Plan for IP Address Changes for Mobile Users, Remote Networks, and Service Connections
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
5.2 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
-
- Allocate Licenses for Prisma Access (Managed by Strata Cloud Manager)
- Plan Service Connections for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Add Additional Locations for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Enable Available Add-ons for Prisma Access (Managed by Strata Cloud Manager)
- Search for Subscription Details
- Share a License for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Increase Subscription Allocation Quantity
-
- Activate a License for Prisma Access (Managed by Strata Cloud Manager) and Prisma SD-WAN Bundle
- Activate and Edit a License for SASE 5G Through Common Services
-
- Prisma Access Onboarding Workflow
-
2.2 Preferred
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
- Prisma Access China
-
- Prisma Access
- Prisma Access Infrastructure Management
- Releases and Upgrades
- Manage Upgrade Options for the GlobalProtect App
- Notifications and Alerts for Panorama, Cloud Services Plugin, and PAN-OS Dataplane Versions
- Retrieve the IP Addresses for Prisma Access
- Plan for IP Address Changes for Mobile Users, Remote Networks, and Service Connections
- Service IP and Egress IP Address Allocation for Remote Networks
- How to Calculate Remote Network Bandwidth
- Prisma Access APIs
- Use Logging, Routing, and EDL Information to Troubleshoot Your Deployment
-
- Set Up Prisma Access
- Plan the Service Infrastructure and Service Connections
- Configure the Service Infrastructure
- Create a Service Connection to Allow Access to Your Corporate Resources
- Create a Service Connection to Enable Access between Mobile Users and Remote Networks
- Deployment Progress and Status
- How BGP Advertises Mobile User IP Address Pools for Service Connections and Remote Network Connections
- Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
- Routing Preferences for Service Connection Traffic
- Create a High-Bandwidth Network Using Multiple Service Connections
- List of Prisma Access Locations
-
- Plan To Deploy Prisma Access for Mobile Users
- Secure Mobile Users With GlobalProtect
- Secure Mobile Users with an Explicit Proxy
- Zone Mapping
- Specify IP Address Pools for Mobile Users
- How the GlobalProtect App Selects a Prisma Access Location for Mobile Users
- View Logged In User Information and Log Out Current Users
-
- Use Explicit Proxy to Secure Public Apps and GlobalProtect or a Third-Party VPN to Secure Private Apps
- Prisma Access with On-Premises Gateways
-
- Set Equal Gateway Priorities for On-Premises and Prisma Access Gateways
- Set a Higher Gateway Priority for an On-Premises Gateway
- Set Higher Priorities for Multiple On-Premises Gateways
- Configure Priorities for Prisma Access and On-Premises Gateways
- Allow Mobile Users to Manually Select Specific Prisma Access Gateways
- DNS Resolution for Mobile Users—GlobalProtect and Remote Network Deployments
- IPv6 Support for Private App Access
- Sinkhole IPv6 Traffic In Mobile Users—GlobalProtect Deployments
- Identification and Quarantine of Compromised Devices With Prisma Access
- Support for Gzip Encoding in Clientless VPN
- Report Website Access Issues
-
- Plan to Deploy Remote Networks
- Onboard and Configure Remote Networks
-
- Remote Network Locations with Overlapping Subnets
- Remote Network Locations with WAN Link
