GlobalProtect
Troubleshoot HIP Issues
Table of Contents
Expand All
|
Collapse All
GlobalProtect Docs
-
10.1 & Later
- 10.1 & Later
- 9.1 (EoL)
-
- How Does the App Know Which Certificate to Supply?
- Set Up Cloud Identity Engine Authentication
- Configure GlobalProtect to Facilitate Multi-Factor Authentication Notifications
- Enable Delivery of VSAs to a RADIUS Server
- Enable Group Mapping
-
-
- GlobalProtect App Minimum Hardware Requirements
- Download the GlobalProtect App Software Package for Hosting on the Portal
- Host App Updates on the Portal
- Host App Updates on a Web Server
- Test the App Installation
- Download and Install the GlobalProtect Mobile App
- View and Collect GlobalProtect App Logs
-
-
- Deploy App Settings in the Windows Registry
- Deploy App Settings from Msiexec
- Deploy Scripts Using the Windows Registry
- Deploy Scripts Using Msiexec
- Deploy Connect Before Logon Settings in the Windows Registry
- Deploy GlobalProtect Credential Provider Settings in the Windows Registry
- SSO Wrapping for Third-Party Credential Providers on Windows Endpoints
- Enable SSO Wrapping for Third-Party Credentials with the Windows Registry
- Enable SSO Wrapping for Third-Party Credentials with the Windows Installer
- Deploy App Settings to Linux Endpoints
- GlobalProtect Processes to be Whitelisted on EDR Deployments
-
-
- Mobile Device Management Overview
- Set Up the MDM Integration With GlobalProtect
- Qualified MDM Vendors
-
-
- Set Up the Microsoft Intune Environment for Android Endpoints
- Deploy the GlobalProtect App on Android Endpoints Using Microsoft Intune
- Create an App Configuration on Android Endpoints Using Microsoft Intune
- Configure Lockdown Mode for Always On Connect Method on Android Endpoints Using Microsoft Intune
-
- Deploy the GlobalProtect Mobile App Using Microsoft Intune
- Configure an Always On VPN Configuration for iOS Endpoints Using Microsoft Intune
- Configure a User-Initiated Remote Access VPN Configuration for iOS Endpoints Using Microsoft Intune
- Configure a Per-App VPN Configuration for iOS Endpoints Using Microsoft Intune
-
-
-
- Create a Smart Computer Group for GlobalProtect App Deployment
- Create a Single Configuration Profile for the GlobalProtect App for macOS
- Deploy the GlobalProtect Mobile App for macOS Using Jamf Pro
-
- Enable GlobalProtect System Extensions on macOS Endpoints Using Jamf Pro
- Enable GlobalProtect Network Extensions on macOS Big Sur Endpoints Using Jamf Pro
- Add a Configuration Profile for the GlobalProtect Enforcer by Using Jamf Pro 10.26.0
- Verify Configuration Profiles Deployed by Jamf Pro
- Remove System Extensions on macOS Monterey Endpoints Using Jamf Pro
- Non-Removable System Extensions on macOS Sequoia Endpoints Using Jamf Pro
- Uninstall the GlobalProtect Mobile App Using Jamf Pro
-
- Configure HIP-Based Policy Enforcement
- Configure HIP Exceptions for Patch Management
- Collect Application and Process Data From Endpoints
- Redistribute HIP Reports
-
- Identification and Quarantine of Compromised Devices Overview and License Requirements
- View Quarantined Device Information
- Manually Add and Delete Devices From the Quarantine List
- Automatically Quarantine a Device
- Use GlobalProtect and Security Policies to Block Access to Quarantined Devices
- Redistribute Device Quarantine Information from Panorama
- Troubleshoot HIP Issues
-
-
- Enable and Verify FIPS-CC Mode on Windows Endpoints
- Enable and Verify FIPS-CC Mode on macOS Endpoints
- Enable and Verify FIPS-CC Mode Using Workspace ONE on iOS Endpoints
- Enable FIPS Mode on Linux EndPoints with Ubuntu or RHEL
- Enable and Verify FIPS-CC Mode Using Microsoft Intune on Android Endpoints
- FIPS-CC Security Functions
- Resolve FIPS-CC Mode Issues
-
-
- Remote Access VPN (Authentication Profile)
- Remote Access VPN (Certificate Profile)
- Remote Access VPN with Two-Factor Authentication
- GlobalProtect Always On VPN Configuration
- Remote Access VPN with Pre-Logon
