Strata Cloud Manager
Proactively Enforce Security Checks
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
Proactively Enforce Security Checks
Use the Panorama CloudConnector Plugin to block faulty configurations before
they’re committed.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
You can customize security posture checks for your deployment to maximize relevant
recommendations using the features below.
- Security ChecksList of the best practice checks that AIOps for NGFW uses to evaluate your configuration. The configuration of firewalls and Panorama is compared to Palo Alto Networks best practice checks to assess the security posture of your devices and to generate security alerts. You can see a list of the best practice checks that are used to evaluate your configuration.Here, you can:
- Set the severity level for checks to identify the checks that are the most critical to your deployment.
- Temporarily disable checks.If you choose to disable a check, you can specify how long it will remain disabled and leave a comment explaining the reason for disabling it.
- Set the response when a check fails.
- Zone to Role MappingMap the zones in NGFWs to roles to get customized recommendations.
- Role to Security Service MappingManage the security services needed for traffic between zones and roles in all NGFWs.
The Panorama CloudConnector Plugin enables you to take proactive measures against
suboptimal configurations by blocking commits that do not pass particular best
practice checks. When you indicate in AIOps for NGFW that you want a
check to Fail Commit, Panorama automatically blocks commits
of any configuration that does not pass that check. Rather than wait to receive an
alert about a failed best practice check, use the plugin to keep configuration
issues out of your deployment in the first place.
- Ensure that you meet all prerequisites, and install the plugin.Specify the best practice checks that will block commits on failure.
- Select ConfigurationPOSTURESettings.Find the check that you want to block commits.Set Action on Fail to Fail CommitVerify by attempting to commit a configuration that does not pass the check.
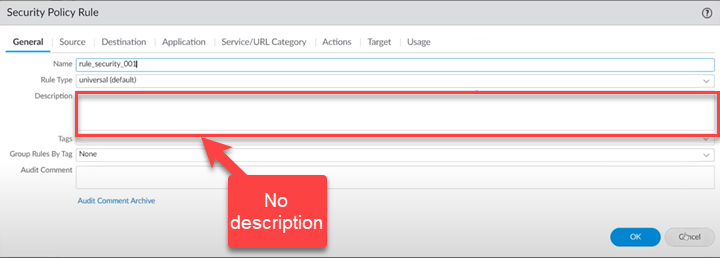
- Log in to Panorama.Violate the best practice check that you specified to Fail Commit.
![]() Select CommitCommit to PanoramaValidate Configuration.
