User-Defined Rules
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
User-Defined Rules
A user-defined rule is a rule that you—or
additional administrators with access to the ESM Console—create
to manage the Traps security policy and agent settings, or to perform
specific actions on the endpoint. A user-defined rule can override
or inherit the settings from the preceding rule in the rule hierarchy.
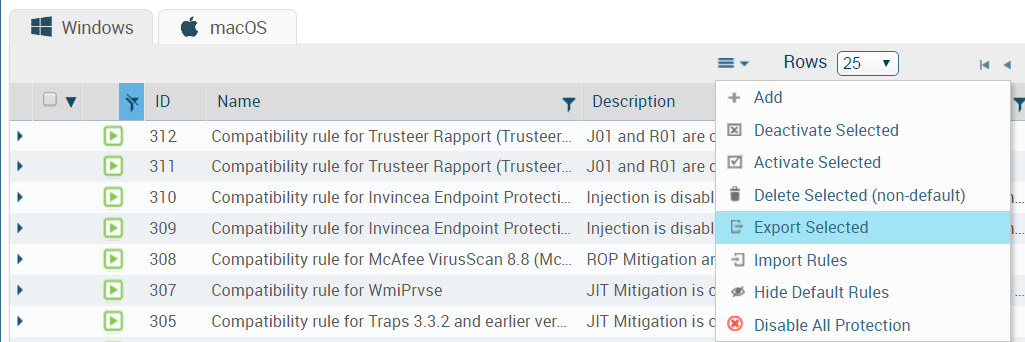
- Export user-defined rules.
- Select the policy management page for the set of rules you are exporting. For example, PoliciesExploitProtection Modules.
- Select the check box next to the rule(s) you want to export or use the check box at the top of the column to select all rules.
- From the action menu at the top of the table, select Export Selected. The ESM Console saves the selected rules to an XML file.
![]()
![]()
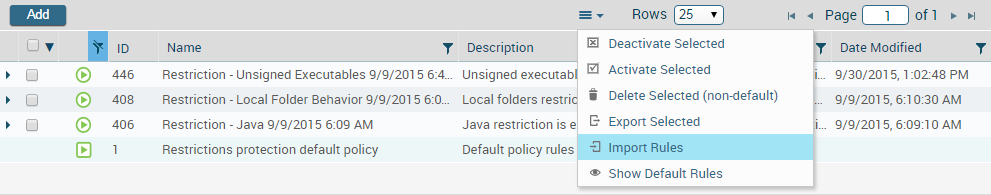
- Import user-defined rules.
- Select the policy management page for the set of rules you are exporting. If your policy file contains rules of different types (for example, exploit protection and malware protection rules), you can choose any rule management page. For example, select PoliciesExploitProtection Modules.
- Select Import Rules from the
action menu at the top of the table.
![]()
![]()
- Browse to the policy file, and then click Upload.The ESM Console appends the new rules to the current policy.