Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
5.2 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
-
- Allocate Licenses for Prisma Access (Managed by Strata Cloud Manager)
- Plan Service Connections for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Add Additional Locations for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Enable Available Add-ons for Prisma Access (Managed by Strata Cloud Manager)
- Search for Subscription Details
- Share a License for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Increase Subscription Allocation Quantity
-
- Activate a License for Prisma Access (Managed by Strata Cloud Manager) and Prisma SD-WAN Bundle
- Activate and Edit a License for SASE 5G Through Common Services
-
- Prisma Access Onboarding Workflow
-
2.2 Preferred
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
- Prisma Access China
-
- Prisma Access
- Prisma Access Infrastructure Management
- Releases and Upgrades
- Manage Upgrade Options for the GlobalProtect App
- Notifications and Alerts for Panorama, Cloud Services Plugin, and PAN-OS Dataplane Versions
- Retrieve the IP Addresses for Prisma Access
- Plan for IP Address Changes for Mobile Users, Remote Networks, and Service Connections
- Service IP and Egress IP Address Allocation for Remote Networks
- How to Calculate Remote Network Bandwidth
- Prisma Access APIs
- Use Logging, Routing, and EDL Information to Troubleshoot Your Deployment
-
- Set Up Prisma Access
- Plan the Service Infrastructure and Service Connections
- Configure the Service Infrastructure
- Create a Service Connection to Allow Access to Your Corporate Resources
- Create a Service Connection to Enable Access between Mobile Users and Remote Networks
- Deployment Progress and Status
- How BGP Advertises Mobile User IP Address Pools for Service Connections and Remote Network Connections
- Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
- Routing Preferences for Service Connection Traffic
- Create a High-Bandwidth Network Using Multiple Service Connections
- List of Prisma Access Locations
-
- Plan To Deploy Prisma Access for Mobile Users
- Secure Mobile Users With GlobalProtect
- Secure Mobile Users with an Explicit Proxy
- Zone Mapping
- Specify IP Address Pools for Mobile Users
- How the GlobalProtect App Selects a Prisma Access Location for Mobile Users
- View Logged In User Information and Log Out Current Users
-
- Use Explicit Proxy to Secure Public Apps and GlobalProtect or a Third-Party VPN to Secure Private Apps
- Prisma Access with On-Premises Gateways
-
- Set Equal Gateway Priorities for On-Premises and Prisma Access Gateways
- Set a Higher Gateway Priority for an On-Premises Gateway
- Set Higher Priorities for Multiple On-Premises Gateways
- Configure Priorities for Prisma Access and On-Premises Gateways
- Allow Mobile Users to Manually Select Specific Prisma Access Gateways
- DNS Resolution for Mobile Users—GlobalProtect and Remote Network Deployments
- IPv6 Support for Private App Access
- Sinkhole IPv6 Traffic In Mobile Users—GlobalProtect Deployments
- Identification and Quarantine of Compromised Devices With Prisma Access
- Support for Gzip Encoding in Clientless VPN
- Report Website Access Issues
-
- Plan to Deploy Remote Networks
- Onboard and Configure Remote Networks
-
- Remote Network Locations with Overlapping Subnets
- Remote Network Locations with WAN Link
- Use Predefined IPSec Templates to Onboard Service and Remote Network Connections
- Onboard Remote Networks with Configuration Import
- Configure Quality of Service in Prisma Access
- Create a High-Bandwidth Network for a Remote Site
- Provide Secure Inbound Access to Remote Network Locations
-
- Multitenancy Overview
- Multitenancy Configuration Overview
- Enable Multitenancy and Migrate the First Tenant
- Add Tenants to Prisma Access
- Delete a Tenant
- Create a Tenant-Level Administrative User
- Control Role-Based Access for Tenant-Level Administrative Users
- Sort Logs by Device Group ID for External Logging
- Visibility and Monitoring Features in the Prisma Access App
-
- Integrate Prisma Access With Other Palo Alto Networks Apps
- Integrate Third-Party Enterprise Browser with Explicit Proxy
- Integrate Third-Party NDRs with Prisma Access
- Juniper Mist Integration for SASE Health
-
-
- Connect your Mobile Users in Mainland China to Prisma Access Overview
- Configure Prisma Access for Mobile Users in China
- Configure Real-Name Registration and Create the VPCs in Alibaba Cloud
- Attach the CEN and Specify the Bandwidth
- Create Linux Instances in the Alibaba Cloud VPCs
- Configure the Router Instances
- Onboard the GlobalProtect Gateway and Configure the Prisma Access Portal
-
-
-
- INC_CIE_AGENT_DISCONNECT
- INC_CIE_DIRECTORY_DISCONNECT
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_MU_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_MU_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_DNS_SERVER_UNREACHABLE_ PER_PA_LOCATION
