Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
WildFire
The Traps agent is designed to block attacks before
any malicious code can run on the endpoint. While this approach
ensures the safety of data and infrastructure, it enables the collection
of forensic evidence only at the moment of prevention. And while
Traps can prevent the attack, Traps alone cannot fully reveal the
purpose of the attack or its entire flow.
To provide more insight into malware activity, the Endpoint Security
Manager supports WildFire integration. This enables the Endpoint
Security Manager to send any unknown executable files to WildFire,
a malware analysis environment that turns unknown threats into preventable
incidents.
You can integrate WildFire with your Endpoint Security Manager
using either of the following two options:
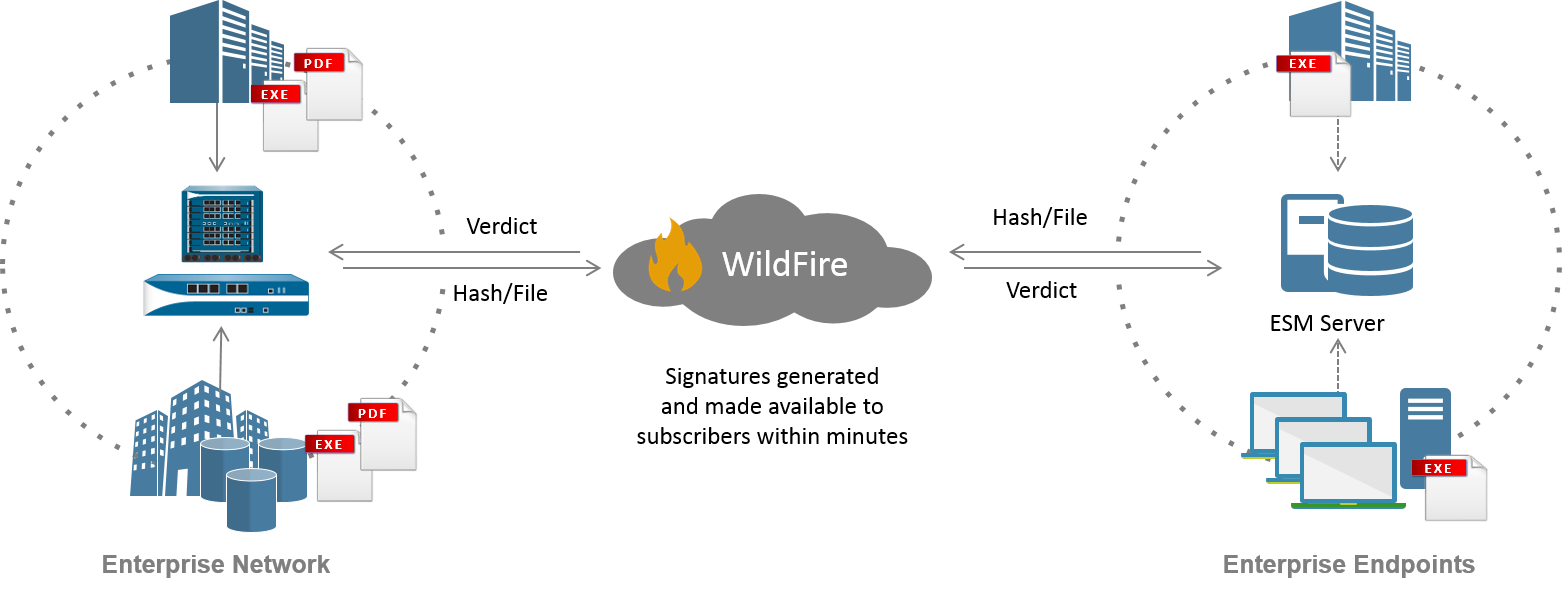
- WildFire public cloud—The WildFire Virtual Environment analyzes and identifies previously unknown malware and generates signatures that Palo Alto Networks firewalls and Palo Alto Networks Endpoint Security Managers can use to detect and block the malware. When Traps detects an unknown sample (an executable file or macro), the Endpoint Security Manager can automatically forward the sample for WildFire analysis.
