Policy Enforcement
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
Policy Enforcement
When you configure security policy rules, the Traps
rules mechanism merges all configured rules into an effective policy
that is evaluated for each endpoint. To determine which rules apply
to the specific endpoint, the agent must evaluate the policy based
on the following considerations:
- Rule type—Traps evaluates exploit protection, malware protection, and restriction rules when a process, executable file, dll, or macro attempts to run. When the security policy contains multiple rules of the same rule type and module, Traps must then evaluate the rules based on the specificity of the rule and the modification date.
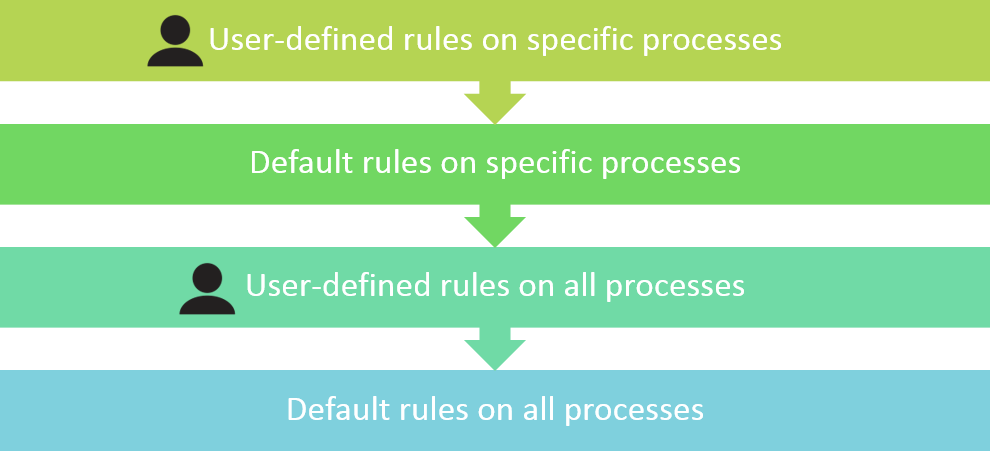
- Process specificity—The more specific a rule, the higher the priority. For example, a rule configured for a specific process takes precedence over a rule configured for all processes even if the more generic rule was created more recently.
![]()
- Modification date—When rules have the same level of specificity, where the core configuration is the same across two or more rules, Traps determines which rule takes precedence to avoid rule conflicts. For example, consider two exploit protection rules which use the same module to protect the same process but have conflicting settings: One rule enables the module and the other disables the module. In this case, the rule that was created or edited more recently takes precedence over an older rule. An easy way to identify which rule is more recent is to look at the ID number assigned to the rule. The ESM Console assigns an ID to each rule sequentially as you modify or add rules to the security policy so a higher ID number indicates the rule was created more recently.
- Target Objects—Target objects allow you to apply rules to specific endpoints, Active Directory objects, or virtual groups that you define in the ESM Console. For a rule to apply, the rule must specify the endpoint as a target object or specify no target objects (meaning the rule applies to all objects). In addition, the rule must not specify the endpoint as a target object from which to exclude the rule.
- Conditions—A condition is an identifying characteristic on the endpoint which can be used to apply or exclude a rule on an endpoint. For a rule to apply, the endpoint must match the conditions specified in the rule. For example, rules with conditions for Windows 7 endpoints will apply only to Windows 7 endpoints. Similar to target objects, the endpoint must not match any exclude conditions for the rule to apply.