Create a Policy-Based Decryption Exclusion
Table of Contents
End-of-Life (EoL)
Create a Policy-Based Decryption Exclusion
Exclude traffic that you choose not to decrypt for legal,
privacy, or business reasons from decryption to comply with those
policies while still applying SSL protections with a Decryption
profile.
Policy-based decryption exclusions are for
excluding traffic that you choose not to decrypt. You can
create a policy-based decryption exclusion based on any combination
of the traffic’s source, destination, service, or URL Category.
Examples of traffic you may choose not to decrypt include:
- Traffic that you should never decrypt because it contains personally identifiable information (PII) or other sensitive information, such as the URL Filtering categories financial-services, health-and-medicine, and government.
- Traffic that originates or is destined for executives or other users whose traffic shouldn’t be decrypted.
- Some devices such as finance servers may need to be excepted from decryption.
- Depending on the business, some companies may value privacy and the user experience more than security for some applications.
- Laws or local regulations that prohibit decryption of some traffic.An example of not decrypting traffic for regulatory and legal compliance is the European Union (EU) General Data Protection Regulation (GDPR). The EU GDPR will require strong protection of all personal data for all individuals. The GDPR affects all companies, including foreign companies, that collect or process the personal data of EU residents.Different regulations and compliance rules may mean that you treat the same data differently in different countries or regions. Businesses usually can decrypt personal information in their corporate data centers because the business owns the information. The best practice is to decrypt as much traffic as possible so that you can see it and apply security protection to it.
You can use predefined
URL Categories to except entire categories of websites from decryption,
you can create custom URL Categories to define a customized list
of URLs that you don’t want to decrypt, or you can create an External Dynamic List (EDL) to define
a customized list of URLs that you don’t want to decrypt.
In
environments such as Office 365 that have dynamically changing IP
addresses or in environments where you make frequent changes to
the list of URLs that you want to exclude from decryption, it’s
often preferable to use an EDL instead of a URL Category to specify
the excluded URLs. Using an EDL is less disruptive in dynamic environments because
editing an EDL changes the URL categories dynamically, without a Commit,
while editing a custom URL Category requires a Commit to
take effect.
Create an EDL or a custom
URL Category that contains all the categories you choose not to
decrypt so that one Decryption policy rule governs the encrypted
traffic you choose to allow. Apply a No Decryption profile to the
rule. The ability to add categories to an EDL or a custom URL Category
makes it easy to exclude traffic from decryption and helps keep
the rulebase clean.
Similar
to Security policy rules, the firewall compares incoming traffic
to Decryption policy rules in the policy rulebase’s sequence. Place
Decryption exclusion rules at the top of the rulebase to prevent
inadvertently decrypting sensitive traffic or traffic that laws
and regulations prevent you from decrypting.
If you
create policy-based decryption exclusions, the best practice is
to place the following exclusion rules at the top of the decryption
rulebase, in the following order:
- IP-address based exceptions for sensitive destination servers.
- Source-user based exceptions for executives and other users or groups.
- Custom URL or EDL based exceptions for destination URLs.
- Sensitive predefined URL Category based exceptions for destination URLs of entire categories such as financial-services, health-and-medicine, and government.
Place rules that decrypt traffic
after these rules in the decryption rulebase.
- Exclude traffic from decryption based on match criteria.This example shows how to exclude traffic categorized as financial or health-related from SSL Forward Proxy decryption.
- Select PoliciesDecryption and Add or modify a decryption policy rule.Define the traffic that you want to exclude from decryption.In this example:
- Give the rule a descriptive Name, such as No-Decrypt-Finance-Health.
- Set the Source and Destination to Any to apply the No-Decrypt-Finance-Health rule to all SSL traffic destined for an external server.
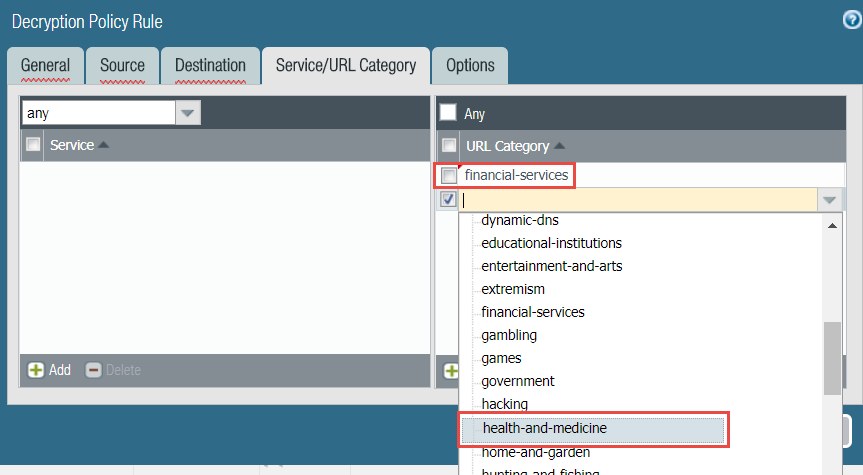
- Select URL Category and Add the URL categories financial-services and health-and-medicine.
![]()
Select Options and set the rule to No Decrypt.(Optional but a best practice) Create a policy-based decryption exclusion to validate certificates for sessions the firewall does not decrypt. Attach the No Decryption profile to the rule and set the profile to Block sessions with expired certificates and Block sessions with untrusted issuers.Click OK to save the No-Decrypt-Finance-Health decryption rule.Place the decryption exclusion rule at the top of your decryption policy rulebase.The firewall enforces decryption rules against incoming traffic in the rulebase sequence and enforces the first rule that match the traffic.Select the No-Decrypt-Finance-Health policy (DecryptionPolicies), and click Move Up until it appears at the top of the list, or drag and drop the rule.Save the configuration.Click Commit.