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_RN_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_DNS_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_ECMP_TUNNEL_RTT_EXCEEDED_ BASELINE
- INC_RN_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SECONDARY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SITE_CAPACITY_PREDICTION
- INC_SC_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SITE_CAPACITY_PREDICTION
-
- INC_CERTIFICATE_EXPIRY
- INC_GP_CLIENT_VERSION_UNSUPPORTED
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_CAPACITY
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_THRESHOLD
- INC_PA_INFRA_DEGRADATION
- INC_PA_SERVICE_DEGRADATION_PA_LOCATION
- INC_PA_SERVICE_DEGRADATION_RN_ SITE_CONNECTIVITY
- INC_PA_SERVICE_DEGRADATION_SC_ CONNECTIVITY
- INC_RN_ECMP_BGP_DOWN
- INC_RN_ECMP_BGP_FLAP
- INC_RN_ECMP_PROXY_TUNNEL_DOWN
- INC_RN_ECMP_PROXY_TUNNEL_FLAP
- INC_RN_ECMP_TUNNEL_DOWN
- INC_RN_ECMP_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_BGP_FLAP
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_BGP_DOWN
- INC_RN_SECONDARY_WAN_BGP_FLAP
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_FLAP
- INC_RN_SITE_DOWN
- INC_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_RN_SPN_LONG_DURATION_CAPACITY_EXCEEDED _THRESHOLD
- INC_RN_SPN_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_SC_PRIMARY_WAN_BGP_DOWN
- INC_SC_PRIMARY_WAN_BGP_FLAP
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_PRIMARY_WAN_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_BGP_DOWN
- INC_SC_SECONDARY_WAN_BGP_FLAP
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_TUNNEL_FLAP
- INC_SC_SITE_DOWN
- INC_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_SC_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- INC_ZTNA_CONNECTOR_CPU_HIGH
- INC_ZTNA_CONNECTOR_MEMORY_HIGH
- INC_ZTNA_CONNECTOR_TUNNEL_DOWN
-
- AL_CIE_AGENT_DISCONNECT
- AL_CIE_DIRECTORY_DISCONNECT
- AL_MU_IP_POOL_CAPACITY
- AL_MU_IP_POOL_USAGE
- AL_RN_ECMP_BGP_DOWN
- AL_RN_ECMP_BGP_FLAP
- AL_RN_PRIMARY_WAN_BGP_DOWN
- AL_RN_PRIMARY_WAN_BGP_FLAP
- AL_RN_PRIMARY_WAN_TUNNEL_DOWN
- AL_RN_PRIMARY_WAN_TUNNEL_FLAP
- AL_RN_SECONDARY_WAN_BGP_DOWN
- AL_RN_SECONDARY_WAN_BGP_FLAP
- AL_RN_SECONDARY_WAN_TUNNEL_DOWN
- AL_RN_SECONDARY_WAN_TUNNEL_FLAP
- AL_RN_SITE_DOWN
- AL_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- AL_RN_SPN_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_PRIMARY_WAN_BGP_DOWN
- AL_SC_PRIMARY_WAN_BGP_FLAP
- AL_SC_PRIMARY_WAN_TUNNEL_DOWN
- AL_SC_PRIMARY_WAN_TUNNEL_FLAP
- AL_SC_SECONDARY_WAN_BGP_DOWN
- AL_SC_SECONDARY_WAN_BGP_FLAP
- AL_SC_SECONDARY_WAN_TUNNEL_DOWN
- AL_SC_SECONDARY_WAN_TUNNEL_FLAP
- AL_SC_SITE_DOWN
- AL_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_SITE_LONG_DURATION_EXCEEDED_CAPACITY
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- AL_ZTNA_CONNECTOR_CPU_HIGH
- AL_ZTNA_CONNECTOR_MEMORY_HIGH
- AL_ZTNA_CONNECTOR_TUNNEL_DOWN
- New Features in Incidents and Alerts
- Known Issues
Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
Use traffic steering and default routing to steer internet-bound
traffic to specific service connections.
Prisma Access allows you to create traffic
steering rules to specify targets for internet-bound traffic from
mobile users and remote network connections. You can specify the
traffic to be redirected to a service connection before sending
to the internet, or you can specify the traffic to directly egress
to the internet. This functionality is known as Traffic Steering.
Alternatively,
you can configure Prisma Access to accept a
default route
from
your CPE to Prisma Access so that Prisma Access forwards internet-bound
mobile user traffic to the best service connection in your deployment.The
following sections provide an overview of default routes and traffic
steering, as well as the steps you take to configure it.
- Default Routes
- Traffic Steering
- Traffic Steering Requirements
- Traffic Steering Examples
- Traffic Steering Rule Guidelines
- Zone Mapping and Security Policies for Dedicated Connections
- Configure Traffic Steering
Default Routes
Use Prisma Access’ default route capability
to accept default routes being advertised from your CPE to service
connections. You can use BGP or static routes to advertise the default route.
Prisma Access uses BGP to advertise these routes over multiple service
connections, which allows Prisma Access to route mobile user traffic
through the best service connection for a given mobile user location.
To enable service connections to accept default routes, specify Accept
Default Route over Service Connections when you
configure global settings for service
connections
. After you enable default routes, your
internet-bound traffic will be steered to service connections instead
of egressing from the mobile user locations. This functionality
can be useful if you want to redirect internet-bound traffic to
the data center; for example, if you have a third-party security
stack in your data center and you want the stack to perform additional
screening or inspection.
Use the following guidelines when
