Strata Cloud Manager
Pre-Change Policy Analysis Reports
Table of Contents
Expand All
|
Collapse All
Strata Cloud Manager Docs
-
- Strata Copilot
- Command Center: Strata Cloud Manager
-
- Dashboard: Build a Custom Dashboard
- Dashboard: Executive Summary
-
- WildFire Dashboard: Filters
- WildFire Dashboard: Total Samples Submitted
- WildFire Dashboard: Analysis Insights
- WildFire Dashboard: Session Trends For Samples Submitted
- WildFire Dashboard: Verdict Distribution
- WildFire Dashboard: Top Applications Delivering Malicious Samples
- WildFire Dashboard: Top Users Impacted By Malicious Samples
- WildFire Dashboard: Top Malware Regions
- WildFire Dashboard: Top Firewalls
- Dashboard: DNS Security
- Dashboard: AI Runtime Security
- Dashboard: IoT Security
- Dashboard: Prisma Access
-
- Application Experience Dashboard: Mobile User Experience Card
- Application Experience Dashboard: Remote Site Experience Card
- Application Experience Dashboard: Experience Score Trends
- Application Experience Dashboard: Experience Score Across the Network
- Application Experience Dashboard: Global Distribution of Application Experience Scores
- Application Experience Dashboard: Experience Score for Top Monitored Sites
- Application Experience Dashboard: Experience Score for Top Monitored Apps
- Application Experience Dashboard: Application Performance Metrics
- Application Experience Dashboard: Network Performance Metrics
- Dashboard: Best Practices
- Dashboard: Compliance Summary
-
- Prisma SD-WAN Dashboard: Device to Controller Connectivity
- Prisma SD-WAN Dashboard: Applications
- Prisma SD-WAN Dashboard: Top Alerts by Priority
- Prisma SD-WAN Dashboard: Overall Link Quality
- Prisma SD-WAN Dashboard: Bandwidth Utilization
- Prisma SD-WAN Dashboard: Transaction Stats
- Prisma SD-WAN Dashboard: Predictive Analytics
- Dashboard: PAN-OS CVEs
- Dashboard: CDSS Adoption
- Dashboard: Feature Adoption
- Dashboard: On Demand BPA
- Manage: IoT Policy Recommendation
- Manage: Enterprise DLP
- Manage: SaaS Security
- Manage: Prisma Access Browser
- Reports: Strata Cloud Manager
-
-
- Strata Cloud Manager Release Information
-
- New Features in March 2025
- New Features in February 2025
- New Features in January 2025
- New Features in December 2024
- New Features in November 2024
- New Features in October 2024
- New Features in September 2024
- New Features in August 2024
- New Features in July 2024
- New Features in June 2024
- New Features in May 2024
- New Features in April 2024
- New Features in March 2024
- New Features in February 2024
- New Features in January 2024
- New Features in November 2023
- New Features in October 2023
- New Features in September 2023
- Known Issues
- Addressed Issues
- Getting Help
Pre-Change Policy Analysis Reports
Provides information about pre-change policy analysis
reports.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Select an analysis report whose status is completed to view the results of the
policy analysis. You can view the results of the analysis.
