Download PDF
GlobalProtect
Configure an Always On VPN Configuration for iOS Endpoints Using Workspace ONE
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
-
-
-
- 6.3
- 6.2
- 6.1
- 6.0
-
- 6.3
- 6.2
- 6.1
- 6.0
Configure an Always On VPN Configuration for iOS Endpoints Using Workspace ONE
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
In an Always On VPN configuration, the secure
GlobalProtect connection is always on. Traffic that matches specific
filters (such as port and IP address) configured on the GlobalProtect
gateway is always routed through the VPN tunnel.
Use the following steps to configure an Always On VPN configuration for iOS endpoints using
Workspace ONE:
- Download the GlobalProtect app for iOS.
- Download the GlobalProtect app directly from the App Store.
The GlobalProtect app for iOS is also available in the Apple App Store in China.From the Workspace ONE console, modify an existing Apple iOS profile or add a new one.- Select ResourcesProfiles & BaselinesProfilesADD, and then Add Profile.Select iOS from the platform list.
![]() Select Device Profile from the Select Context window.Configure the General settings:
Select Device Profile from the Select Context window.Configure the General settings:- Enter a Name for the profile.
- (Optional) Enter a brief Description of the profile that indicates its purpose.
- (Optional) Select the Deployment method, which indicates whether the profile will be removed automatically upon unenrollment—either Managed (the profile is removed) or Manual (the profile remains installed until it is removed by the end user).
- (Optional) Select an Assignment Type to determine how the profile is deployed to endpoints. Select Auto to deploy the profile to all endpoints automatically, Optional to enable the end user to install the profile from the Self-Service Portal (SSP) or to manually deploy the profile to individual endpoints, or Compliance to deploy the profile when an end user violates a compliance policy applicable to the endpoint.
- (Optional) Select whether or not you want to Allow Removal of the profile by the end user. Select Always to enable the end user to manually remove the profile at any time, Never to prevent the end user from removing the profile, or With Authorization to enable the end user to remove the profile with the authorization of the administrator. Choosing With Authorization adds a required Password.
- (Optional) In the Managed By field, enter the Organization Group with administrative access to the profile.
- (Optional) In the Assigned Groups field, add the Smart Groups to which you want the profile added. This field includes an option to create a new Smart Group, which can be configured with specs for minimum OS, device models, ownership categories, organization groups, and more.
- (Optional) Indicate whether you want to include any Exclusions to the assignment of this profile. If you select Yes, the Excluded Groups field displays, enabling you to select the Smart Groups that you wish to exclude from the assignment of this profile.
- (Optional) If you enable the option to Install only on devices inside selected areas, the profile can be installed only on endpoints in specified geofence or iBeacon regions. When prompted, add the geofence or iBeacon regions in the Assigned Geofence Areas field.
- (Optional) If you Enable Scheduling and install only during selected time periods, you can apply a time schedule (DevicesProfiles & ResourcesProfiles SettingsTime Schedules) to the profile installation, which limits the periods of time during which the profile can be installed on endpoints. When prompted, enter the schedule name in the Assigned Schedules field.
- (Optional) Select the Removal Date on which you want the profile to be removed from all endpoints.
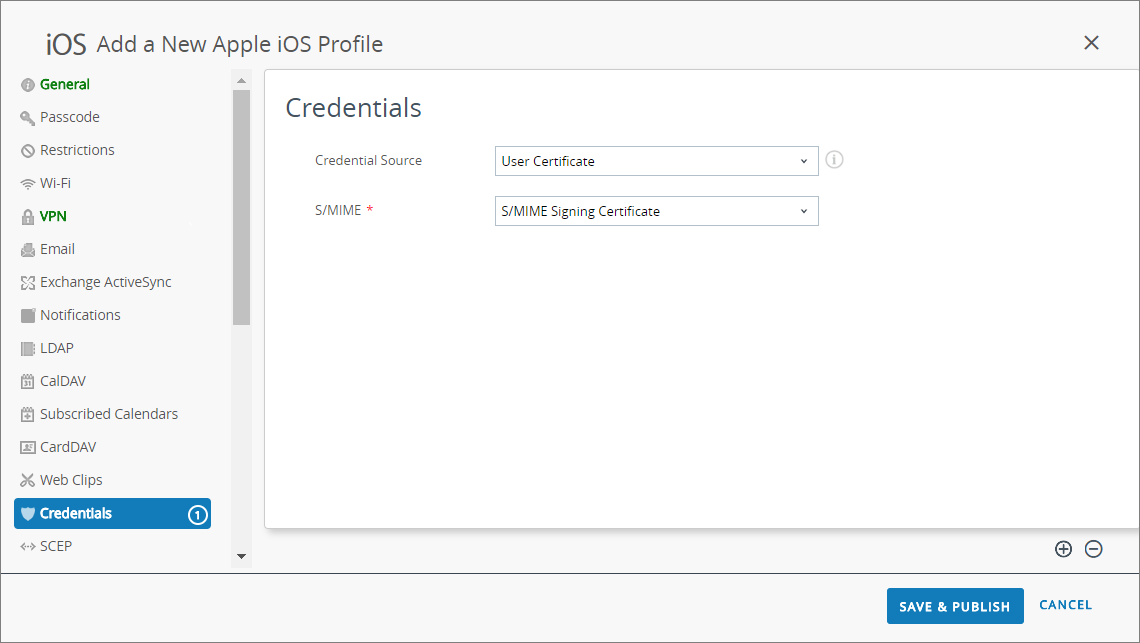
![]() (Optional) If your GlobalProtect deployment requires client certificate authentication, configure the Credentials settings:Starting with iOS 12, if you want to use client certificates for GlobalProtect client authentication, you must deploy the client certificates as part of the VPN profile that is pushed from the MDM server. If you deploy client certificates from the MDM server using any other method, the certificates cannot be used by the GlobalProtect app.