implementing default routes:
- Default routes apply to mobile user deployments only; remote network connections operate normally with no change when you enable default routes.
- You do not need to specify target service connections or traffic steering rules when you allow default routes, although they are supported for use with default routes. SeeTraffic Steering Examplesfor examples of using default routes with traffic steering.
- When you specify the Accept Default Route over Service Connections setting, all Prisma Access service connections, with the exception of dedicated service connections, accept default routes and will use the routes in traffic steering decisions.
- Before you enable this setting, make sure that your data centers are sending default routes; otherwise, routing through service connections will fail.
- Palo Alto Networks recommends that all data centers advertise a default route; when Prisma Access receives the routes, it can then select the best service connection to use for the remote network location.
- When you create service connections, use either static routes only or BGP only for the connections. Palo Alto Networks does not recommend mixing service connections that use BGP and static routes when using default routes.
- Using default routes is supported with multitenant deployments.
- Prisma Access does not forward Clientless VPN, portal, or gateway SAML authentication traffic to a public identity provider (IdP) using the default route.
For more information
and examples of implementing default routes with traffic steering,
see
Traffic Steering Examples
.Traffic Steering
In standard Prisma Access deployments, a service
connection provides access to internal network resources, such as
authentication services and private apps in your headquarters or data
center. Service connections process internal traffic, where no internet
access is required. In some cases, you might want to redirect internet-bound
traffic to the data center. Traffic steering allows you to redirect
mobile user or remote network traffic to a service connection before
being sent to the internet.
You can use traffic steering with
mobile user deployments, remote network deployments, or a combination
of both. Use traffic steering to direct internet-bound network traffic
based on many criteria including IP addresses, Custom URL categories,
service type (HTTP or HTTPS), User-ID, Dynamic Address Groups (DAGs) and
IP-based External Dynamic Lists (EDLs).
There
are two action types supported with traffic steering:
- Forward to the target—Use the criteria in traffic steering rules to forward internet-bound traffic through a target you create that uses one or more service connections.
- Forward to the internet—Use the criteria in traffic steering rules to directly forward traffic from its source (mobile user location or remote network connection) to the internet, without being forwarded to a service connection.
If
you forward to a target, you can choose to create two types of target
groups: dedicated and non-dedicated.
- A service connection that is used only for traffic steering-related traffic is a dedicated service connection. To set a service connection to be used as a dedicated service connection, select Dedicated for Traffic Steering Only when youconfigure traffic steeringin Panorama.You might want to configure a dedicated service connection if you use a third-party security stack that is outside of your organization’s internal network to process traffic before it is sent to a public SaaS application or the internet. Because the security stack is not a part of your organization’s network, you don’t want this service connection to process any internal network traffic.
- A service connection that is used for traffic steering and for standard service connection-related traffic (such as traffic going to an authentication server in the data center) is a non-dedicated service connection.
Setting a service connection
as a dedicated service connection causes the following changes to
your deployment:
- The zone for all service connections associated with this target changes from Trust to Untrust. Check your zone mapping andsecurity policiesto make sure that your network reflects this change.
- Service connections that are configured as dedicated service connections do not participate in BGP routing, either internally or externally.
- If your dedicated service connection uses BGP, the BGP status shows as Not Enabled when you open the status page (PanoramaCloud ServiceStatusMonitorService Connection), select a region, then select the Status tab. To check the BGP status of a service connection, check the service connections configuration page (PanoramaCloud ServicesConfigurationService Connection).
