Configure a WildFire Rule
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
Configure a WildFire Rule
WildFire rules determine how Traps detects
and responds to malware on your endpoints. You can create or edit
WildFire rules on the WildFire rule management
page (PoliciesMalwareWildFire). When you configure
a WildFire rule, you can enable any of the following functionality
in Traps:
- Notify the user about malware on the endpoint
- Execute the desired action on malware (either block, permit but notify, or permit and silently log the event)
- Apply the same action on malware to grayware
- Submit unknown executable files, DLL files, and files containing macros—to the ESM Server—for WildFire analysis
- Use local analysis to determine the verdict for a file
- Quarantine malicious files identified locally on the endpoint
- Block unknown files when no WildFire verdict is available
- Block unknown files when the ESM Server is unreachable
By
default, a WildFire rule applies to all users. If needed, you can
customize different WildFire settings for specific users or different
groups of users by creating a WildFire rule for each.
Configure Traps to Analyze Executable Files
To configure Traps to analyze executable files:
- Verify that the ESM components are configured to communicate with WildFire.
- Configure a new WildFire rule.
- Select PoliciesMalwareWildFire.
- Click the tab for the type of endpoint OS, either Windows or macOS.
- From the action menu , select Add.
![]()
- Select Executable Files.
- To activate the WildFire module to enable Traps to calculate and check hash verdicts for executable files against its local cache of hashes, set Activation to On.
- Configure the Action—the behavior
of Traps—when Traps identifies malware.
- Select Inherit to inherit the behavior from the preceding rule in the rule hierarchy.
- Select Prevention to block the malicious file.
- Select Notification to allow the user to open the file, log the issue, and notify the user about the malicious file.
- Select Learning to allow the user to open a malicious file and silently log the issue without notifying the user.
- Specify whether Traps will notify the user about the
malicious file.From the User Alert drop-down, select On to notify the user or Off to silently log the event.
- To exempt a file from WildFire examination, add the file
to the whitelist.Whitelisting files can be useful if the associated hash value changes but the filename stays the same. For example, consider an application such as GoToMeeting which creates a new executable file with the same filename and a unique hash value each time you launch the application. In this case, to exempt GoToMeeting from WildFire examination, you can add the full path for GoToMeeting.exe to the whitelist.If you do not expect the hash value associated with a file to change and want to whitelist the file, we recommend that you configure an administrative hash override for the verdict.
- Click the icon above the Whitelist.
![]()
- Add the Full Path to the file.
Traps will ignore executables or macros run from the specified files
at these paths.The whitelist also supports the same environment variables and wildcards that you can use in restriction rules. For example, to allow a file at path C:\temp\myfilename.exe to run, add the path to the whitelist. Or to allow myfilename.exe to run regardless of where myfilename.exe is stored, you can use wildcards to define the full path as *\myfilename.exe.
- Repeat this process to specify additional files.
- Select the Whitelist Action to Merge or Override the
whitelist with lists defined in other user-defined or default policy
rules.
- If multiple rules specify List Action: Merge, Traps consolidates the Whitelist.
- If multiple rules specify List Action: Override, only the most recent rule (with the highest ID number) takes precedence.
- Click the
- Configure the WildFire integration behavior for executable files:To get the most out of WildFire integration, we recommend that you turn on all WildFire functionality.
- Upload Files for WildFire Analysis—Set this value to On to enable Traps to send unknown executable files to the ESM, which sends the files to WildFire for analysis.
- Apply Malware Verdict on Grayware—Set this option to On to treat all grayware as malware. Otherwise, if this option is Off, grayware is considered benign and is not blocked.
- Enable Local Analysis on Unknown Files—Set this option to On to enable Traps to use embedded machine learning to determine the likelihood that an unknown executable file is malware and issue a local verdict for the file. When this option is Off and is configured to block unknown files, users will not be permitted to open unknown executable files. As a result, the unknown file remains blocked until Traps receives an official WildFire verdict.
- Quarantine Prevented Files—Set this option to On to enable Traps to quarantine malware on the endpoint. A file is considered malware if one of the following sources issued a malware verdict for the file: WildFire, administrative policy override, or local analysis. Set this option to Off to allow malware to remain on the endpoint in its original location. The quarantine feature is not available for malware identified in network drives.
- WildFire Verdict is Unavailable—Set this option to Block Unknowns or Allow Unknowns when the file is unknown in the local and server cache.By default Traps permits unknown executable files to open; however, if local analysis is enabled, Traps always returns a verdict for an unknown executable file. Therefore, enabling these options files only applies to agents for which local analysis is not enabled.
- ESM Unreachable—Set this option to Block Unknowns or Allow Unknowns (default) when Traps cannot reach the ESM Server to query for a verdict or submit the file for analysis.