- Use Predefined IPSec Templates to Onboard Service and Remote Network Connections
- Onboard Remote Networks with Configuration Import
- Configure Quality of Service in Prisma Access
- Create a High-Bandwidth Network for a Remote Site
- Provide Secure Inbound Access to Remote Network Locations
-
- Multitenancy Overview
- Multitenancy Configuration Overview
- Enable Multitenancy and Migrate the First Tenant
- Add Tenants to Prisma Access
- Delete a Tenant
- Create a Tenant-Level Administrative User
- Control Role-Based Access for Tenant-Level Administrative Users
- Sort Logs by Device Group ID for External Logging
- Visibility and Monitoring Features in the Prisma Access App
-
- Integrate Prisma Access With Other Palo Alto Networks Apps
- Integrate Third-Party Enterprise Browser with Explicit Proxy
- Integrate Third-Party NDRs with Prisma Access
- Juniper Mist Integration for SASE Health
-
-
- Connect your Mobile Users in Mainland China to Prisma Access Overview
- Configure Prisma Access for Mobile Users in China
- Configure Real-Name Registration and Create the VPCs in Alibaba Cloud
- Attach the CEN and Specify the Bandwidth
- Create Linux Instances in the Alibaba Cloud VPCs
- Configure the Router Instances
- Onboard the GlobalProtect Gateway and Configure the Prisma Access Portal
-
-
-
- INC_CIE_AGENT_DISCONNECT
- INC_CIE_DIRECTORY_DISCONNECT
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_MU_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_MU_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_DNS_SERVER_UNREACHABLE_ PER_PA_LOCATION
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_RN_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_DNS_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_ECMP_TUNNEL_RTT_EXCEEDED_ BASELINE
- INC_RN_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SECONDARY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SITE_CAPACITY_PREDICTION
- INC_SC_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SITE_CAPACITY_PREDICTION
-
- INC_CERTIFICATE_EXPIRY
- INC_GP_CLIENT_VERSION_UNSUPPORTED
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_CAPACITY
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_THRESHOLD
- INC_PA_INFRA_DEGRADATION
- INC_PA_SERVICE_DEGRADATION_PA_LOCATION
- INC_PA_SERVICE_DEGRADATION_RN_ SITE_CONNECTIVITY
- INC_PA_SERVICE_DEGRADATION_SC_ CONNECTIVITY
- INC_RN_ECMP_BGP_DOWN
- INC_RN_ECMP_BGP_FLAP
- INC_RN_ECMP_PROXY_TUNNEL_DOWN
- INC_RN_ECMP_PROXY_TUNNEL_FLAP
- INC_RN_ECMP_TUNNEL_DOWN
- INC_RN_ECMP_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_BGP_FLAP
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_BGP_DOWN
- INC_RN_SECONDARY_WAN_BGP_FLAP
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_FLAP
- INC_RN_SITE_DOWN
- INC_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_RN_SPN_LONG_DURATION_CAPACITY_EXCEEDED _THRESHOLD
- INC_RN_SPN_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_SC_PRIMARY_WAN_BGP_DOWN
- INC_SC_PRIMARY_WAN_BGP_FLAP
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_PRIMARY_WAN_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_BGP_DOWN
- INC_SC_SECONDARY_WAN_BGP_FLAP
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_TUNNEL_FLAP
- INC_SC_SITE_DOWN
- INC_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_SC_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- INC_ZTNA_CONNECTOR_CPU_HIGH
- INC_ZTNA_CONNECTOR_MEMORY_HIGH
- INC_ZTNA_CONNECTOR_TUNNEL_DOWN
-
- AL_CIE_AGENT_DISCONNECT
- AL_CIE_DIRECTORY_DISCONNECT
- AL_MU_IP_POOL_CAPACITY