- By default, the service connections apply source NAT to the forwarded traffic. The source IP address is the User-ID Agent Address of the service connection (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionUser-ID Agent Address), which is taken from the Infrastructure Subnet (PanoramaCloud ServicesStatusNetwork DetailsService Infrastructure).You can disable source NAT and use your organization’s source IP addresses for the dedicated service connection; to do so, select Disable Source NAT for Dedicated SC when you Add a target in the Target Service Connections for Traffic Steering area.
Traffic Steering Requirements
Before you implement traffic steering in your
Prisma Access deployment, make sure that your network environment
has the following infrastructure requirements:
- Prisma Access must be able to connect to the IPSec-capable CPE (such as a router or SD-WAN device) that your organization uses to terminate the service connection, and the IP address for the device must be reachable from Prisma Access.You create a service connection using standard IPSec and IKE cryptographic profiles between the stack location and Prisma Access. You can use static routes, BGP, or a combination or both when you create a service connection and use traffic steering. If you use default routes with traffic steering, Palo Alto Networks recommends that you use either BGP only or static routes only. If you use static routing, specify the public IP address used by the organization’s CPE as the Peer Address when you create an IKE gateway.
- Prisma Access might not match the first few packets of a URL from a URL category in a traffic steering rule, which means that the first few packets of a network session (for example, a TCP handshake) might not match the rule. Palo Alto Networks recommends that, for URLs you use in traffic steering rules, you create a security policy rule to allow them through the Untrust zone so that the handshake can complete when a new session begins.
- If you are using this configuration with a security stack, the stack location must be reachable from the service connection by a standard IPSec tunnel configuration.
Use the
following guidelines when configuring traffic steering:
- You can specify up to 1,000 URLs (aggregated) in a traffic steering configuration, including regular and wildcard (*.example.com) URLs in custom URL categories.
- Prisma Access prepends an asterisk to URLs in custom URL categories, if you use this category in a traffic steering rule. If you use the same URL category policies for both traffic steering and other security policy rules, these changes apply to both the traffic steering rules and other security policy rules.If you have custom URL categories that are not used in traffic steering rules, Prisma Access does not change the URLs in those categories.
- Use all lower-case URLs when you enter URLs in a custom URL category.
- You can configure a maximum of 100 traffic steering rules.
- If you have primary and backup tunnels configured, traffic steering using traffic steering rules will not work after a failover from the primary (active) to the backup tunnel.Default routingworks in a failover scenario with primary and backup tunnels.
Traffic Steering Examples
The following sections describes different
types of traffic steering deployments.
Default Route Example
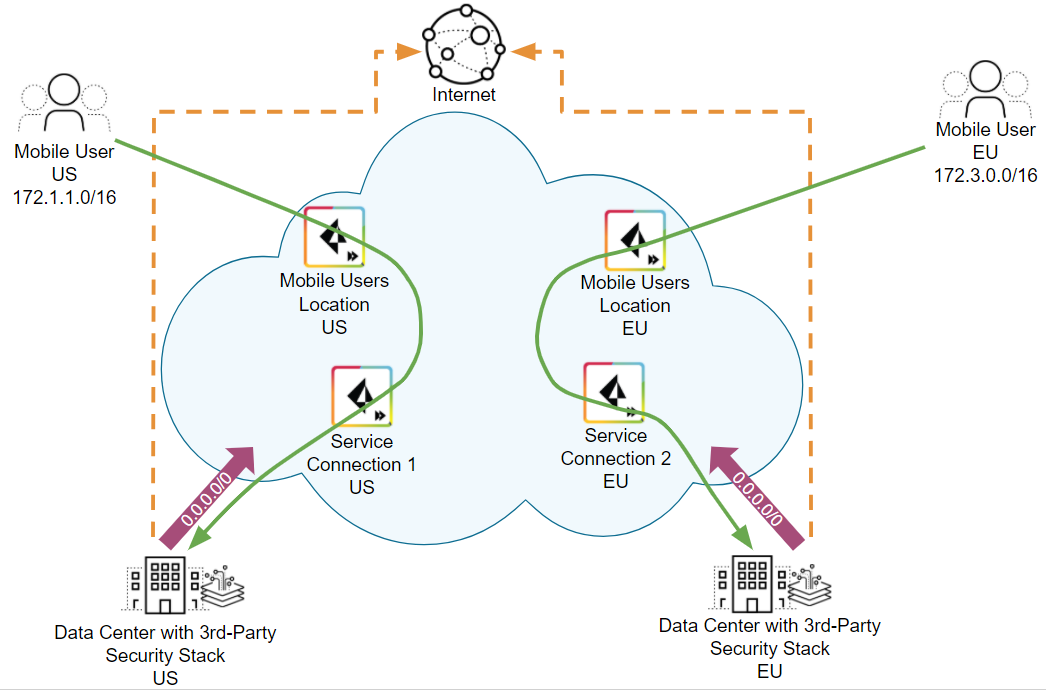
The following example shows a sample Prisma
Access deployment the following components:
- Two Prisma Access mobile user locations; one in the United States (US) and one in Europe (EU).
- Two Prisma Access service connections; one in the US and one in the EU, with both data centers sending default routes to the service connections (Accept Default Route over Service Connections is enabled).
- Two data centers; one in the US and one in the EU.Each data center has a 3rd-party security stack; for this reason, you want all internet-bound traffic to go through the data center before egressing to the internet.
When a mobile user sends
data center traffic, Prisma Access checks its routing tables, determines the
closest service connection, and forwards the traffic to that service
connection. In the following example, Prisma Access sends data center
traffic from the mobile users in the US to Service Connection and
traffic from the mobile users in the EU to Service Connection 2.
Use
non-dedicated service connections with default routes; dedicated
service connections do not participate in BGP routing, so they cannot
receive BGP advertisements from the HQ or data center.
To
enable default routes, select Accept Default Route over
Service Connections when you configure traffic steering
settings. After you configure this setting and commit and push your
changes, Prisma Access sends internet-bound traffic over the service
connections.
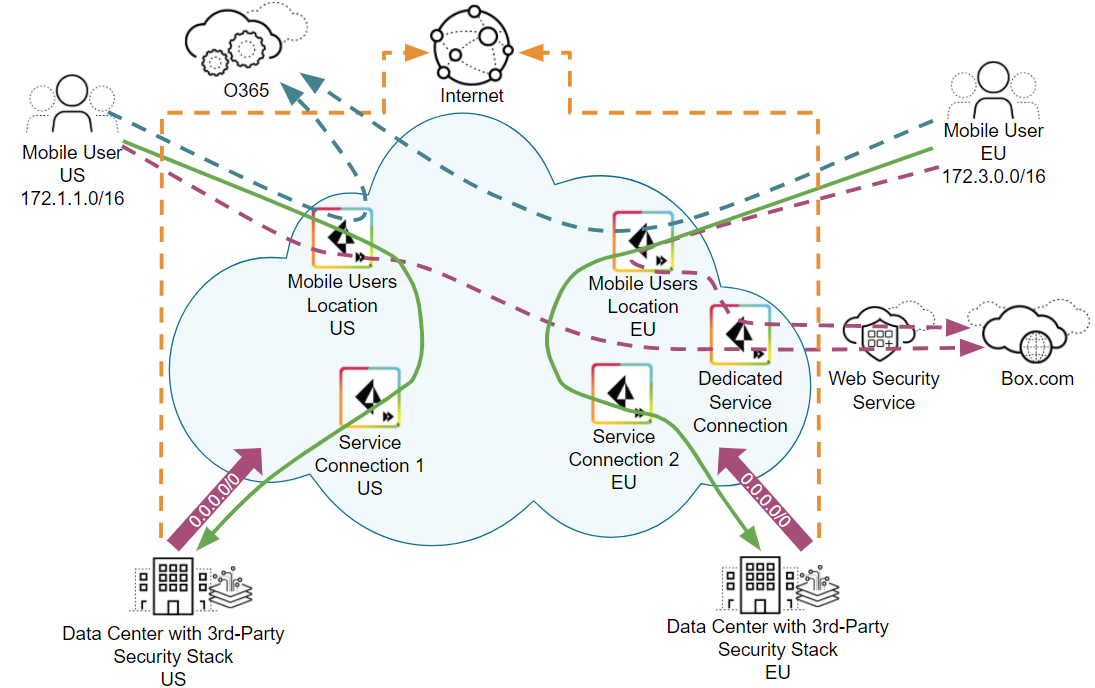
Default Routes with Traffic Steering Direct to Internet Example
The following example shows you using more
granular control for external SaaS application-bound traffic. In
this case, you want to send Office 365 traffic to egress to the
internet directly from the mobile user location, instead of sending
it to the data center for further processing. Use traffic steering
along with default routes for this configuration.

