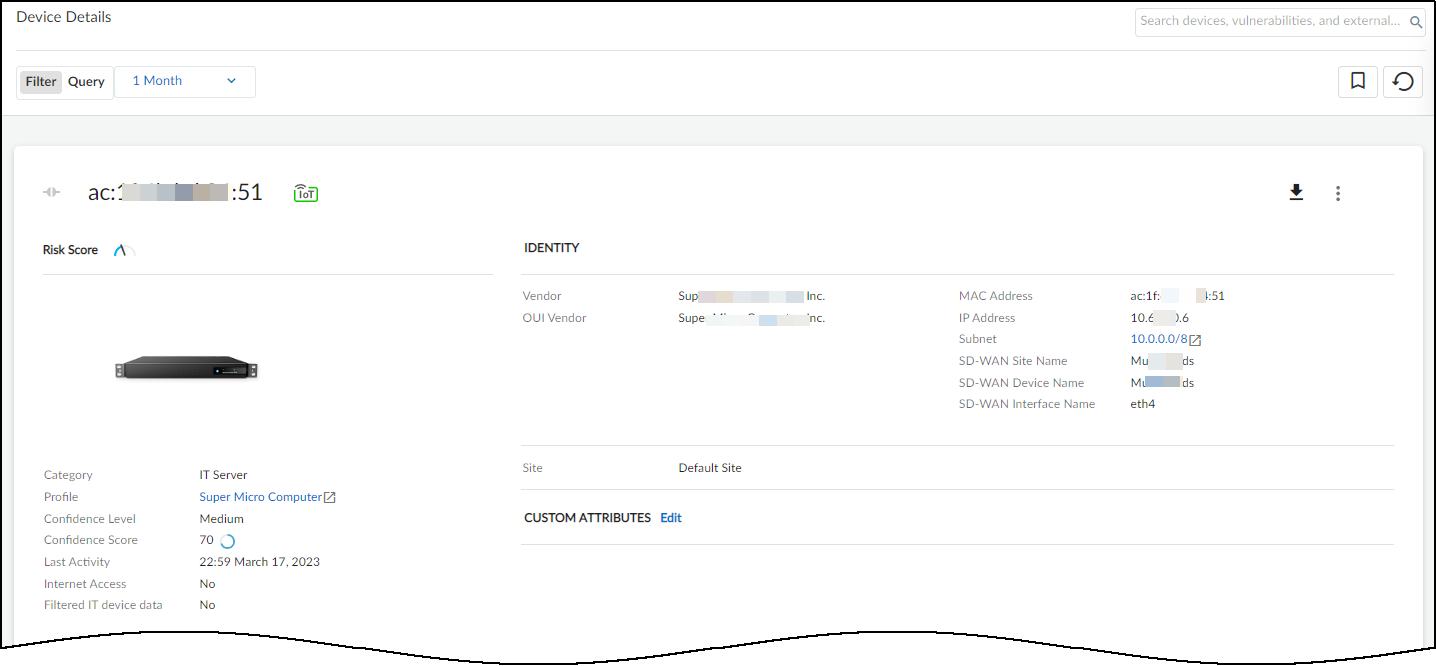
![]() (Optional) Click a device to view details such as Prisma SD-WAN site, device, and interface names.Device Enforcement
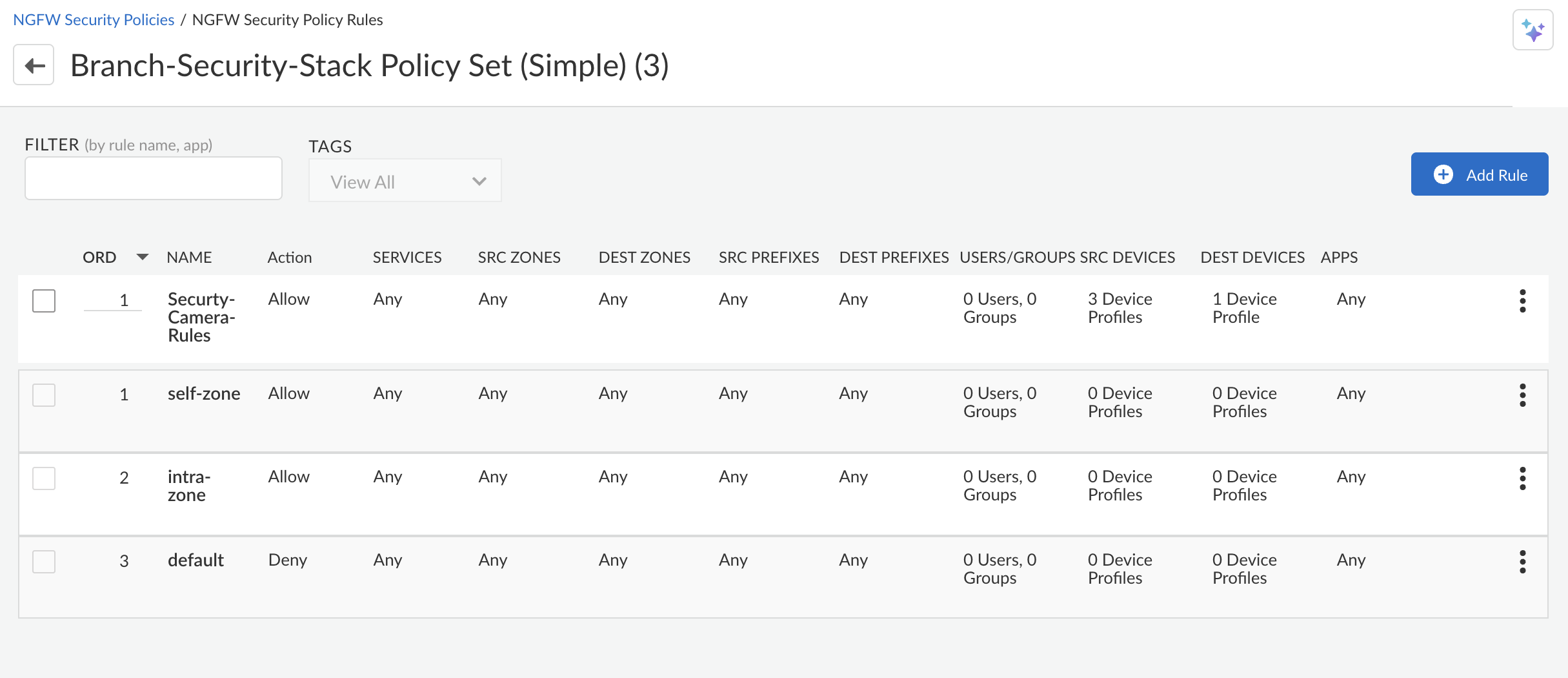
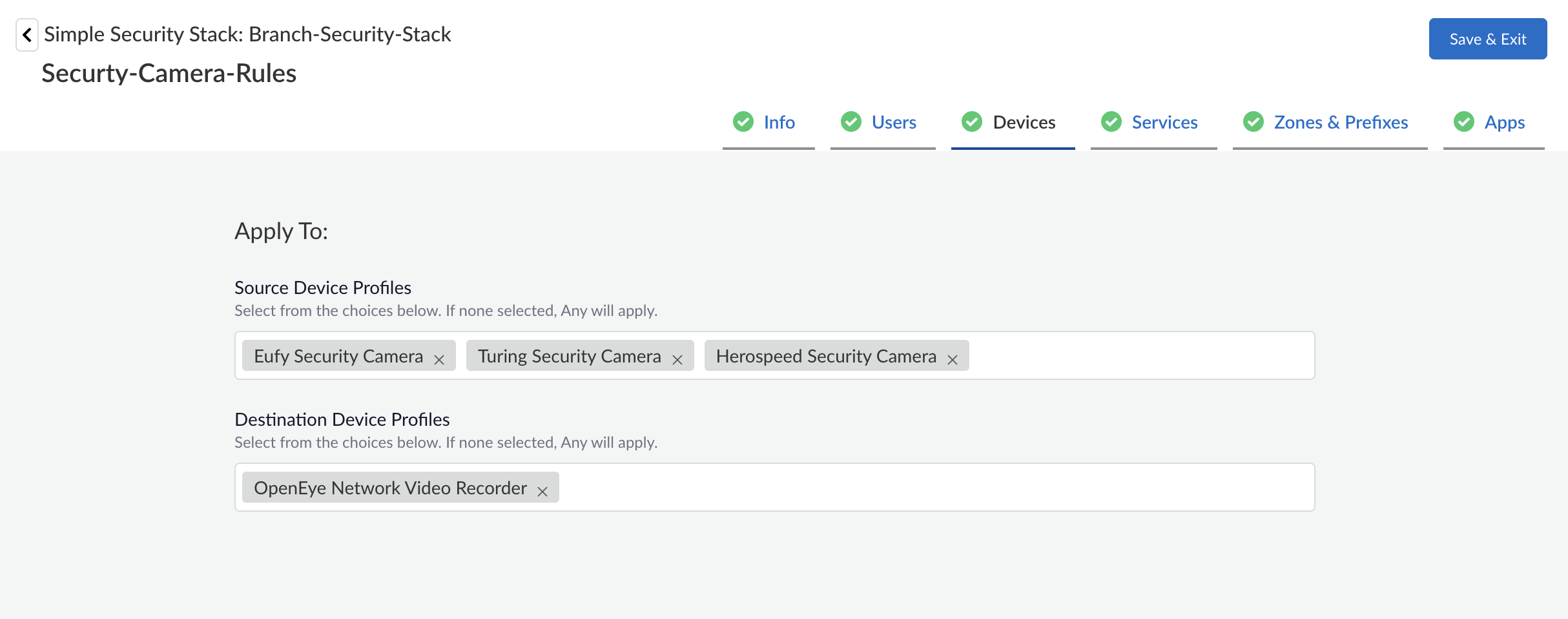
(Optional) Click a device to view details such as Prisma SD-WAN site, device, and interface names.Device Enforcement![]() Branch security is essential and implementing Device-ID-based policies play a key role in strengthening our defenses. By integrating these policies with App-ID and User-ID, we create a comprehensive security framework that effectively protects against threats. Earlier, with the PA/SASE license, Prisma SD-WAN customers could get enhanced visibility into OT, IoT, and endpoint devices at their branches. Now, these device-based IDs can be seamlessly incorporated into security policies, enabling enforcement based on specific device categories or IDs. This advancement delivers unparalleled security and granular control over path selection.Apply the security policy to the source and the destination device profiles.
Branch security is essential and implementing Device-ID-based policies play a key role in strengthening our defenses. By integrating these policies with App-ID and User-ID, we create a comprehensive security framework that effectively protects against threats. Earlier, with the PA/SASE license, Prisma SD-WAN customers could get enhanced visibility into OT, IoT, and endpoint devices at their branches. Now, these device-based IDs can be seamlessly incorporated into security policies, enabling enforcement based on specific device categories or IDs. This advancement delivers unparalleled security and granular control over path selection.Apply the security policy to the source and the destination device profiles.![]()
![]()
Related CLIs