Intent Satisfaction Results
From the list of analyses under Analysis Requests,
click an analysis to view its analysis results. These results include:
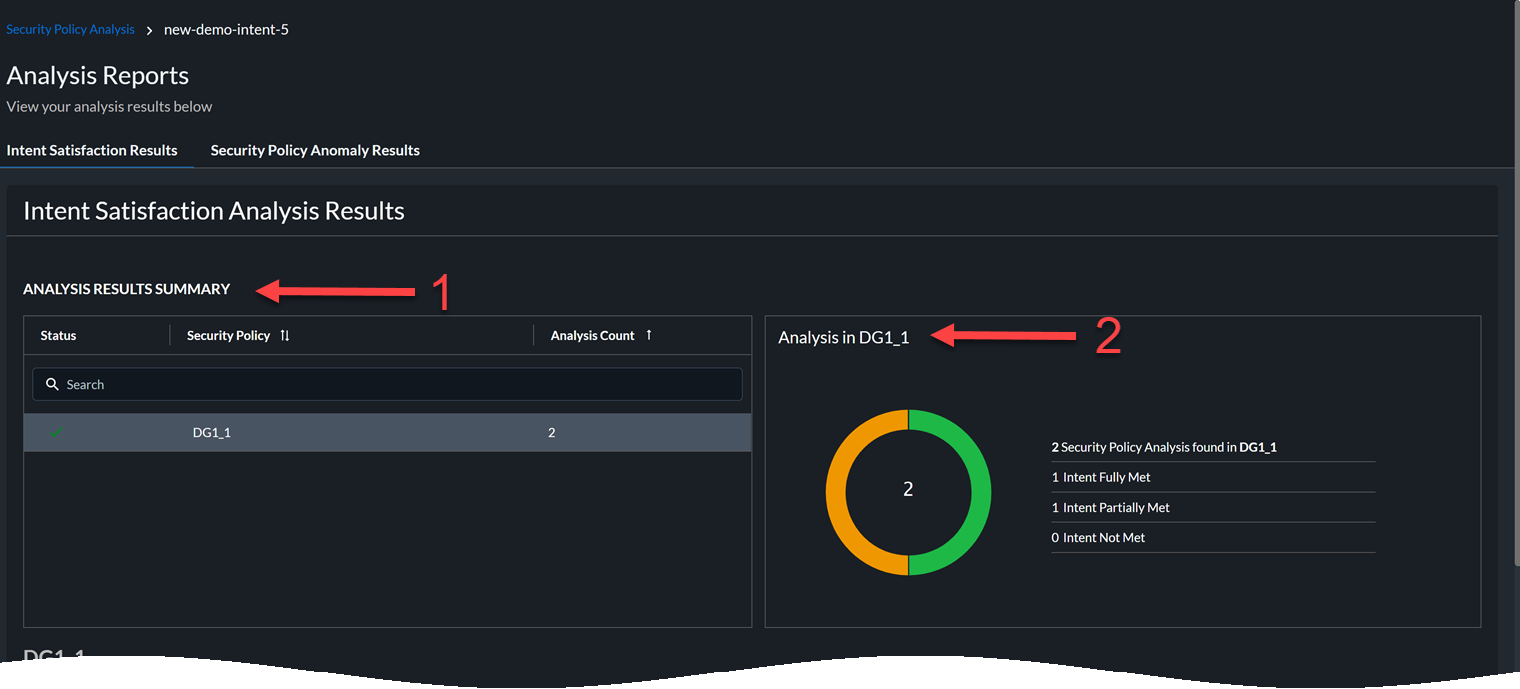
- Summary of the analysis with details about device groups and the anomaly count.
- Click the name of a device group to view the result of the intent satisfaction analysis:
- Intent Fully Met—Your security rule is a duplicate of one of the existing rules in the device group.
- Intent Partially Met—Your security rule is partially meeting the intent of one of the existing rules in the device group.
- Intent not met—Your security rule is a unique rule that is not present in the device group. You can add this rule to the device group.

- View the results of the analysis for the new security rule intent.