To
allow Prisma Access to route Office 365 traffic directly to the
internet, perform the following actions:
- Create an EDL (ObjectExternal Dynamic Lists) with IP addresses that match the Office 365 addresses.
- Create a Custom URL category (ObjectsCustom ObjectsURL Category) with URLs that match Office 365 URL.
- createcreate traffic forwarding rulesand specify the EDL and URL category you created as destination match criteria with an Action of Forward to the internet.
This configuration sends
Office 365 traffic directly to the internet, while other internet-bound
traffic is sent to the data center for further processing before
egressing to the internet.

Default Routes with Traffic Steering and Dedicated Service Connection Example
In this example, in addition to the previous
configuration, you have a third-party internet security service,
and you want to send traffic from box.com to be processed by the security
service before egressing to the internet. You do not want to send
any other internet-bound traffic to the security service; for this
reason, you create a dedicated service connection for the box.com
traffic. After your configuration is complete, Prisma Access sends
*.box.com destination traffic to the stack.
To
enable this deployment, you perform the following actions in the
Traffic Steering tab:
- Create a Target Service Connection group that assigns one or more service connections to the target and select Dedicated for Traffic Steering Only, which makes the target service connection or connections dedicated.If you create a target with more than one service connection, Prisma Access chooses the best service connection to forward the internet-bound traffic.