- (Optional)
Add Conditions to
the rule. By default, a new rule does not contain any conditions.To specify a condition, select the Conditions tab, select the condition in the Conditions list, and then Add it to the Selected Conditions list. Repeat this step to add more conditions, as needed. You can also define new Conditions.
- (Optional)
Define the Target
Objects to which to apply the rule.To define a smaller subset of target objects, select the Objects tab, and then enter one or more AD Users, AD Computers, AD Groups, AD Organizational Unit, Existing Endpoints, or Existing Groups in the Include or Exclude areas. The Endpoint Security Manager queries Active Directory to verify the users, computers, groups, or organizational units. The ESM Console also offers autocompletion as you type for existing endpoints and existing virtual groups.
- (Optional)
Review the rule name and description. The ESM Console automatically
generates the rule name and description based on the rule details
but permits you to change these fields, if needed.To override the autogenerated name, select the Name tab, clear the Activate automatic description option, and then enter a rule name and description of your choice.
- Save the WildFire rule.Do either of the following:
- Save the rule without activating it. This option is only available for inactive, cloned, or new rules. When you are ready to activate the rule, select the rule from the PoliciesMalwareWildFire page and then click Activate.
- Apply the rule to activate it immediately.
After saving or applying a rule, you can return to the WildFire page at any time to Delete or Deactivate the rule.
Configure Traps to Analyze DLL Files
In addition to executable files and macros,
Traps can prevent built-in system and other common DLL-loading processes
from loading malicious DLL files on Windows endpoints. The WildFire
module for DLL Files enables Traps to leverage both local analysis
and WildFire threat intelligence to analyze and identify the nature
of a DLL.
In prevention mode, Traps blocks both the process
attempting to load a known malicious DLL and the DLL itself. To
determine whether to examine an unknown DLL, Traps considers the
following criteria:
- Loading process—Traps examines the DLL if it is loaded by a process configured in the DLL Files security policy. This policy contains a list of legitimate Windows system processes (such as rundll32.exe) that attackers commonly use to load DLLs on the endpoint. The default list of protected processes which trigger examination can change with content updates. To protect additional DLL loading processes, you can add any process defined on the Process Management page to a new DLL Files rule.
- DLL Files whitelist—Traps examines the DLL if it is not in the DLLs whitelist.
- Trusted signer—Traps examines the DLL if it is not signed by a trusted signer.
When an unknown DLL
meets the above criteria, Traps performs additional evaluation and
handling actions depending on the configuration of your DLL Files
policy. For unknown DLLs, Traps minimally queries the ESM for an
official WildFire verdict for the DLL file. Traps can also submit
the DLL file (which can have a maximum file size of 100MB) for in-depth
analysis and use local analysis to issue a local verdict for unknown files.
To exempt a DLL from examination by this module (regardless of the
loading process), you can add it to the whitelist.
- Verify that the ESM components are configured to communicate with WildFire.
- Configure a new WildFire rule.
- Select PoliciesMalwareWildFireWindows .
- From the action menu , select Add.
![]()
- Select DLL Files.
- (ESM 4.1.1 and later releases) Choose the Rule
Type, either General module settings to apply
the rule to all processes, or Process-specific settings to
apply the rule to select processes.The type of rule also determines the settings that you can configure:
- General module settings—Settings which apply to all DLL files including the Action mode, User Alert, Whitelist, Analysis Configuration, and Unknown Verdict Configuration. In addition, Activation is automatically enabled for General module settings rules.
- Process-specific settings—Activation and Action mode settings which apply to select processes. These settings override the settings you specify in a General module settings rule. All other settings are not configurable.
- To enable Traps to calculate and check hash verdicts for DLL files against its local cache of hashes, set Activation to On.
- Configure the Action—the behavior
of Traps—when Traps identifies malware.
- Select Inherit to inherit the behavior from the preceding rule in the rule hierarchy.
- Select Prevention to block the malicious file.
- Select Notification to allow the user to open the file, log the issue, and notify the user about the malicious file.
- Select Learning to allow the user to open a malicious file and silently log the issue without notifying the user.
- Specify whether Traps will notify the user about the
malicious file.From the User Alert drop-down, select On to notify the user or Off to silently log the event.
- (Optional) To exempt a DLL file from WildFire
examination—regardless of the loading process that tries to run
it—add the file to the whitelist.Whitelisting files can be useful if the associated hash value changes but the filename stays the same. If you do not expect the hash value associated with a DLL file to change and want to whitelist the file, we recommend that you configure an administrative hash override for the verdict.When multiple DLL Files rules contain whitelists, Traps merges the lists into a single whitelist of DLL files. For simplified management of whitelisted DLL files, we recommend that you create a new rule and give it a descriptive name which identifies the rule purpose (for example, DLL rule for whitelisted files).
