Small Single-Site Deployment
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
Small Single-Site Deployment
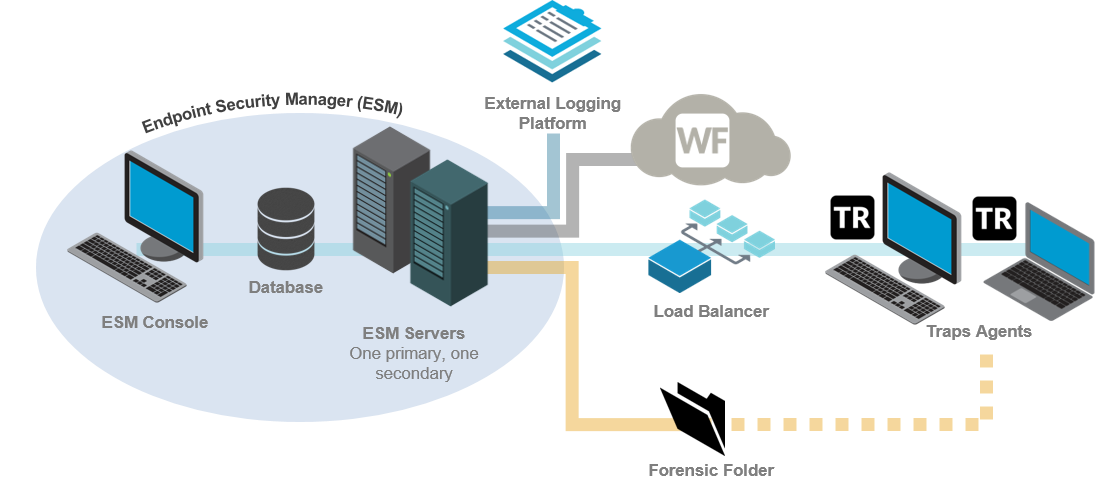
This single-site deployment scenario supports up to 30,000 Traps
agents and consists of the following components:
- One dedicated database server
- One ESM Console for managing the security policy and Traps agents
- Two ESM Servers, one primary and one backup, on the same network segment as the database server and ESM Console
- One forensic folder accessible by all endpoints for storing real-time forensic details about security events
- (Recommended) WildFire integration
- (Optional) Load balancer for distributing traffic across ESM Servers
- (Optional) External logging platform, such as an SIEM or syslog
In this deployment scenario, a single site contains the database,
ESM Console for managing local policies and endpoints, and redundant
ESM Servers. In the event that the primary ESM Server is inaccessible,
Traps agents connect to the Endpoint Security Manager using the
backup server. Both servers obtain the security policy from the
database and distribute the policy to the agents.