- AL_MU_IP_POOL_USAGE
- AL_RN_ECMP_BGP_DOWN
- AL_RN_ECMP_BGP_FLAP
- AL_RN_PRIMARY_WAN_BGP_DOWN
- AL_RN_PRIMARY_WAN_BGP_FLAP
- AL_RN_PRIMARY_WAN_TUNNEL_DOWN
- AL_RN_PRIMARY_WAN_TUNNEL_FLAP
- AL_RN_SECONDARY_WAN_BGP_DOWN
- AL_RN_SECONDARY_WAN_BGP_FLAP
- AL_RN_SECONDARY_WAN_TUNNEL_DOWN
- AL_RN_SECONDARY_WAN_TUNNEL_FLAP
- AL_RN_SITE_DOWN
- AL_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- AL_RN_SPN_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_PRIMARY_WAN_BGP_DOWN
- AL_SC_PRIMARY_WAN_BGP_FLAP
- AL_SC_PRIMARY_WAN_TUNNEL_DOWN
- AL_SC_PRIMARY_WAN_TUNNEL_FLAP
- AL_SC_SECONDARY_WAN_BGP_DOWN
- AL_SC_SECONDARY_WAN_BGP_FLAP
- AL_SC_SECONDARY_WAN_TUNNEL_DOWN
- AL_SC_SECONDARY_WAN_TUNNEL_FLAP
- AL_SC_SITE_DOWN
- AL_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_SITE_LONG_DURATION_EXCEEDED_CAPACITY
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- AL_ZTNA_CONNECTOR_CPU_HIGH
- AL_ZTNA_CONNECTOR_MEMORY_HIGH
- AL_ZTNA_CONNECTOR_TUNNEL_DOWN
- New Features in Incidents and Alerts
- Known Issues
Plan for IP Address Changes for Mobile Users, Remote Networks, and Service Connections
After you set up your Prisma Access deployment, it is
useful to know when IP addresses change so that you can pro-actively
plan your infrastructure and add required IP addresses to allow
lists accordingly. The IP address changes can be the result of changes
you made (for example, adding another mobile users location) or
changes that Prisma Access performs automatically (for example,
a large number of mobile users accesses a single Prisma Access gateway).
The following sections describe how IP addresses can change:
- IP Address Allocation For Mobile Users
- IP Address Changes For Remote Network Connections That Allocate Bandwidth by Location
- IPSec Termination Nodes and Service IP Addresses
- Mobile User, Remote Network, and Service Connection IP Allocation Changes After a Compute Location Change
- Loopback IP Address Allocation for Mobile Users
IP Address Allocation For Mobile Users
After you deploy Prisma Access for users for the first
time, Prisma Access adds two public and (if applicable)
egress IP addresses for each location you onboard. These
IP addresses are unique, not shared, and dedicated to your Prisma
Access deployment. If you have a multitenant setup, Prisma Access
adds dedicated IP addresses for each tenant.
Since the public IP address is the source IP address used by
Prisma Access for requests made to an internet-based source, you
need to know what the public IP address are and add them to an allow
list in your network to provide your users access to resources such
as SaaS applications or publicly-accessible partner applications.
Because Prisma Access adds more public IP addresses when you
add a gateway, and can add more public IP addresses after a scaling
event, you should add an IP Change Event
Notification URL, or use the API to retrieve mobile user
addresses, to be notified of IP address changes in your Prisma Access
infrastructure. You can then add any added or changed addresses
to an allow list.
Public IP Address Scaling Examples for Mobile Users
The following examples illustrate the mobile user public
IP address allocation process that Prisma Access uses during a scaling
event or when you add a new location.
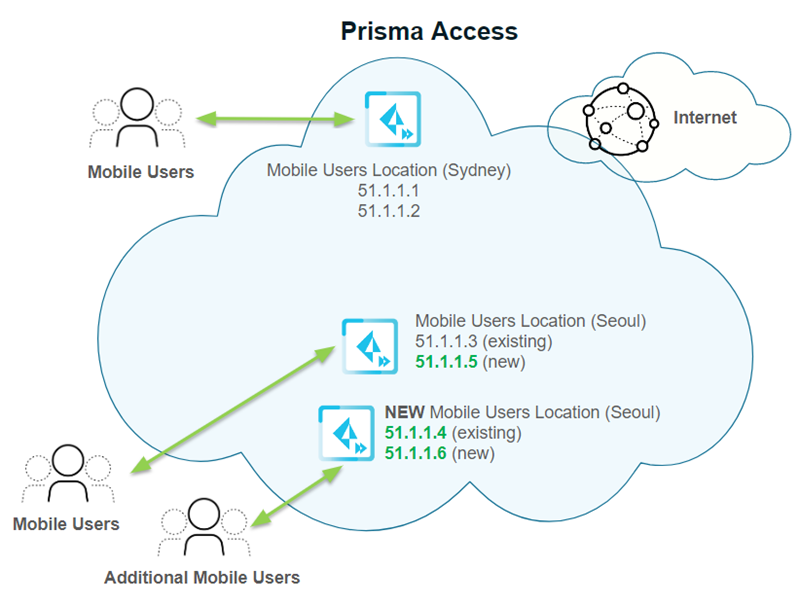
In the following example, you specified two locations in the
Asia Pacific region for a new mobile user deployment: Sydney and
Seoul. Each location is given two gateway IP addresses.

