Manage Upgrade Options for the GlobalProtect App
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
5.2 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
-
- Allocate Licenses for Prisma Access (Managed by Strata Cloud Manager)
- Plan Service Connections for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Add Additional Locations for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Enable Available Add-ons for Prisma Access (Managed by Strata Cloud Manager)
- Search for Subscription Details
- Share a License for Prisma Access (Managed by Strata Cloud Manager) and Add-ons
- Increase Subscription Allocation Quantity
-
- Activate a License for Prisma Access (Managed by Strata Cloud Manager) and Prisma SD-WAN Bundle
- Activate and Edit a License for SASE 5G Through Common Services
-
- Prisma Access Onboarding Workflow
-
2.2 Preferred
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
- Prisma Access China
-
- Prisma Access
- Prisma Access Infrastructure Management
- Releases and Upgrades
- Manage Upgrade Options for the GlobalProtect App
- Notifications and Alerts for Panorama, Cloud Services Plugin, and PAN-OS Dataplane Versions
- Retrieve the IP Addresses for Prisma Access
- Plan for IP Address Changes for Mobile Users, Remote Networks, and Service Connections
- Service IP and Egress IP Address Allocation for Remote Networks
- How to Calculate Remote Network Bandwidth
- Prisma Access APIs
- Use Logging, Routing, and EDL Information to Troubleshoot Your Deployment
-
- Set Up Prisma Access
- Plan the Service Infrastructure and Service Connections
- Configure the Service Infrastructure
- Create a Service Connection to Allow Access to Your Corporate Resources
- Create a Service Connection to Enable Access between Mobile Users and Remote Networks
- Deployment Progress and Status
- How BGP Advertises Mobile User IP Address Pools for Service Connections and Remote Network Connections
- Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
- Routing Preferences for Service Connection Traffic
- Create a High-Bandwidth Network Using Multiple Service Connections
- List of Prisma Access Locations
-
- Plan To Deploy Prisma Access for Mobile Users
- Secure Mobile Users With GlobalProtect
- Secure Mobile Users with an Explicit Proxy
- Zone Mapping
- Specify IP Address Pools for Mobile Users
- How the GlobalProtect App Selects a Prisma Access Location for Mobile Users
- View Logged In User Information and Log Out Current Users
-
- Use Explicit Proxy to Secure Public Apps and GlobalProtect or a Third-Party VPN to Secure Private Apps
- Prisma Access with On-Premises Gateways
-
- Set Equal Gateway Priorities for On-Premises and Prisma Access Gateways
- Set a Higher Gateway Priority for an On-Premises Gateway
- Set Higher Priorities for Multiple On-Premises Gateways
- Configure Priorities for Prisma Access and On-Premises Gateways
- Allow Mobile Users to Manually Select Specific Prisma Access Gateways
- DNS Resolution for Mobile Users—GlobalProtect and Remote Network Deployments
- IPv6 Support for Private App Access
- Sinkhole IPv6 Traffic In Mobile Users—GlobalProtect Deployments
- Identification and Quarantine of Compromised Devices With Prisma Access
- Support for Gzip Encoding in Clientless VPN
- Report Website Access Issues
-
- Plan to Deploy Remote Networks
- Onboard and Configure Remote Networks
-
- Remote Network Locations with Overlapping Subnets
- Remote Network Locations with WAN Link
- Use Predefined IPSec Templates to Onboard Service and Remote Network Connections
- Onboard Remote Networks with Configuration Import
- Configure Quality of Service in Prisma Access
- Create a High-Bandwidth Network for a Remote Site
- Provide Secure Inbound Access to Remote Network Locations
-
- Multitenancy Overview
- Multitenancy Configuration Overview
- Enable Multitenancy and Migrate the First Tenant
- Add Tenants to Prisma Access
- Delete a Tenant
- Create a Tenant-Level Administrative User
- Control Role-Based Access for Tenant-Level Administrative Users
- Sort Logs by Device Group ID for External Logging
- Visibility and Monitoring Features in the Prisma Access App
-
- Integrate Prisma Access With Other Palo Alto Networks Apps
- Integrate Third-Party Enterprise Browser with Explicit Proxy
- Integrate Third-Party NDRs with Prisma Access
- Juniper Mist Integration for SASE Health
-
-
- Connect your Mobile Users in Mainland China to Prisma Access Overview
- Configure Prisma Access for Mobile Users in China