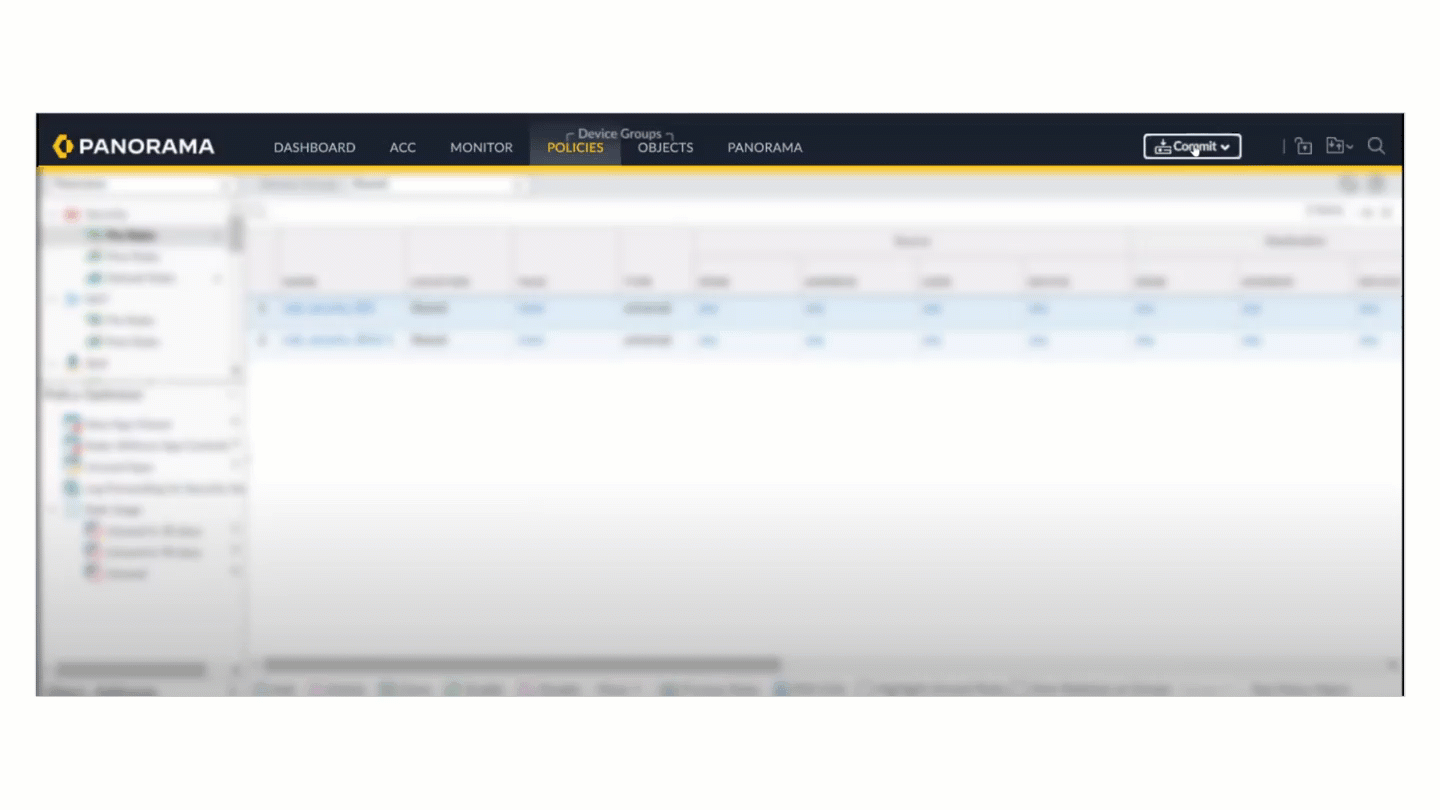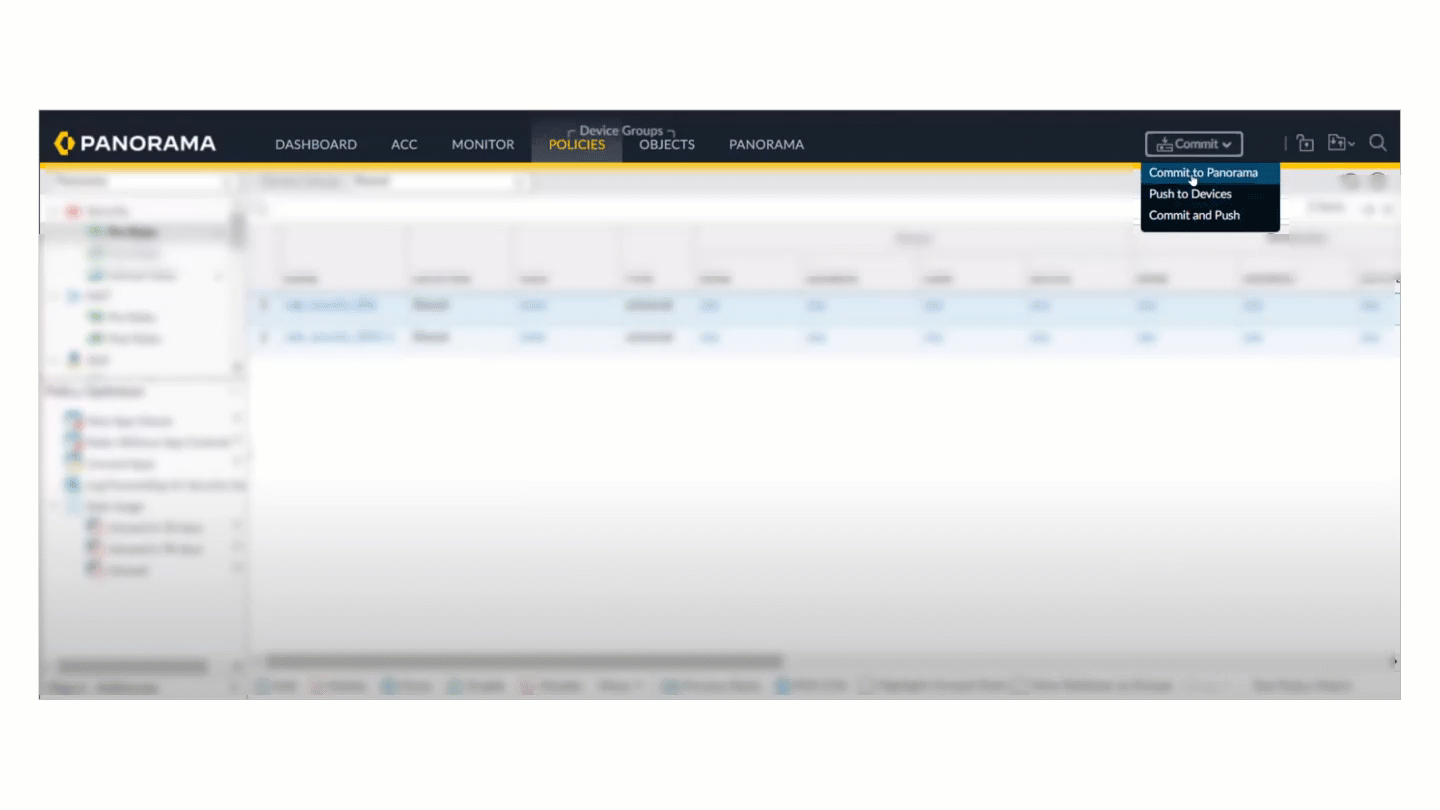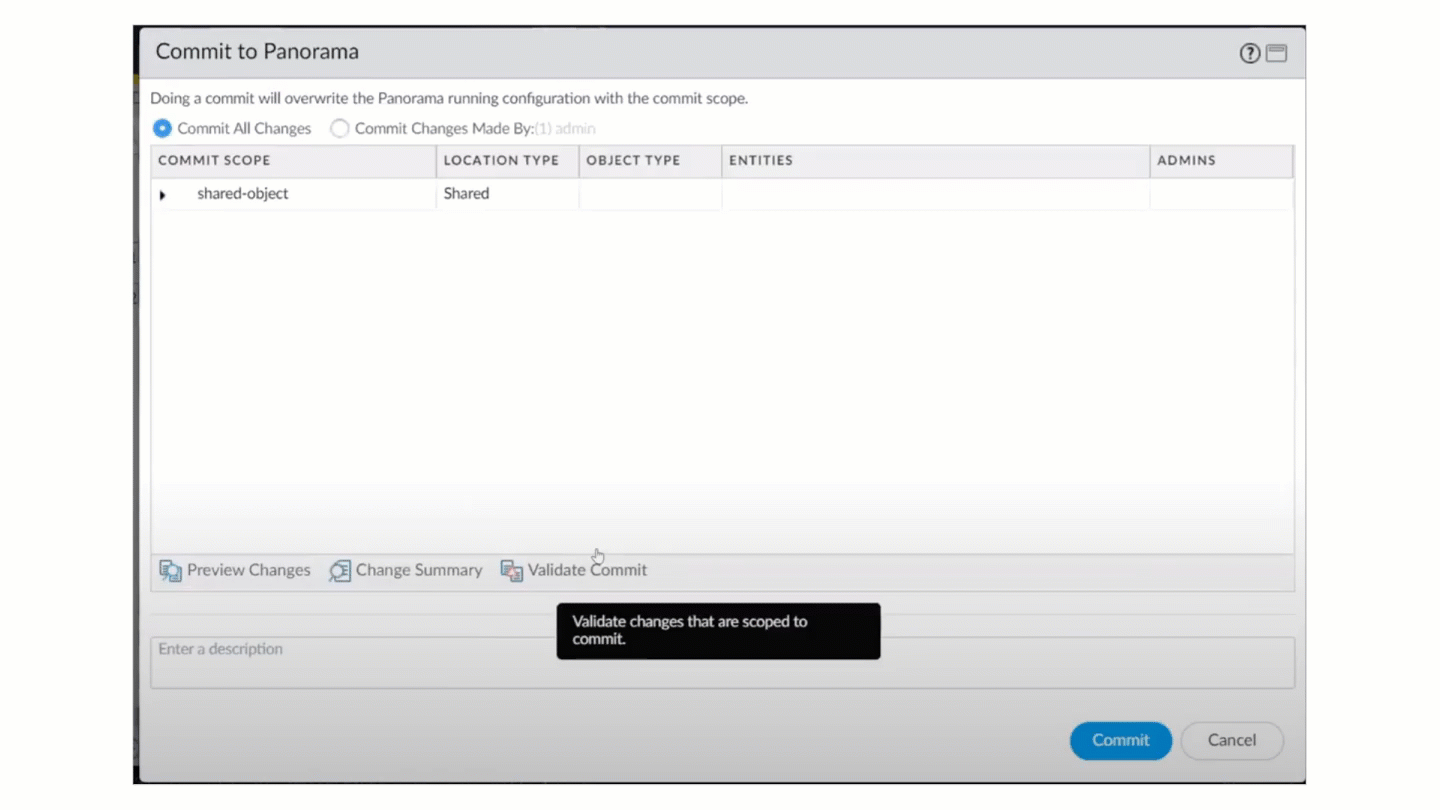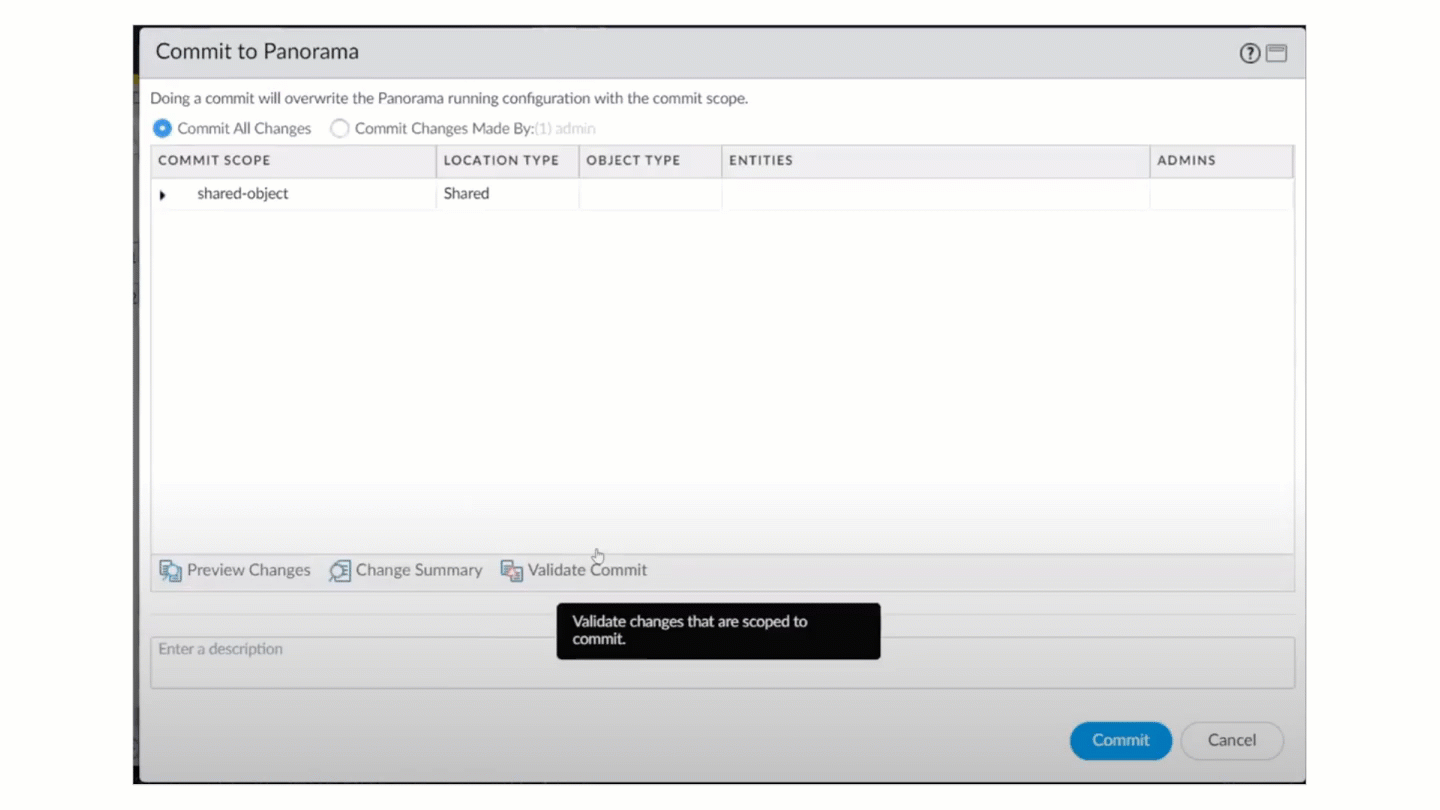
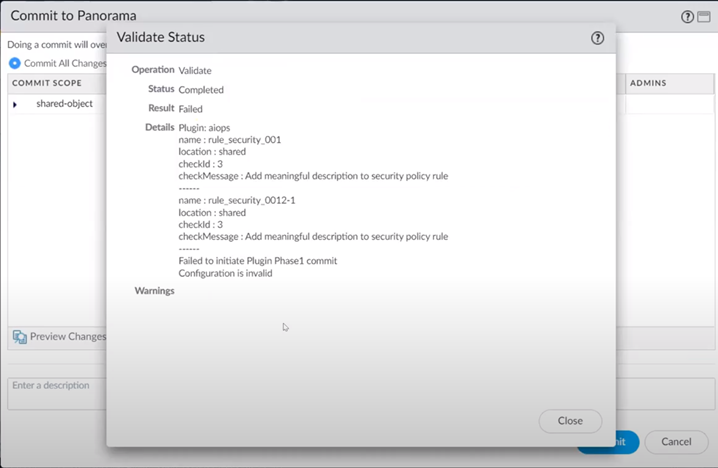
Select CommitCommit to PanoramaValidate Configuration.![]() You should see a dialog stating that the validation failed because the configuration did not pass the best practice check.
You should see a dialog stating that the validation failed because the configuration did not pass the best practice check.![]() Setting a check to Fail Commit causes the check to fail both validation and the actual commit operation.See Security Posture Settings for more information.
Setting a check to Fail Commit causes the check to fail both validation and the actual commit operation.See Security Posture Settings for more information.