![]()
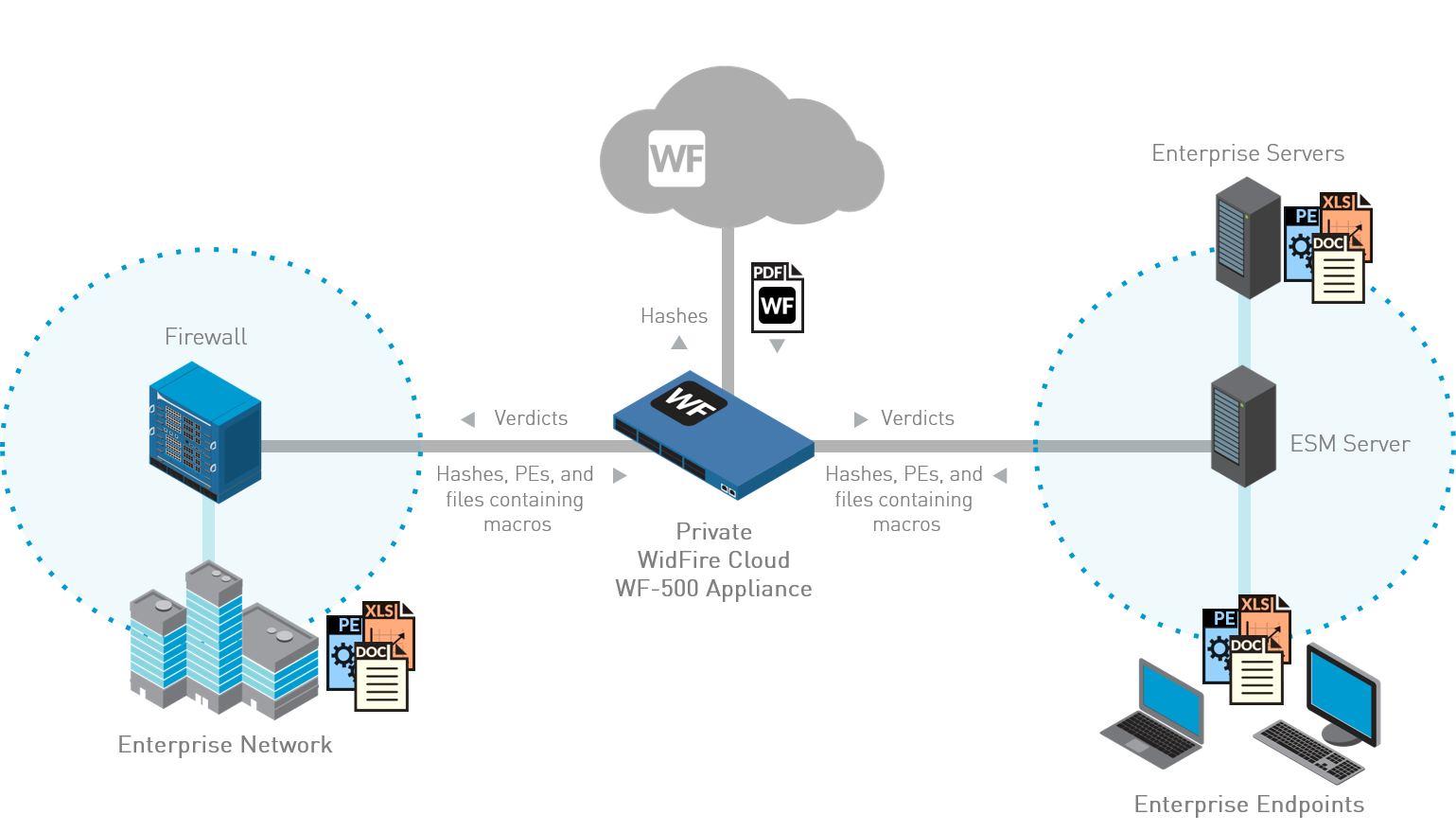
- WildFire private cloud—A WildFire private cloud enables you to analyze unknown executable files discovered on Windows endpoints in a local sandbox. To deploy a WildFire private cloud, you must install a local WF-500 appliance.
![]() The local WF-500 appliance is ideal for deployments with privacy and legal regulations that restrict the transfer of files outside your network. The WildFire-500 appliance queries the WildFire public cloud to obtain the verdict and, if unknown, analyzes the executable file in the local sandbox. By default, the WF-500 appliance does not send discovered malware outside your network, however, you can choose to automatically forward malware to the WildFire public cloud to generate and distribute signatures to all Palo Alto Networks firewalls with Threat Prevention and WildFire licenses. Otherwise, the WF-500 appliance only forwards the malware report (and not the sample itself) to the WildFire public cloud.
The local WF-500 appliance is ideal for deployments with privacy and legal regulations that restrict the transfer of files outside your network. The WildFire-500 appliance queries the WildFire public cloud to obtain the verdict and, if unknown, analyzes the executable file in the local sandbox. By default, the WF-500 appliance does not send discovered malware outside your network, however, you can choose to automatically forward malware to the WildFire public cloud to generate and distribute signatures to all Palo Alto Networks firewalls with Threat Prevention and WildFire licenses. Otherwise, the WF-500 appliance only forwards the malware report (and not the sample itself) to the WildFire public cloud.
If WildFire integration is enabled in the ESM Console, the Status page
of the Traps Console displays a
![]() next to Forensic
Data Collection. If WildFire is not enabled, the Traps
Console displays an
next to Forensic
Data Collection. If WildFire is not enabled, the Traps
Console displays an
![]() next to Forensic
Data Collection.
next to Forensic
Data Collection.
For more information, see Set
Up the ESM to Communicate with WildFire and Malware
Protection Flow.