Enable Log Forwarding to Panorama
Table of Contents
Expand all | Collapse all
-
- Set Up the Endpoint Infrastructure
- Activate Traps Licenses
-
- Endpoint Infrastructure Installation Considerations
- TLS/SSL Encryption for Traps Components
- Configure the MS-SQL Server Database
- Install the Endpoint Security Manager Server Software
- Install the Endpoint Security Manager Console Software
- Manage Proxy Communication with the Endpoint Security Manager
- Load Balance Traffic to ESM Servers
-
- Malware Protection Policy Best Practices
- Malware Protection Flow
- Manage Trusted Signers
-
- Remove an Endpoint from the Health Page
- Install an End-of-Life Traps Agent Version
-
-
- Traps Troubleshooting Resources
- Traps and Endpoint Security Manager Processes
- ESM Tech Support File
-
- Access Cytool
- View the Status of the Agent Using Cytool
- View Processes Currently Protected by Traps Using Cytool
- Manage Logging of Traps Components Using Cytool
- Restore a Quarantined File Using Cytool
- View Statistics for a Protected Process Using Cytool
- View Details About the Traps Local Analysis Module Using Cy...
- View Hash Details About a File Using Cytool
Enable Log Forwarding to Panorama
To enable log forwarding to a Panorama log
collector, use the following workflow:
- Before you begin: If you are enabling SSL for secure syslog communication between Panorama and the ESM Server(s), you must Set Up Secure Communication with Panorama.
- To Configure a Panorama log collector to receiveESMandTraps
logs, first define the log ingestion profile on Panorama:
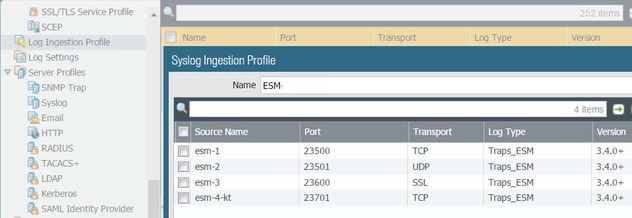
- Select PanoramaLog Ingestion Profile, and click Add.
- Enter a Name for the profile.
- Add a new profile and enter the details for the ESM Server. You can add up to four ESM Servers to a profile.
- Enter a Source Name.
- Specify the Port on which Panorama will be listening for syslog messages. The range is 23000 to 23999.
- Select the Transport layer protocol—TCP, UDP, or SSL.
- Select Traps_ESM for External Log type and 3.4.1+ from the Version drop-down.
![]() As Traps log formats are updated, the updated log definitions will be available through content updates on Panorama.
As Traps log formats are updated, the updated log definitions will be available through content updates on Panorama. - Attach the log ingestion profile to a Collector Group.
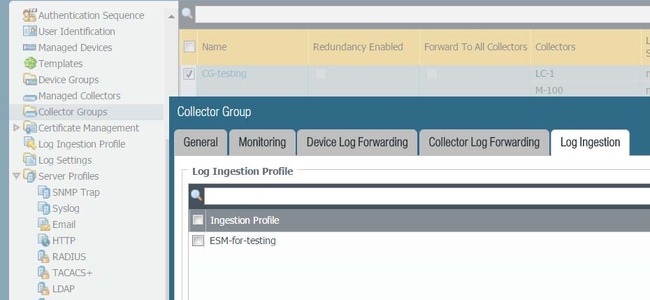
- Select PanoramaCollector GroupsLog Ingestion and Add the
log ingestion profile so that the Collector Group can receive logs
from the ESM Server(s) listed in the profile.If you are enabling SSL for secure syslog communication between Panorama and the ESM Server(s), verify that an Inbound Certificate for Secure Syslog is selected. For more information, see the Set Up Secure Communication with Panorama.
![]()
- Commit changes to Panorama and the Collector Group.
- Select PanoramaCollector GroupsLog Ingestion and Add the
log ingestion profile so that the Collector Group can receive logs
from the ESM Server(s) listed in the profile.
- Enable log forwarding to Panorama on the ESM Console.If you use a Panorama High Availability (HA) configuration, you can also specify the server and port information of the redundant server. Panorama in HA provides redundancy in the event of a system or network failure.
![]()
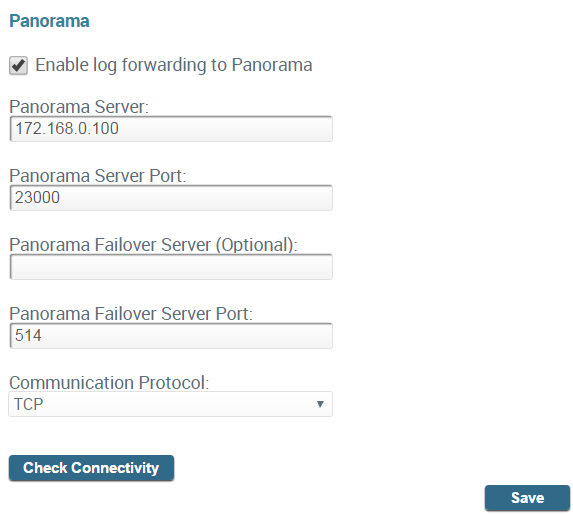
- From the ESM Console, select SettingsESMPanorama.
- Enable log forwarding to Panorama.
- Configure the following settings:
- Panorama Server—Hostname or IP address of the Panorama server.
- Panorama Server Port—Port on which Panorama will be listening for syslog messages.
- Panorama Failover Server (Optional)—Hostname or IP address of a secondary Panorama server.
- Panorama Failover Server Port—Port of the secondary Panorama on which Panorama will be listening for syslog messages.
- Communication Protocol—Transport layer protocol that the ESM uses to send logs to Panorama: TCP, TCP with SSL, or UDP. If you are enabling SSL for secure syslog communication between Panorama and the ESM Server(s), you must also import the Panorama root CA certificate on to the ESM Server as described in the following step.
- Click Save.
- Verify connectivity between the ESM and Panorama.Click Check Connectivity. The ESM Console sends a test communication to the external logging platform using the settings you configured. If you do not receive the test message, confirm that your settings are correct and then try again.