Then a large number of users log in to the Seoul location. To
accommodate these extra users, Prisma Access adds a second gateway
for the Seoul location, takes one of the gateway addresses from
the first Seoul gateway (51.1.1.4) and assigns it to the second
Seoul gateway. It then adds two additional IP addresses (51.1.1.5
and 51.1.1.6 in this example) and adds them to the two Seoul gateways.
Then you add another location, Tokyo, in the Asia Pacific region.
Prisma Access creates two new IP addresses for the new gateway (51.1.1.7
and 51.1.1.8).
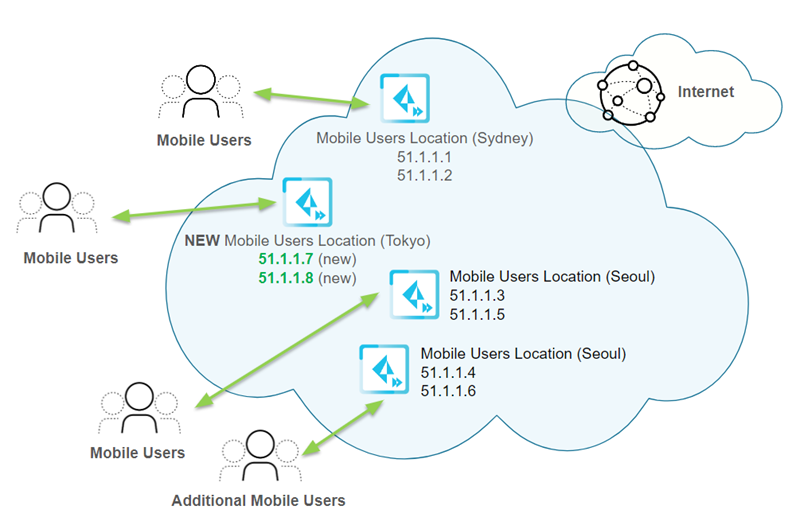
Each time you add a location or have a scaling event, you should retrieve the new egress
and gateway IP addresses that Prisma Access assigned and
add them to an allow list in your network. Prisma Access keeps two sets
of IP addresses at all times for all active gateways in each location.
IP Address Changes For Remote Network Connections That Allocate Bandwidth by Location
This section applies if you have a legacy Prisma Access
deployment that allocates bandwidth
by location. Any new deployments allocate bandwidth by compute
location; to learn about how Prisma Access allocates those IP addresses,
see
IPSec Termination Nodes and Service IP Addresses
.IP addresses for remote network connections are unique, not shared,
and dedicated to your Prisma Access deployment. These IP addresses
do not change after Prisma Access creates them as part of remote
network onboarding, and the IP addresses persist after an upgrade.
However, take care when increasing the bandwidth of an existing
connection, because the IP address of a remote network can change
if that increase causes the bandwidth in a location to exceed 500
Mbps.
In addition, egress IP addresses can change if Prisma Access
creates a new compute location and
you decide to use this new compute location with locations you have
already onboarded. See
Mobile User, Remote Network, and Service Connection IP Allocation Changes After a Compute Location Change
for details.These bandwidth guidelines apply only when you upgrade an existing
connection. A single remote network connection, even a 1000 Mbps
(Preview) connection, always receives a single Service
IP Address, regardless of its size.