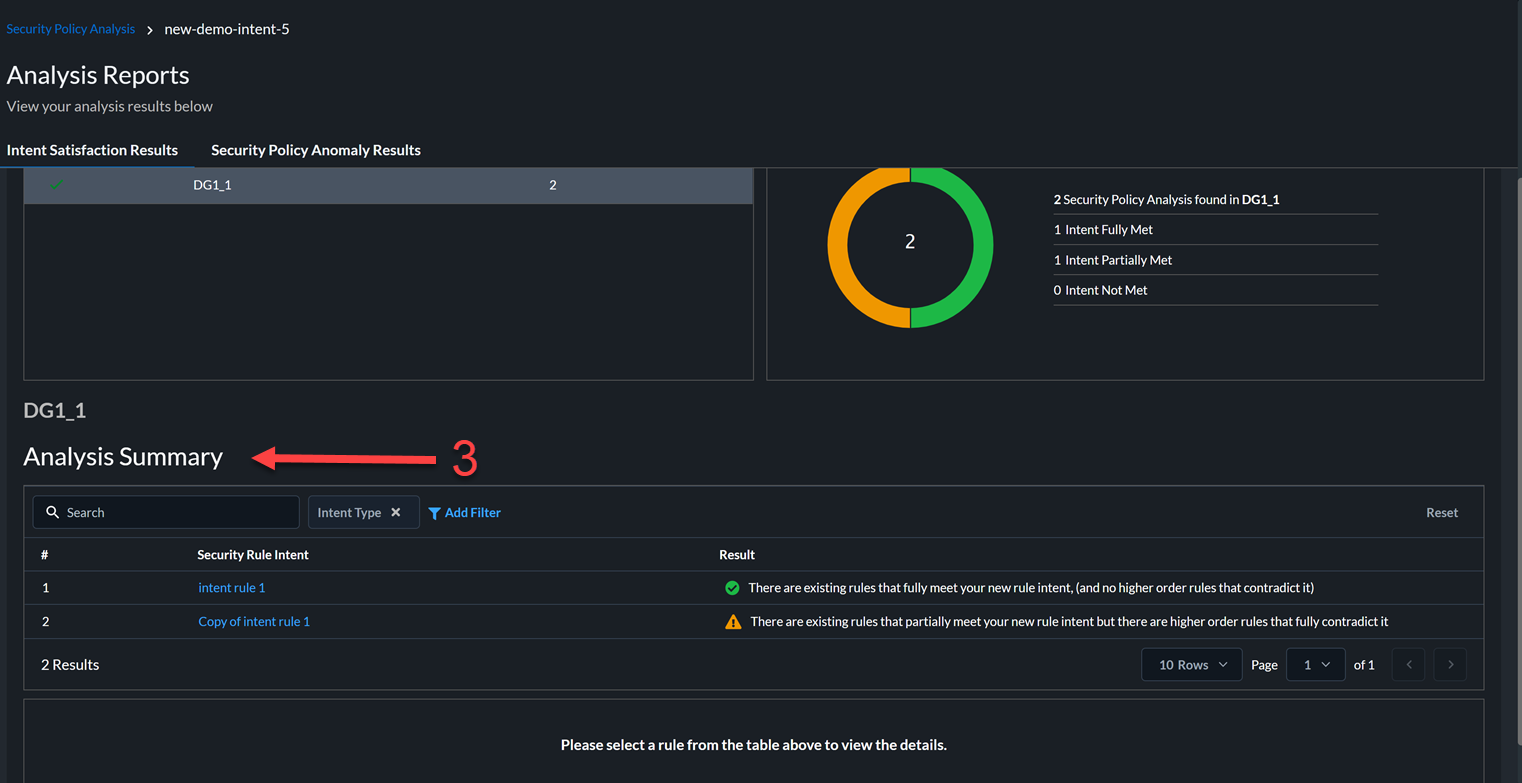
 In this example, there are two rules. The intent of the first rule matches fully with existing rules and the intent of the second rule matches partially with the existing rules.
In this example, there are two rules. The intent of the first rule matches fully with existing rules and the intent of the second rule matches partially with the existing rules. - View the details of the new security rule and check the intent satisfaction results.