- Create a traffic steering rule that forwards traffic to the URL. The following screenshot shows the traffic destination being assigned a custom URL category that contains the URL *.box.com.

- Create an Action in the traffic steering rule of Forward to the target and specify the target group name you created (dedicated in this case).

Traffic Steering Rule Guidelines
Traffic steering can process a wide variety
of possible configurations; however, it is important to understand
how Prisma Access processes rules, so you can create rules are easy
to maintain and manage. To help you create the rules that work best
for your deployment, follow these guidelines:
- Prisma Access evaluates rules in the order that you create them (from top to bottom). Specify more specific rules at the top and more general rules at the bottom.
- Palo Alto Networks recommends that you create multiple rules with fewer matching criteria, instead of creating fewer rules with multiple types of criteria. Creating simpler rules both speeds up rule creation and makes it easier to modify a rule.
- Since you cannot move a rule up or down in a list after you create it, carefully plan your rule order before you create the rules.
- Rules that specify Any source address and User, Any source destination and URL Category, and Any service are not supported. Use more specific rules; for example, specify a rule with Any source or destination traffic and a service of service-http and service-https.
- If you are going to specify rules for users in the Source User field, make sure that Prisma Access can distinguish between users if the same username is shared between users who authenticate locally and users who authenticate using LDAP by authenticating LDAP users in the format of domain/username and authenticating local users in the format of username (without the domain name).
- If you have configured an on-premises next-generation firewall as a master device, you can auto-populate user and group information for mobile user device groups in traffic steering and security policy rules by selecting PanoramaCloud ServicesConfigurationMobile Users, clicking the gear icon to edit the Settings, and selecting the Master Device in the Device Group area. While this populates the master device in every device group, it only populates the user and group information for mobile users in security policy rules.
- If an EDL (type IP List) is used in a Traffic Steering Rule, and the EDL source URL of the EDL is updated to a URL that is not accessible, Prisma Access may continue to use the cached IP list from the previous URL.
- Prisma Access bypasses Traffic Steering for rules with a service type of HTTP or HTTPS if you use an application override policy for TCP ports 80 and 443.In addition, traffic steering does not work for URLs from URL categories referenced in the traffic steering rule if you have configured an application override policy for TCP ports 80 or 443.
- You can specify destination IP addresses and URL categories in the same rule. If you do, Prisma Access uses a logical OR to process the destination criteria in the rule, but processes the URLs and URL category traffic based on TCP ports 80 and 8080 for HTTP and TCP port 443 for HTTPS.For a rule with IP addresses and URL categories, traffic matches the rule if either the IP address or the URL category matches, but processes the URL category traffic based on ports 80, 443, and 8080 only. Palo Alto Networks does not recommend creating a rule of this type; instead, create simpler rules.
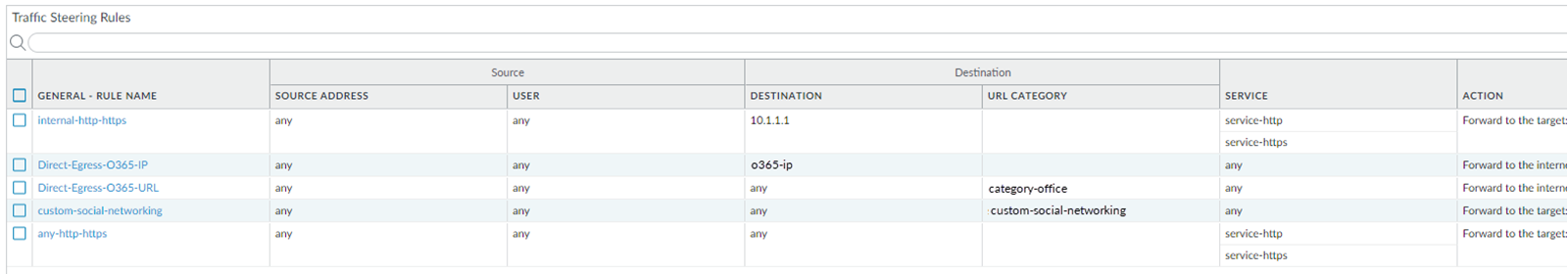
For example, you
want to enforce the following rules for your network traffic:
- You have an internal HTTP server with an IP address of 10.1.1.1 in the data center, and you want to direct internal HTTP and HTTPS traffic to this server. The IP address of the server is 10.1.1.1.Traffic to this server should not go to the internet and should be processed internally; therefore, choose a non-dedicated target for this traffic, because this type of target processes both internal and internet-bound traffic.
- You want office365.com traffic to be routed directly to the internet.
- You want traffic from *.example.com or any traffic defined in a custom URL category of custom-social-networking to be routed to a dedicated connection.
- You want any other HTTP and HTTPS traffic to use the same non-dedicated service connection target as that used for the internal HTTP server.
For this example, create the rules
from the most specific to the least specific, as shown in the following
screenshot. Do not add the rule that allows all HTTP and HTTPS traffic
first, or Prisma Access would direct all HTTP and HTTPS traffic
to the non-dedicated connection without evaluating any of the other
rules.
Zone Mapping and Security Policies for Dedicated Connections
If you create a target that uses a dedicated
service connection, the zone for the dedicated service connection
changes from Trust to Untrust (non-dedicated
service connection targets do not change their zones). Since you
cannot create zones or configure zone mapping for service connections,
you make zone mapping and security policy changes
for dedicated service connections to the mobile users and device
groups instead. Complete the following steps to configure zone mapping
for dedicated connections.
These steps show a sample
configuration; you can tailor this example to suit your deployment.
- Select NetworkZones.
- Select the correct Template from the drop-down list (either Mobile_User_Template for mobile users or Remote_Network_Template for remote networks).If you have a mobile user and a remote network deployment, you need to perform these steps twice; once in the Mobile_User_Template and once in the Remote_Network_Template.
- Add two zones for your trusted and untrusted zones.This example creates two zones called Trust and Untrust.