- Click to Whitelist DLLs.
![]()
- Add the Full Path to the DLL
file. Traps will ignore DLL files from the specified files at these
paths.The whitelist also supports the same environment variables and wildcards that you can use in restriction rules. For example, to allow a file at path C:\temp\myfilename.dll to run, add the path to the whitelist. Or to allow myfilename.dll to run regardless of where myfilename.dll is stored, you can use wildcards to define the full path as *\myfilename.dll.
- Repeat this process to specify additional files.
To apply the whitelist, you must activate (Apply) the rule. Until the rule which specifies the file is activated, the ESM Console identifies the file in plain text. After a rule containing the file is activated, the ESM Console identifies the file in bold. When you delete a file from a whitelist, the ESM Console identifies the file in strikethrough font. The file remains in the active whitelist until you apply the rule. After you apply the rule, the ESM Console removes the file from the whitelist completely. - Click
- Specify the processes which trigger the DLL file examination (Activation is On).
If you disabled activation (Activation is Off),
specify the processes which are exempt from DLL examination.
- Click to add Protected Processes. The ESM Console provides autocompletion based on the processes on the Process Management page.
![]()
- Repeat this process to specify additional files.
- Click
- Configure the WildFire analysis settings for DLL files:
- Upload Files for WildFire Analysis—Set this value to On (default) to enable Traps to send unknown DLL files to the ESM, which sends the files to WildFire for analysis. Set this value to Off if you do not want to send files to WildFire for analysis.
- Apply Malware Verdict on Grayware—Set this option to On to treat all grayware DLLs as malware. Otherwise, if this option is Off (default), grayware is considered benign and is not blocked.
- Enable Local Analysis on Unknown Files—Set this option to On (default) to allow Traps to use statistical analysis to determine the nature of an unknown DLL. Set this value to Off if you do not want Traps to analyze a DLL. In prevention mode, Traps will block or allow unknown DLLs according to the unknown verdict configuration.
- Configure the Traps behavior when a DLL file is unknown:
- WildFire Verdict is Unavailable—Set this option to Allow Unknowns (default) or Block Unknowns when the file is unknown in the local and server cache.If local analysis is enabled, Traps always returns a verdict for an unknown DLL file. Therefore, configuring this option only applies to agents for which local analysis is not enabled.
- ESM Unreachable—Set this option to Allow Unknowns (default) or Block Unknowns when Traps cannot reach the ESM Server to query for a verdict or submit the file for analysis.
- (Optional)
Add Conditions to
the rule. By default, a new rule does not contain any conditions.To specify a condition, select the Conditions tab, select the condition in the Conditions list, and then Add it to the Selected Conditions list. Repeat this step to add more conditions, as needed. You can also define new Conditions.
- (Optional)
Define the Target
Objects to which to apply the rule.To define a smaller subset of target objects, select the Objects tab, and then enter one or more AD Users, AD Computers, AD Groups, AD Organizational Unit, Existing Endpoints, or Existing Groups in the Include or Exclude areas. The Endpoint Security Manager queries Active Directory to verify the users, computers, groups, or organizational units. The ESM Console also offers autocompletion as you type for existing endpoints and existing virtual groups.
- (Optional)
Review the rule name and description. The ESM Console automatically
generates the rule name and description based on the rule details
but permits you to change these fields, if needed.To override the autogenerated name, select the Name tab, clear the Activate automatic description option, and then enter a rule name and description of your choice.
- Save the WildFire rule.Do either of the following:
- Save the rule without activating it. This option is only available for inactive, cloned, or new rules. When you are ready to activate the rule, select the rule from the PoliciesMalwareWildFire page and then click Activate.
- Apply the rule to activate it immediately.
After saving or applying a rule, you can return to the WildFire page at any time to Delete or Deactivate the rule.