The 1000 Mbps bandwidth option is in preview mode. The
throughput during preview is delivered on a best-effort basis and
the actual performance will vary depending upon the traffic mix.
The following example shows three remote network connections
in the same location, each with a bandwidth of 150 Mbps. Since the
total bandwidth is 500 Mbps, Prisma Access assigns a single IP address
for all connections in the location.

The following example shows the bandwidth of remote network connection
A being increased from 150 Mbps to 300 Mbps. Since the total bandwidth
of all connections is now more than 500 Mbps, Prisma Access assigns
a new service IP address for the connection with the additional
bandwidth. The other service IP addresses remain unchanged.

Conversely, given four remote networks with a bandwidth of 100
Mbps, if you increase the bandwidth of one of the remote networks
to 100 Mbps, the Service IP address of that remote network does
not change because the total bandwidth is now 500 Mbps.
If you reduce the bandwidth of a remote network connection,
the Service IP address does not change.
To find the service IP addresses in Panorama, select PanoramaCloud ServicesStatusNetwork Details tab and
click the Remote Networks radio button to
display the Service IP Address for the remote
networks, or use the API script.
IPSec Termination Nodes and Service IP Addresses
All new deployments starting with Prisma Access 1.8
allocate remote network bandwidth by compute location instead
of by Prisma Access location. You can also upgrade your current
deployment to allocate bandwidth by compute location.
When you onboard a remote network,
you associate it with an IPSec Termination Node, and each
IPSec termination node has a Service IP Address associated
with it. You use the Service IP Address as
the peer IP address when you set up the IPSec tunnel for the remote network
connection. Each termination node can provide you up to 500 Mbps
of bandwidth. Associating more than 500 Mbps of bandwidth to a compute
location provides you with more than one Service IP Address.

When you onboard a remote network in an Ireland compute location,
you are given a choice of two IPSec termination nodes, because the
total bandwidth is more than 500 Mbps.

Each IPSec termination node has its own Service IP address, as
can be seen in PanoramaCloud
ServicesStatusNetwork
DetailsRemote Networks.

Mobile User, Remote Network, and Service Connection IP Allocation Changes After a Compute Location Change
To optimize performance and improve latency, Prisma
Access can introduce new compute locations for
existing remote network locations as part of a plugin upgrade. When
you upgrade the plugin, you can choose to take advantage of the
new compute location. If you change the compute region, Prisma Access
changes the gateway and portal IP addresses (for mobile users) and
Service IP addresses (for remote networks) for the location or locations
to which the new compute location is associated. If you use allow
lists in your network to provide users access to internet resources
such as SaaS applications or publicly accessible partner applications,
you need to add these new IP addresses to your allow lists.
To upgrade to a new compute location after it becomes available,
complete the following task.
Since you need to allow time to delete and add the existing location
and change your allow lists (for mobile users) or peer IPSec tunnel
IP address (for remote network deployments), Palo Alto Networks
recommends that you schedule a compute location change during a
maintenance window or during off-peak hours.
To reduce down time for mobile user deployments,
you can use the API to pre-allocate the
new mobile user gateway and portal IP addresses before you perform
these steps.
- Add bandwidth for the new remote network compute locations.
- (Remote Network deployments that allocate remote network bandwidth by compute locations only) Select PanoramaCloud ServicesConfigurationRemote Networks.
- Click the gear icon in the Bandwidth Allocation area and add Bandwidth Allocation (Mbps) for the new compute location.
- Wait for the bandwidth to be reflected in the Allocated Total field at the top of the page; then, click OK.
- Delete the Service Connection, Remote Network connection, or Mobile User location associated with the new compute location.
- Commit and push your changes.
- Re-add the locations you just deleted.
- Commit and push your changes.
- (Mobile User deployments only) Retrieve the new gateway and portal IP addresses using the API script and add them to your allow lists.