- User-Initiated Pre-Logon Connection
- GlobalProtect Multiple Gateway Configuration
- GlobalProtect for Internal HIP Checking and User-Based Access
- Mixed Internal and External Gateway Configuration
- Captive Portal and Enforce GlobalProtect for Network Access
- GlobalProtect on Windows 365 Cloud PC
-
- About GlobalProtect Cipher Selection
- Cipher Exchange Between the GlobalProtect App and Gateway
-
- Reference: GlobalProtect App Cryptographic Functions
-
- Reference: TLS Ciphers Supported by GlobalProtect Apps on macOS Endpoints
- Reference: TLS Ciphers Supported by GlobalProtect Apps on Windows Endpoints
- Reference: TLS Ciphers Supported by GlobalProtect Apps on Android 6.0.1 Endpoints
- Reference: TLS Ciphers Supported by GlobalProtect Apps on iOS 10.2.1 Endpoints
- Reference: TLS Ciphers Supported by GlobalProtect Apps on Chromebooks
- Ciphers Used to Set Up IPsec Tunnels
- SSL APIs
-
- View a Graphical Display of GlobalProtect User Activity in PAN-OS
- View All GlobalProtect Logs on a Dedicated Page in PAN-OS
- Event Descriptions for the GlobalProtect Logs in PAN-OS
- Filter GlobalProtect Logs for Gateway Latency in PAN-OS
- Restrict Access to GlobalProtect Logs in PAN-OS
- Forward GlobalProtect Logs to an External Service in PAN-OS
- Configure Custom Reports for GlobalProtect in PAN-OS
-
6.3
- 6.3
- 6.2
- 6.1
- 6.0
- 5.1
-
- Download and Install the GlobalProtect App for Windows
- Use Connect Before Logon
- Use Single Sign-On for Smart Card Authentication
- Use the GlobalProtect App for Windows
- Report an Issue From the GlobalProtect App for Windows
- Disconnect the GlobalProtect App for Windows
- Uninstall the GlobalProtect App for Windows
- Fix a Microsoft Installer Conflict
-
- Download and Install the GlobalProtect App for macOS
- Use the GlobalProtect App for macOS
- Report an Issue From the GlobalProtect App for macOS
- Disconnect the GlobalProtect App for macOS
- Uninstall the GlobalProtect App for macOS
- Remove the GlobalProtect Enforcer Kernel Extension
- Enable the GlobalProtect App for macOS to Use Client Certificates for Authentication
-
6.1
- 6.1
- 6.0
- 5.1
-
6.3
- 6.3
- 6.2
- 6.1
- 6.0
- 5.1
Troubleshoot HIP Issues
Steps to troubleshoot whether a HIP issue is on the GlobalProtect client side or on
the server side.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
HIP issues usually occur when the GlobalProtect app endpoint posture evaluation
(products installed, custom checks, encryption and backup settings, and more)
doesn't match expected HIP objects and profiles, causing the traffic coming from the
GlobalProtect client to match unexpected security policies. HIP issues also occur
when vendors are not supported by OPSWAT module used by
GlobalProtect app for HIP. When the GlobalProtect app evaluation does not match HIP
on the GlobalProtect gateway side, end users experience restricted or no access
based on the configured security policy. HIP issues are most often on the client
side, such as the OPSWAT module not evaluating some product or version properly.
Issues on the GlobalProtect gateway side are mainly misconfigured HIP objects and
profiles, or problems with HIP redistribution.
Use the following steps to identify or narrow down whether a HIP issue is on the
GlobalProtect client side or on the firewall or GlobalProtect Gateway side.
- Ensure that the GlobalProtect app has no issue with identifying the specific HIP attributes or software, such as: firewall, anti-malware, and more.Using anti-malware as an example, each GlobalProtect app version has a fixed OPSWAT database. If a new anti-malware product or version is released, the currently installed GlobalProtect app might not be able to detect it or, in some cases, may have reduced detection functionality. Refer to the OPSWAT chart of supported products to verify if a new anti-malware product is supported. If it's supported but not being detected, you can try installing the latest GlobalProtect app.
