Strata Cloud Manager
Configuration: Enterprise DLP
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
Configuration: Enterprise DLP
How to use Strata Cloud Manager to manageEnterprise Data Loss Prevention (E-DLP).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
Enterprise Data Loss Prevention (E-DLP) protects sensitive information against unauthorized access,
misuse, extraction, or sharing. Enterprise DLP on Strata Cloud Manager
enables you to enforce your organization’s data security standards and prevent the
loss of sensitive data across your NGFWs, and your Prisma Access mobile users and
remote networks.
Feature Highlights
- The Enterprise Data Loss Prevention (E-DLP) DashboardGo to ConfigurationData Loss Prevention to configure and manage Enterprise DLP.Your Enterprise DLP configuration is shared across the products where you’re using Enterprise DLP. So you might see settings here that were configured elsewhere, and some settings you can configure here can also be leveraged in other products.
- Predefined + Custom Enterprise DLP SettingsEnterprise DLP includes built-in settings that you can use to quickly start protecting your most sensitive content:
- Predefined regex and ML-based data pattern specify common types of sensitive information (like credit cards and social security numbers) that you might want to scan for and protect
- Predefined data profiles group together data patterns that commonly require the same type of enforcement
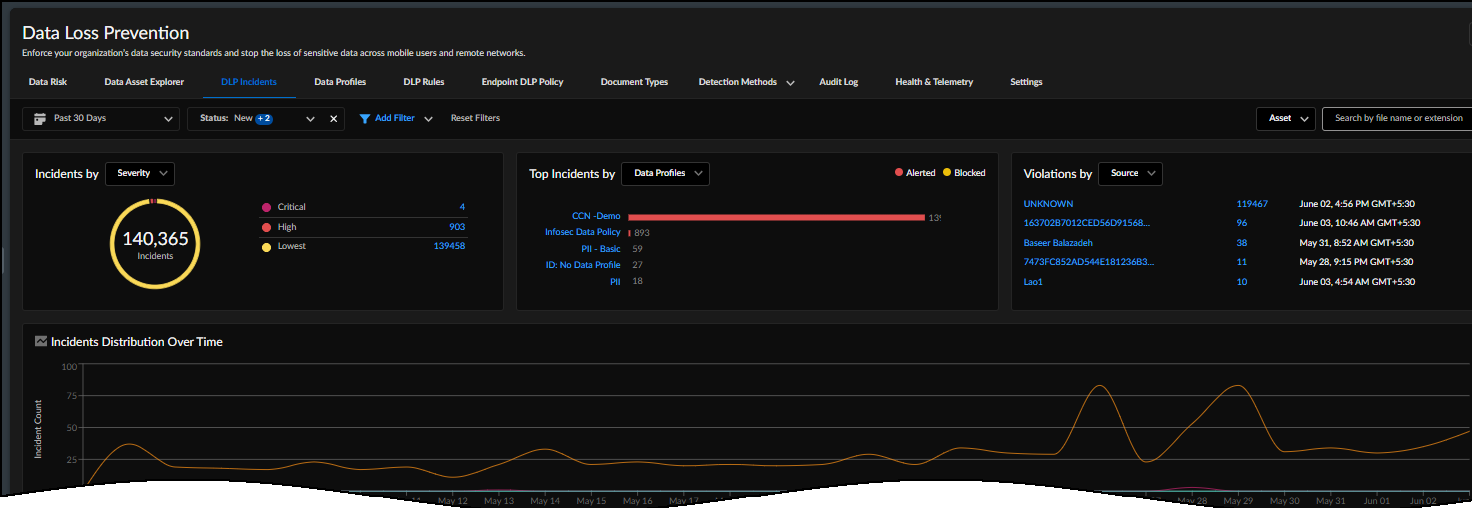
You can also create custom data patterns and profiles directly on Strata Cloud Manager. - Investigation for DLP IncidentsA DLP incident is generated when traffic matches a DLP data profile attached to a security policy rule on Strata Cloud Manager. On the DLP Incidents dashboard, you can view details for the traffic that triggered the incident, such as matched data patterns, the source and destination of the traffic, the file and file type.
- Scanning for Images in Supported File FormatsStrengthen your security posture to further prevent accidental data misuse, loss, or theft with Optical Character Recognition (OCR). OCR allows the DLP cloud service to scan supported file types with images containing sensitive information that match your Enterprise DLP filtering profiles.
- Exact Data Matching (EDM)EDM is an advanced detection tool to monitor and protect sensitive data from exfiltration. Use EDM to detect sensitive and personally identifiable information (PII) such as social security numbers, Medical Record Numbers, bank account numbers, and credit card numbers, in a structured data source such as databases, directory servers, or structured data files (CSV and TSV), with high accuracy.
- Custom Document TypesUpload your custom documents that contain intellectual property or sensitive information to Enterprise Data Loss Prevention (E-DLP) to create custom document types. Your custom document types are used as match criteria in advanced data profile to detect and prevent exfiltration.
- Email DLPEmail DLP prevents exfiltration of emails containing sensitive information with AI/ML powered data detections. For example, Enterprise DLP can prevent exfiltration of sensitive data over an outbound email sent from a salesperson within your organization to their personal email.
- Role-Based Access for Enterprise DLPYou can enable role-based access to Enterprise DLP controls inside Strata Cloud Manager. This allows you to control which users have read and write access privileges to different parts of Enterprise DLP.
Get Started
- Enable Enterprise DLP on Strata Cloud Manager.To set up Enterprise DLP, you need to create a decryption profile to allow the DLP cloud service to inspect traffic. Select ConfigurationSecurity ServicesDecryption and:
- Select ConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and Add Rule.The predefined decryption profile settings enable Enterprise DLP to inspect traffic. Modifying the predefined decryption profile settings isn't required unless you need to enable Strip ALPN (Advanced SettingsSSL Forward Proxy).Add the decryption profile to an SSL Forward Proxy decryption rule.(Optional) Select ConfigurationData Loss PreventionDetection Methods and create a Data PatternYou can create custom Enterprise DLP data patterns to specify what content is sensitive and needs to be protected—this is the content you’re filtering. You can create a custom data pattern based on regular expressions or a data pattern based on file properties.Create a Data ProfileGroup data patterns that should be enforced the same way into a data profile. You can also use data profiles to specify additional match criteria and confidence levels for matching.Create a DLP RuleSpecify the traffic and file types you want Enterprise DLP to protect. Set the action for Enterprise DLP to take when it detects a DLP incident.