- (Remote Network and Service Connection deployments only) Change your CPE to point to the new IP addresses for the IPSec tunnel for the remote network connection or service connection.For remote network connections, select PanoramaCloud ServicesStatusNetwork DetailsRemote Networks, make a note of the Service IP Address, and configure the new Service IP Address as the peer address for the remote network IPSec tunnel on your CPE.For service connections, select PanoramaCloud ServicesStatusNetwork DetailsService Connection, make a note of the Service IP Address, and configure the new Service IP Address as the peer address for the service connection IPSec tunnel on your CPE.
- Select PanoramaCloud ServicesStatusNetwork DetailsRemote Networks, make a note of the Service IP Address, and configure the new Service IP Address as the peer address for the remote network IPSec tunnel on your CPE.When you delete and re-add a remote network connection, the IP address of the IPSec tunnel on the Prisma Access side changes.
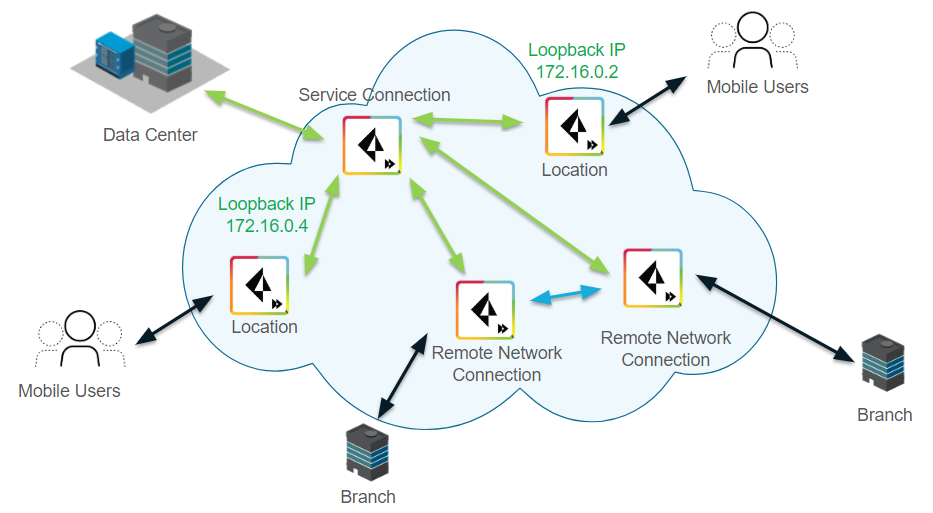
Loopback IP Address Allocation for Mobile Users
Loopback IP addresses can change for mobile users
during an infrastructure or dataplane upgrade.
Loopback IP addresses do not change for service connections
or remote network connections during an infrastructure or dataplane
upgrade; only mobile user loopback IP addresses can change.
Prisma Access allocates the loopback IP addresses from the infrastructure
subnet that you specify when you enable the Prisma
Access infrastructure. You can add the entire infrastructure
subnet to an allow list and avoid planning for mobile user loopback
IP changes during an infrastructure or dataplane upgrade. To find
the infrastructure subnet, select PanoramaCloud ServicesStatusNetwork DetailsService Infrastructure and
view the Infrastructure Subnet.
Retrieve these addresses using the Retrieve Public, Loopback, and Egress IP Addresses used to retrieve
public IP and loopback IP addresses.
The following example shows a Prisma Access deployment that has
an infrastructure subnet of 172.16.0.0/16. Prisma Access has assigned
loopback IP addresses 172.16.0.1 and 172.16.0.3 for mobile users
from the infrastructure subnet.

After in infrastructure or dataplane upgrade (for example, to
prepare for a new release of the Cloud Services plugin), Prisma
Access assigns two different IP addresses for mobile users from
the infrastructure subnet (172.16.0.1 is changed to 172.16.0.2 and
172.16.0.3 is changed to 172.16.0.4).