(Optional) If your GlobalProtect deployment requires client certificate authentication, configure the Credentials settings:Starting with iOS 12, if you want to use client certificates for GlobalProtect client authentication, you must deploy the client certificates as part of the VPN profile that is pushed from the MDM server. If you deploy client certificates from the MDM server using any other method, the certificates cannot be used by the GlobalProtect app.- To pull client certificates from Workspace ONE users:
- Set the Credential Source to User Certificate.
- Select the S/MIME Signing Certificate (default).
![]()
- To upload a client certificate manually:
- Set the Credential Source to Upload.
- Enter a Credential Name.
- Click UPLOAD to locate and select the certificate that you want to upload.
- After you select a certificate, click SAVE.
![]()
- To use a predefined certificate authority and template:
- Set the Credential Source to Defined Certificate Authority.
- Select the Certificate Authority from which you want obtain certificates.
- Select the Certificate Template for the certificate authority.
![]()
Configure the VPN settings:- Enter the Connection Name that the endpoint displays.Select the network Connection Type:
- For GlobalProtect app 4.1.x and earlier releases, select Palo Alto Networks GlobalProtect.
- For GlobalProtect app 5.0 and later releases, select Custom.
(Optional) If you set the Connection Type to Custom, enter the bundle ID (com.paloaltonetworks.globalprotect.vpn) in the Identifier field to identify the GlobalProtect app.If you downloaded the GlobalProtect app directly from the Apple App Store in China, enter the bundle ID (com.paloaltonetworks.globalprotect.vpncn) in the Identifier field.![]() In the Server field, enter the hostname or IP address of the GlobalProtect portal to which users connect.(Optional) Enter the username of the VPN Account or click the add (+) button to view supported lookup values that you can insert.(Optional) In the Disconnect on idle field, specify the amount of time (in seconds) at which an endpoint logs out of the GlobalProtect app after the app stops routing traffic through the VPN tunnel.In the Authentication area, select a user Authentication method: Password, Certificate, Password + Certificate.When prompted, enter a Password and/or select the Identity Certificate that GlobalProtect will use to authenticate users. The Identity Certificate is the same certificate that you configured in the Credentials settings.Enable VPN On Demand and Use new on demand keys .Configure an on-demand rule with Action: Connect.(Optional) Select the Proxy type and configure the relevant settings.(Optional) (starting with GlobalProtect app 5.0) If your GlobalProtect deployment requires HIP integration with MDM, specify the unique device identifier (UDID) attribute.GlobalProtect supports integration with MDM to obtain mobile device attributes from the MDM server for use in HIP-based policy enforcement. In order for the MDM integration to work, the GlobalProtect app must present the UDID of the endpoint to the GlobalProtect gateway. The UDID attribute enables the GlobalProtect app to retrieve and use UDID information in MDM-based deployments. If you remove the UDID attribute from the profile, you can no longer use the MDM integration. The GlobalProtect app generates a new UDID, but it cannot be used for the integration.
In the Server field, enter the hostname or IP address of the GlobalProtect portal to which users connect.(Optional) Enter the username of the VPN Account or click the add (+) button to view supported lookup values that you can insert.(Optional) In the Disconnect on idle field, specify the amount of time (in seconds) at which an endpoint logs out of the GlobalProtect app after the app stops routing traffic through the VPN tunnel.In the Authentication area, select a user Authentication method: Password, Certificate, Password + Certificate.When prompted, enter a Password and/or select the Identity Certificate that GlobalProtect will use to authenticate users. The Identity Certificate is the same certificate that you configured in the Credentials settings.Enable VPN On Demand and Use new on demand keys .Configure an on-demand rule with Action: Connect.(Optional) Select the Proxy type and configure the relevant settings.(Optional) (starting with GlobalProtect app 5.0) If your GlobalProtect deployment requires HIP integration with MDM, specify the unique device identifier (UDID) attribute.GlobalProtect supports integration with MDM to obtain mobile device attributes from the MDM server for use in HIP-based policy enforcement. In order for the MDM integration to work, the GlobalProtect app must present the UDID of the endpoint to the GlobalProtect gateway. The UDID attribute enables the GlobalProtect app to retrieve and use UDID information in MDM-based deployments. If you remove the UDID attribute from the profile, you can no longer use the MDM integration. The GlobalProtect app generates a new UDID, but it cannot be used for the integration.- If you are using the Palo Alto Networks GlobalProtect network Connection Type, go to the VPN settings and enable Vendor Keys in the Vendor Configurations area. Set the Key to mobile_id and the Value to {DeviceUid}.
![]()
- If you are using the Custom network Connection Type, go to the VPN settings and ADD Custom Data in the Connection Info area. Set the Key to mobile_id and the Value to {DeviceUid}.
![]()
SAVE & PUBLISH your changes.