- Configure Real-Name Registration and Create the VPCs in Alibaba Cloud
- Attach the CEN and Specify the Bandwidth
- Create Linux Instances in the Alibaba Cloud VPCs
- Configure the Router Instances
- Onboard the GlobalProtect Gateway and Configure the Prisma Access Portal
-
-
-
- INC_CIE_AGENT_DISCONNECT
- INC_CIE_DIRECTORY_DISCONNECT
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_GW_USER_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_GLOBALPROTECT_PORTAL_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_MU_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_MU_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_MU_DNS_SERVER_UNREACHABLE_ PER_PA_LOCATION
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_ALL_PA_LOCATIONS
- INC_PORTAL_CLIENTLESS_VPN_AUTH_ TIMEOUT_FAILURES_COUNT_EXCEEDED_ ABOVE_BASELINE_PER_PA_LOCATION
- INC_RN_AUTH_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_AUTH_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_DNS_SERVER_UNREACHABLE_ALL_ PA_LOCATIONS
- INC_RN_DNS_SERVER_UNREACHABLE_PER_ PA_LOCATION
- INC_RN_ECMP_TUNNEL_RTT_EXCEEDED_ BASELINE
- INC_RN_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SECONDARY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_RN_SITE_CAPACITY_PREDICTION
- INC_SC_PRIMARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SECONDARY_WAN_TUNNEL_RTT_ EXCEEDED_BASELINE
- INC_SC_SITE_CAPACITY_PREDICTION
-
- INC_CERTIFICATE_EXPIRY
- INC_GP_CLIENT_VERSION_UNSUPPORTED
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_CAPACITY
- INC_MU_IP_POOL_BLOCK_UTILIZATION_ EXCEEDED_THRESHOLD
- INC_PA_INFRA_DEGRADATION
- INC_PA_SERVICE_DEGRADATION_PA_LOCATION
- INC_PA_SERVICE_DEGRADATION_RN_ SITE_CONNECTIVITY
- INC_PA_SERVICE_DEGRADATION_SC_ CONNECTIVITY
- INC_RN_ECMP_BGP_DOWN
- INC_RN_ECMP_BGP_FLAP
- INC_RN_ECMP_PROXY_TUNNEL_DOWN
- INC_RN_ECMP_PROXY_TUNNEL_FLAP
- INC_RN_ECMP_TUNNEL_DOWN
- INC_RN_ECMP_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_BGP_FLAP
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_PRIMARY_WAN_TUNNEL_DOWN
- INC_RN_PRIMARY_WAN_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_BGP_DOWN
- INC_RN_SECONDARY_WAN_BGP_FLAP
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_RN_SECONDARY_WAN_TUNNEL_DOWN
- INC_RN_SECONDARY_WAN_TUNNEL_FLAP
- INC_RN_SITE_DOWN
- INC_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_RN_SPN_LONG_DURATION_CAPACITY_EXCEEDED _THRESHOLD
- INC_RN_SPN_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_SC_PRIMARY_WAN_BGP_DOWN
- INC_SC_PRIMARY_WAN_BGP_FLAP
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_PRIMARY_WAN_TUNNEL_DOWN
- INC_SC_PRIMARY_WAN_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_BGP_DOWN
- INC_SC_SECONDARY_WAN_BGP_FLAP
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_PROXY_TUNNEL_FLAP
- INC_SC_SECONDARY_WAN_TUNNEL_DOWN
- INC_SC_SECONDARY_WAN_TUNNEL_FLAP
- INC_SC_SITE_DOWN
- INC_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- INC_SC_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN
- INC_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- INC_ZTNA_CONNECTOR_CPU_HIGH
- INC_ZTNA_CONNECTOR_MEMORY_HIGH
- INC_ZTNA_CONNECTOR_TUNNEL_DOWN
-
- AL_CIE_AGENT_DISCONNECT
- AL_CIE_DIRECTORY_DISCONNECT
- AL_MU_IP_POOL_CAPACITY
- AL_MU_IP_POOL_USAGE
- AL_RN_ECMP_BGP_DOWN
- AL_RN_ECMP_BGP_FLAP
- AL_RN_PRIMARY_WAN_BGP_DOWN
- AL_RN_PRIMARY_WAN_BGP_FLAP
- AL_RN_PRIMARY_WAN_TUNNEL_DOWN
- AL_RN_PRIMARY_WAN_TUNNEL_FLAP
- AL_RN_SECONDARY_WAN_BGP_DOWN
- AL_RN_SECONDARY_WAN_BGP_FLAP
- AL_RN_SECONDARY_WAN_TUNNEL_DOWN
- AL_RN_SECONDARY_WAN_TUNNEL_FLAP
- AL_RN_SITE_DOWN
- AL_RN_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_RN_SITE_LONG_DURATION_EXCEEDED_ CAPACITY
- AL_RN_SPN_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_PRIMARY_WAN_BGP_DOWN
- AL_SC_PRIMARY_WAN_BGP_FLAP
- AL_SC_PRIMARY_WAN_TUNNEL_DOWN
- AL_SC_PRIMARY_WAN_TUNNEL_FLAP
- AL_SC_SECONDARY_WAN_BGP_DOWN
- AL_SC_SECONDARY_WAN_BGP_FLAP
- AL_SC_SECONDARY_WAN_TUNNEL_DOWN
- AL_SC_SECONDARY_WAN_TUNNEL_FLAP
- AL_SC_SITE_DOWN
- AL_SC_SITE_LONG_DURATION_CAPACITY_ EXCEEDED_THRESHOLD
- AL_SC_SITE_LONG_DURATION_EXCEEDED_CAPACITY
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN
- AL_ZTNA_CONNECTOR_APP_STATUS_DOWN_PARTIAL
- AL_ZTNA_CONNECTOR_CPU_HIGH
- AL_ZTNA_CONNECTOR_MEMORY_HIGH
- AL_ZTNA_CONNECTOR_TUNNEL_DOWN
- New Features in Incidents and Alerts
- Known Issues
Manage Upgrade Options for the GlobalProtect App
Control how Prisma Access manages the GlobalProtect app.