Configure Traps to Analyze Macros
In addition to executable files and DLLs,
Traps can block malicious macros from running when launched from
a Microsoft office process on Windows endpoints. Traps and the ESM
identify macros individually by the unique hash calculated for the
macro and correlate this value with the hash of the Microsoft Office
file from which the macro attempted to run. This enables the ESM
to query WildFire for the verdict issued to the parent file. By
default, Traps automatically blocks malicious macros from the following
Microsoft Excel and Microsoft Word file formats (see File
Type Analysis):
The following figure displays the evaluation
flow when a macro attempts to run from a supported file format and
the file is not whitelisted:
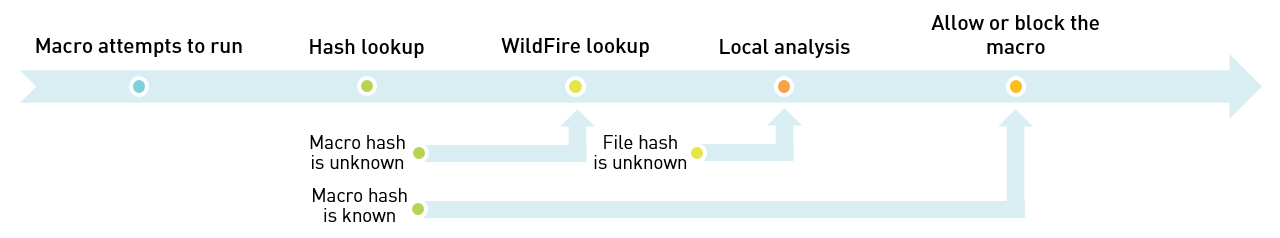
To
configure Microsoft Office file protection:
- Verify that the ESM components are configured to communicate with WildFire.
- Configure a new WildFire rule.
- Select PoliciesMalwareWildFireWindows.
- From the action menu , select Add.
![]()
- Select Office Files.
- To activate the WildFire module to enable Traps to calculate and check hash verdicts against its local cache of hashes, set Activation to On.
- Configure the Action—the behavior
of Traps—when Traps identifies malware.
- Select Inherit to inherit the behavior from the preceding rule in the rule hierarchy.
- Select Prevention to block the malicious file.
- Select Notification to allow the user to open the file, log the issue, and notify the user about the malicious file.
- Select Learning to allow the user to open a malicious file and silently log the issue without notifying the user.
- Specify whether Traps will notify the user about the
malicious file.From the User Alert drop-down, select On to notify the user or Off to silently log the event.
- To exempt a file from WildFire examination, add the file
to the whitelist.Whitelisting files can be useful if the associated hash value changes but the filename stays the same. If you do not expect the hash value associated with a file to change and want to whitelist the file, we recommend that you configure an administrative hash override for the verdict.
- Click the icon above the Whitelist.
![]()
- Add the Full Path to the file.
Traps will ignore executables or macros run from the specified files
at these paths.The whitelist also supports the same environment variables and wildcards that you can use in restriction rules.
- Repeat this process to specify additional files.
- Select the Whitelist Action to Merge or Override the
whitelist with lists defined in other user-defined or default policy
rules.
- If multiple rules specify List Action: Merge, Traps consolidates the Whitelist.
- If multiple rules specify List Action: Override, only the most recent rule (with the highest ID number) takes precedence.
- Click the
- Configure the WildFire integration behavior for the type
of file:To get the most out of WildFire integration, we recommend that you turn on all WildFire functionality.Set Upload Files with Macros for WildFire Analysis to On to enable the ESM Server to send the files it received from Traps agents which contain unknown macros to WildFire for analysis.
- (Optional)
Add Conditions to
the rule. By default, a new rule does not contain any conditions.To specify a condition, select the Conditions tab, select the condition in the Conditions list, and then Add it to the Selected Conditions list. Repeat this step to add more conditions, as needed. You can also define new Conditions.
- (Optional)
Define the Target
Objects to which to apply the rule.To define a smaller subset of target objects, select the Objects tab, and then enter one or more AD Users, AD Computers, AD Groups, AD Organizational Unit, Existing Endpoints, or Existing Groups in the Include or Exclude areas. The Endpoint Security Manager queries Active Directory to verify the users, computers, groups, or organizational units. The ESM Console also offers autocompletion as you type for existing endpoints and existing virtual groups.
- (Optional)
Review the rule name and description. The ESM Console automatically
generates the rule name and description based on the rule details
but permits you to change these fields, if needed.To override the autogenerated name, select the Name tab, clear the Activate automatic description option, and then enter a rule name and description of your choice.
- Save the WildFire rule.Do either of the following:
- Save the rule without activating it. This option is only available for inactive, cloned, or new rules. When you are ready to activate the rule, select the rule from the PoliciesMalwareWildFire page and then click Activate.
- Apply the rule to activate it immediately.
After saving or applying a rule, you can return to the WildFire page at any time to Delete or Deactivate the rule. - After you configure DLL file protection, you can perform
any of the following actions:
- Although the agent automatically requests the latest security policy at the next heartbeat communication with the ESM Server, you can use the Check In Now option from the Traps console to force an immediate check-in. To verify that the agent received the rule, select AdvancedPolicy and review the recent rules.
- View all security events related to DLLs on the Security Events pages (PreventionsWildFire/Hash Control or NotificationsWildFire/Hash Control.
- View all analyzed DLLs on the PoliciesMalwareHash Control page.To display only verdicts for DLL files, use the search conditions to set File Type: Is: DLL.