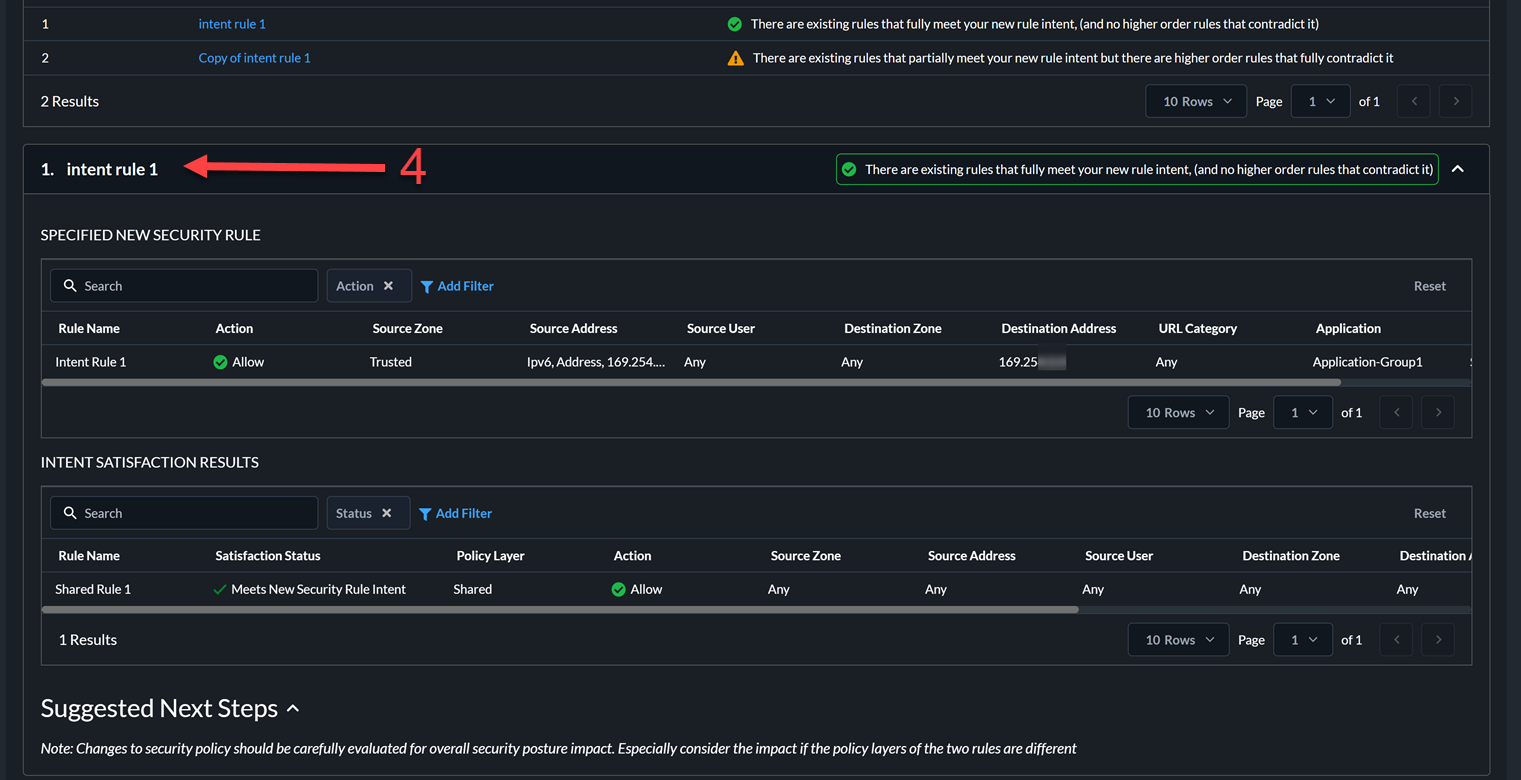
 In this example, all the attributes of the new rule intent rule 1 matches the attributes of the existing rule Shared Rule 1. The intent of the new rule fully matches the intent of the existing rule. Therefore, you need not add this new rule to the configuration.
In this example, all the attributes of the new rule intent rule 1 matches the attributes of the existing rule Shared Rule 1. The intent of the new rule fully matches the intent of the existing rule. Therefore, you need not add this new rule to the configuration.