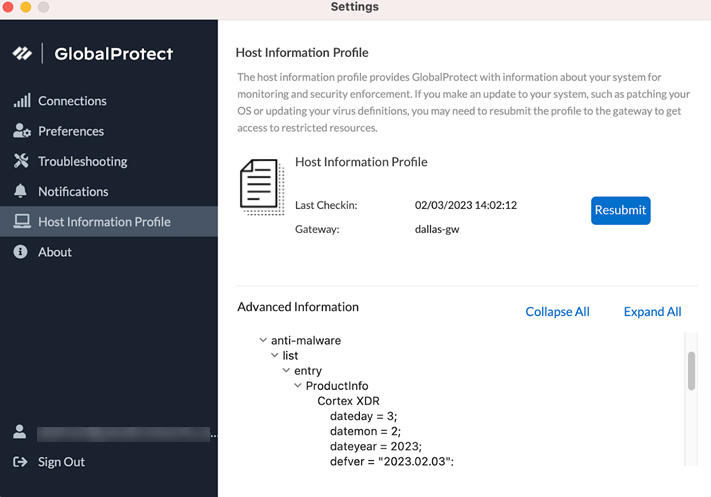
- From the GlobalProtect app, select SettingsHost Information Profile.
- Check the exact HIP category.

- If the anti-malware product is unidentified, try installing a new version of the GlobalProtect app that contains an updated OPSWAT database version if available. You can also try checking the GlobalProtect app release notes. When the GlobalProtect app is updated, the release notes for the new version lists the anti-malware products for which OPSWAT detection capability is updated or fixed based on issues reported by customers.
- Ensure that GlobalProtect app has sent the HIP report with the endpoint posture information.
- Verify if the GlobalProtect app passed the report to the GlobalProtect gateway firewall after connecting successfully.
- If the HIP process gets stuck on the GlobalProtect app, it can eventually cause the app to disconnect due to Idle Timeout expiry if the PAN-OS version is 10.0 or below (which should be refreshed on each hipreportcheck.esp message).
- Sometimes a delay in completing the HIP report comes from evaluating Missing Patches (PanGpHipMp) as this process is time consuming. Keep in mind that a partial HIP report is sent after the configured “Max Wait Time” (default 20s), and the full report is sent after it's ready.
- Ensure that the gateway or firewall has received the HIP report.
- Verify if the HIP report exchange happened by checking MonitorLogsGlobalProtect on the gateway. If yes, you can also verify the following:
- Check for corresponding HIP objects and profiles matched from MonitorLogsHIP.
- Select the magnifying glass on each object or profile to see the full report.
- If you are a Prisma Access customer, logs are forwarded by default to CDL. View the logs in the embedded Log Viewer in the SASE platform or the embedded Explore in CDL. Further details about Explore.
- If you are an NGFW customer, verify if the firewall received the HIP report from the GlobalProtect app by running the following commands from the firewall:The following example provides the details on the Computer name (PAN00965), HIP profile name (Hip-Profile) Matching condition, user (admin), and IP allocated (172.24.10.1). The user name format could be different (email address, username, netbios\username). If you don't type the correct user name format, the output will be empty. In the output, look for the HIP profiles configured for the PC PAN00965.> show user hip-report computer PAN00965 user admin ip 172.24.10.1<?xml version="1.0" encoding="UTF-8"?> <hip-report> <user-name>admin</user-name> <host-name>PAN00965</host-name> <ip-address>172.24.10.1</ip-address> <generate-time>10/29/2012 16:51:17</generate-time> <categories> <entry name="host-info"> <client-version>1.1.7-11</client-version> <os>Microsoft Windows 7 Enterprise Edition Service Pack 1, 32-bit</os> <os-vendor>Microsoft</os-vendor> <host-name>PAN00965</host-name> <network-interface> <entry name="{7383A4FF-0140-4E4C-B70F-0D30438851C9}"> <description>PANGP Virtual Ethernet Adapter</description> <mac-address>02-50-41-00-00-01</mac-address> <ip-address> <entry name="172.24.10.1"/> </ip-address> </entry> <entry name="firewall"> <list> <entry> <ProductInfo> <Prod name="Microsoft Windows Firewall" version="7" vendor="Microsoft Corp."> </Prod> <is-enabled>yes</is-enabled> </ProductInfo> </entry> </list> </entry> <entry name="disk-backup"> <list> <entry> <ProductInfo>
- If there is a delay in the GlobalProtect app sending the HIP report, the gateway will use the cache file (hip_report_base) until the new report is sent and policies are processed based on the new report.
If you don't see the report on the firewall after the max wait time or the info in MonitorLogsGlobalProtect, check the Global Protect app logs to see if the app tried to send the HIP report. Selecting Refresh Connection on the client might help if anything got stuck, but will not determine the reason for the failure. - Ensure that the GlobalProtect app end user is matching the correct HIP profile based on the HIP report submitted.