Manage Security Events
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
Manage Security Events
Select Security EventsThreats to display a list of
threats that have occurred in your network. The default view of the
threats page includes all prevention and notification events. The
menu on the side of the Threats page also
provides links to filtered lists of threats by event (Preventions and Notifications)
and also by rule type.
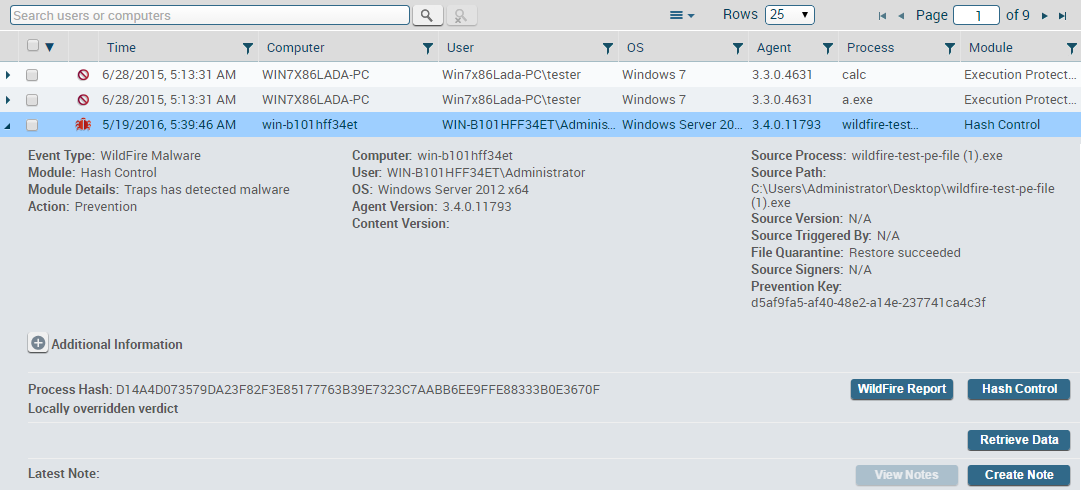
The
standard details view of the Threats page
displays a table of security events with fields displayed along
the top. Selecting an event in the Threats table expands the row
to reveal additional details about the security event. In addition
to viewing details about threat events, you can create and view
notes about the event, retrieve log data about the event from the
endpoint, or create an exclusion rule to allow the process to run
on a particular endpoint.
- Filter for specific eventsUse the search field to search for users or endpoints, or use the filters at the top of each column to narrow the results.
- View additional details about the eventSelect the row for the event. The row expands to reveal additional details about the security event.For details on the fields in the security events table, refer to the online help.
- Export events to a comma separated values (CSV) file.
- Select the checkbox for each event that you want to export.
- Click the action menu , and select Export Selected. The ESM Console generates the CSV file containing the selected records.
![]()
- Delete events.
- Select the checkbox for each event that you want to export.
- Click the action menu , and select Delete Selected. The ESM Console removes the records from all Security Events pages.
![]()
- (WildFire events only) View the WildFire Report
for an executable fileFrom the expanded view of a security event, click WildFire Report.
- (WildFire events only) Jump to the Hash Control
entry for the executable file. From the expanded view of a security event, click Hash Control.
- Retrieve prevention data from the endpoint. From the expanded view of a security event, click Retrieve Data. The ESM Console uses the prevention key and trigger information to request data about the prevention event from the agent. After the information is sent to the forensic folder, you can view information about the download from the MonitorData Retrieval page.
- View administrative notes about the event From the expanded view of a security event, click View Notes to view notes that you or other administrators entered about the security event. If there are no notes, this option is grayed out.
- Create an administrative note about the event From the expanded view of a security event, click Create Note to record information about the security event for follow-up at a later time or date.
- (Exploit events only) Create a rule to exclude
an endpoint from exploit protection. From the expanded view of a security event, click Create Rule to create an exploit protection rule that excludes the endpoint from the exploit protection rule that prevented the process from running. The rule uses the details from the security event to populate a rule with settings that allow a process to run on a specific endpoint.
