Strata Cloud Manager
Configuration: IoT Policy Recommendation
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
Configuration: IoT Policy Recommendation
Create Security policy rules from automatically generated rule recommendations for
next-generation firewalls or Prisma Access to enforce.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
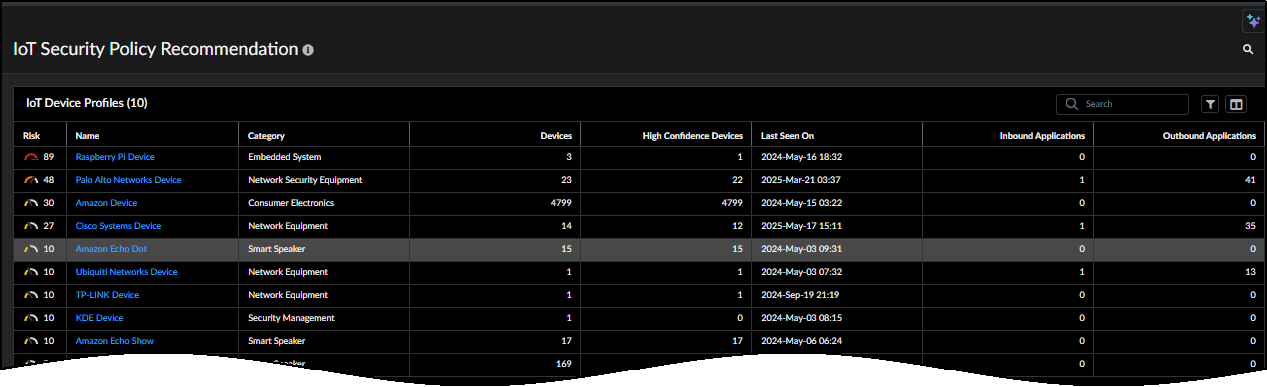
IoT Security provides Strata Cloud Manager with automatically generated Security policy rule recommendations
organized by device profile. There is one recommendation per application per
profile. Choose a profile, select the rule recommendations you want to use, and then
the next-generation firewalls or Prisma Access deployment types
where you want to enforce them.
Get Started
Select Security policy rule recommendations and apply them to next-generation
firewalls or Prisma Access.
- Create folders or snippets for next-generation firewalls.Skip this step if you want to use predefined folders or previously created folders or snippets. Prisma Access folders are predefined.Folders are essentially containers that hold various kinds of rules, security configurations, and objects. For importing the policy rule recommendations that Device Security generated, the folders would hold next-generation firewalls or Prisma Access deployments.Snippets are also a type of container that can be associated with multiple folders. With folders and snippets, you can import policy rules into whichever groups of firewalls or deployments you want.For example, you might create a folder named California and put 60 firewalls in it and then create another folder named Hawaii and put 15 firewalls in that. You then create a snippet called CA-HI and apply it to the California and Hawaii folders. When you want to import rule recommendations only to firewalls in California, you set the scope as Folder and select the California folder. If you want to import the rule recommendations to both California and Hawaii, set the scope as Snippet and select the CA-HI snippet.Depending on the hierarchy of the folder structure, we might have a parent folder like US-West above California and Hawaii. Then if you import rule recommendations while the scope is set as Folder with US-West selected, then both of the children folders California and Hawaii would inherit the imported rules. However, this wouldn't work if you only wanted to import rules to California and Hawaii if they had sibling folders like Oregon, Alaska, Washington, and Arizona under the US-West folder. Then you'd have to use the CA-HI snippet.Create Security policy rules.
- Select ConfigurationIoT Policy Recommendation.
- Select a profile name.Device Security uses machine learning to automatically generate Security policy rule recommendations based on the normal, acceptable network behaviors of IoT devices in the same device profile. Strata Cloud Manager displays a list of these recommendations organized by application. For each behavior, you can see the following:
Behavior Component Explanation App RiskThis is the level of risk that’s inherent in an application as determined by various factors on a scale of increasing risk from 1 to 5.Security Policy CreatedWhen one or more names of folders or snippets appear here, it indicates a Security policy rule was previously created for this behavior. Clicking one of them opens a side panel with the names of the profile, application, and folder or snippet, and the policy rule action. When No appears here, it indicates a rule has not yet been created.Discovered LocationInternal indicates that the destination is on the local network. External indicates that the destination is outside the local network.Locally ObservedYes indicates the behavior was observed in your IoT Security tenant environment. No indicates it was observed in multiple IoT Security tenant environments but not in yours.App UsageCommon indicates that an application has been detected in multiple IoT Security tenant environments. Unique indicates that it has been observed in your environment but not in those of other tenants that also have devices in the same profile.Destination Address & FQDNThis is the destination for a recommended policy rule. It can be Any, an IP address, or an FQDN.Destination ProfileA profile is shown when the destination is internal and the device profile of the destination is identified.Last SeenFor locally observed behaviors, this is the timestamp when it was last observed. For common behaviors not observed locally, a dash is shown. - Select one or more behaviors and then Create Security Policy.
- Review the Security policy rules that will be created and then select the config scope for where Strata Cloud Manager will apply them.To apply the rules to one or more next-generation firewalls or Prisma Access deployments in a folder, select Folders and then choose the folder from Scope Selection.To apply the rules to one or more next-generation firewalls or Prisma Access deployments in a snippet, select Snippets and then choose the snippet from Scope Selection.
- Create Security Policy.
Push the configuration to next-generation firewalls and Prisma Access deployments.- Select OperationsPush Config.
- Select the folders with the configuration changes, Push Config, Push, and then Push again.Strata Cloud Manager displays an ID number in the Job ID column for the selected folders and the status of the configuration push in the Push Status column.When the Push Status changes from Pending to Success, you know the pushed configuration has started running.
- To see the status of a push job, select OperationsPush Status. There you can see the status of the parent job and also the status of the children jobs, one for each firewall or deployment.