- Create default policies for the zones you created.
- Select PoliciesSecurityPost Rules.
- Select the correct Device Group from the drop-down list (either Mobile_User_Device_Group for remote networks or Remote_Network_Device_Group for mobile users).If you have a mobile user and remote network deployment, you need to perform these steps twice; once in the Mobile_User_Device_Group and once in the Remote_Network_Device_Group.
- Add a default policy to use for Trust zone-to-Trust zone traffic.This policy allows Any traffic to pass for all Source, User, Destination, Application, and Service/URL Category traffic.

- Add a default policy to use for Trust zone-to-Untrust zone traffic, using the same parameters you used for the Trust-to-Trust policy.When complete, you have two security policies, one for Trust-to-Trust traffic and one for Trust-to-Untrust traffic.

- Define Zone Mapping for the remote networks, mobile users, or both, as required for your deployment.
- Set the zone mapping for the remote networks, mobile users, or both.
- For mobile users, select PanoramaCloud ServicesConfigurationMobile Users.
- For remote networks, select PanoramaCloud ServicesConfigurationRemote Networks.
- Click the gear icon next to Zone Mapping to edit the settings.

- Set the Zone Mapping for your deployment, moving the zone for trusted traffic to the Trusted Zones and the zone for untrusted traffic to the Untrusted Zones; then, click OK.

Configure Traffic Steering
Configure traffic steering for your deployment
by completing the following steps.
- Onboard your service connections, mobile users and remote networks, as applicable to your deployment.
- Select PanoramaCloud ServicesConfigurationTraffic Steering.
- (Optional, mobile user deployments only) Allow Prisma Access to accept and install the default route advertised over one or more service connections from the CPE by clicking the gear icon to open the Settings and selecting Accept Default Route over Service Connections.Default routes havespecific guidelinesthat you must follow when using them; for example, default routes are supported for mobile user deployments only and have no effect on remote network deployments. Be sure to review these guidelines before implementing default routes with traffic steering.

- (Optional) Create a target group and assign a service connection to it.
- In the Target Service Connections for Traffic Steering area, Add a group and give it a Group Name.
- Add a Target for the traffic, specifying the Service Connection to use with the target; then, click OK.Palo Alto Networks does not recommend using multiple service connections (whether dedicated or non-dedicated) in a target service connection group that is referenced in a traffic steering rule. In addition, a given service connection can only exist in one target and you cannot add a single service connection to two different targets.
- Choose whether to make the service connections associated with this target a dedicated service connection.
- You can use a dedicated service connection to steer traffic to a third-party security stack or cloud that is not on your premises and does not need to participate in routing. To set a service connection to be used as a dedicated service connection, select Dedicated for Traffic Steering Only.Dedicated service connections change their zones; seeTraffic Steeringfor details.
- Deselect Dedicated for Traffic Steering Only if you will send both normal service connection-related and traffic steering traffic through the service connection; with this choice, the zone for the service connection remains as Trust.
- Choose whether to enable or disable source NAT.To disable source NAT for Dedicated service connections, select Disable Source NAT for Dedicated SC. Source NAT is enabled by default (the check box is deselected).If you disable source NAT, Prisma Access uses your organization’s source IP addresses for the dedicated service connection. If you enable source NAT, Prisma Access uses the EBGP Router address of the service connection (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionEBGP Router) as the source IP address, even after the traffic egresses from the dedicated service connection.

- Create rules for the target you created and apply them to the target.
- In the Traffic Steering Rules area, Add a traffic steering rule.
- in the General tab, Name the traffic steering rule.
- In the Source tab, specify rules for source traffic.
- In the Source Address field, specify one or more of the following objects, or select Any to have traffic from any source go to this target:
- An IP address
- An address object that you created in Panorama (ObjectsAddresses)
- An External Dynamic List (EDL) using IP addresses or URLs
- In the Source User field, specify rules for source user traffic. You can specify the following user information:
- UsersEnter users in either the domain/user or the user@domain format.
- User groupsUse full distinguished names (DNs) when entering user groups.
- Users configured on Panorama (DeviceLocal User DatabaseUsers)
- User groups configured on Panorama (DeviceLocal User DatabaseUser Groups)
If you use address objects, DAGs, EDLs, users, or user groups, specify them as Shared to share them with all device groups in Prisma Access. In addition, do not enter 0.0.0.0/0 in address objects, DAGs, or EDLs; instead, enter 0.0.0.0/0 directly in the rule.Prisma Access automatically populates users from the mobile users device group only. - In the Destination tab, specify the following values:
- In the Destination area, specify one of the following criteria, or select Any to have traffic processed by the rules in the URL Category field:
- An IP address or prefix
- An address object that you created in Panorama (ObjectsAddresses)
- An IP address-based External Dynamic List (EDL)
Do not enter 0.0.0.0/0 in address objects, DAGs, or EDLs; instead, enter 0.0.0.0/0 directly in the rule.Leave Any selected to pass all traffic to be processed by the rules in the URL Category area. If you specify rules in the Destination, and URL Category areas, Prisma Access processes the rules in the Destination category first. - In the URL Category field, enter a custom URL category (ObjectsCustom ObjectsURL Category) When you create a custom URL category, enter URLs in all lower case. Traffic steering supports custom URL and predefined URL categories.You can use wildcards with the URLs in URL categories. The following wildcard formats are supported:
- *.example.com
- *.fqdn.example.com
The following formats are not supported:- *
- *.*
- *example.com
- example.com/ (trailing slashes in URLs are not supported in URL categories that are used with Traffic Steering)
- example.com/path (only domain names are supported)
- *fqdn.example.com
- fqdn.example.*
URLs in custom URL categories use the same URL pattern matching as that used by next-generation firewalls.
Use the following guidelines when configuring destination options:- If you specify a URL category, Prisma Access only matches HTTP and HTTPS traffic, even when service is set to Any.
- Do not create a custom URL category with a type of Category Match.
- Do not create a custom URL category with the name Custom_URL_Category_TFR because, for deployments that are migrated from Prisma Access 1.7 to 2.0, URLs entered in the URL area from 1.7 are moved to a custom URL category named Custom_URL_Category_TFRnumber, where number is a number appended to the custom URL category.

- In the Service tab, specify a service type.Specify service-http to forward HTTP traffic and specify service-https to specify HTTPS traffic. Select Any to forward traffic of any service type.
- In the Action tab, select the Target Group Name that you want to apply to the traffic steering rule.
- Forward traffic to the specified service connection target, or send the traffic directly to the internet without going through the service connection.
- To have Prisma Access forward traffic to a service connection target, select Forward to the target; then select the Target Group Name.
- To have Prisma Access forward traffic directly to the internet without first sending it to a service connection, select Forward to the internet.

- Click OK to save your changes.
- Optional Specify additional traffic steering rules.Prisma Access processes multiple rules in the order that you create them (from top to bottom).
- Commit and push your changes to make them active in Prisma Access.
- Select CommitCommit and Push and Edit Selections in the Push Scope.
- Select Prisma Access, then select Service Setup, Remote Networks, and Mobile Users.

- Click OK to save your changes to the Push Scope.
- Commit and Push your changes.