Control the active app versions on the Prisma Access portal. Manage
the active GlobalProtect version.
Prisma Access hosts the GlobalProtect app
version that macOS and Windows users in your organization can download
from the Prisma Access portal. Prisma Access offers several versions
of the GlobalProtect app, and you can choose to make one of those
versions the active version. You can also manage mobile users' access
to the GlobalProtect app, or perform staged upgrades.
- Select the Active GlobalProtect App Version
- Manage Users’ Access to GlobalProtect App Updates
- Perform Staged Updates of the GlobalProtect App
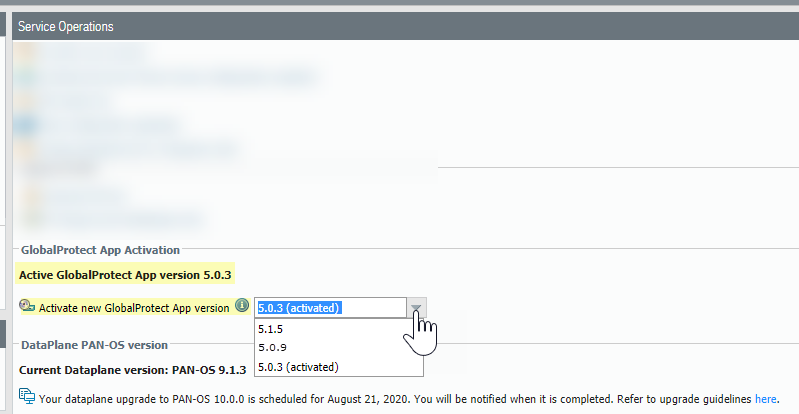
Select the Active GlobalProtect App Version
Prisma Access manages the GlobalProtect app
version for Windows and macOS users in your organization. While
Prisma Access hosts several GlobalProtect app versions, only one
of the hosted versions is active. When mobile users log in to the
Prisma Access portal, the active version is the one they download and
use on their Windows and macOS devices.
The System Status
page also provides you information about your current Panorama version,
Cloud Services plugin version, and dataplane version. You can receive
notifications and alerts on this page when plugin or Panorama versions become
end of support (EoS) for use with Prisma Access. See Notifications and Alerts for Panorama, Cloud Services Plugin, and PAN-OS Dataplane Versions for details.
If
your currently-active version is end-of-life, Prisma Access notifies
you and requests that you activate a supported version.
You
can select different GlobalProtect versions in a multitenant deployment.
The GlobalProtect app version settings you apply are per tenant
and not global; you control the app version on a per-tenant basis.
You
can replace the current active version with another hosted version
from the Service Setup page by completing the following steps.
- Select PanoramaCloud ServicesConfigurationService Setup.
- Select Activate new GlobalProtect App version and compare it to the active GlobalProtect version.
 If your current GlobalProtect version is end-of-life (EoL), a message displays in this area on the Service Setup page; if you receive this message, upgrade your GlobalProtect app version by continuing to the next step.
If your current GlobalProtect version is end-of-life (EoL), a message displays in this area on the Service Setup page; if you receive this message, upgrade your GlobalProtect app version by continuing to the next step.
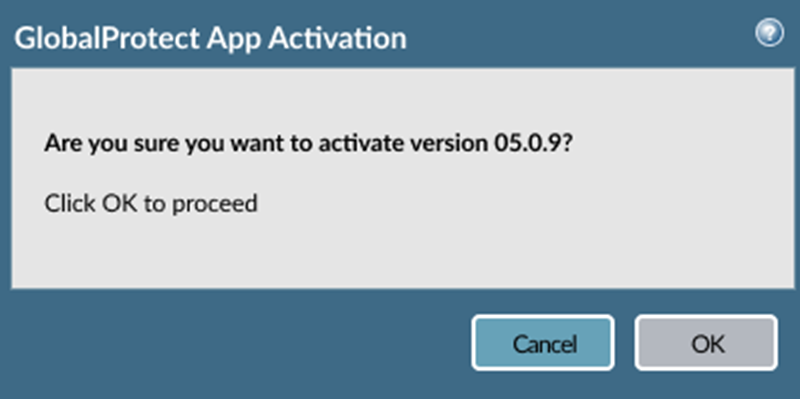
- Select the version to which you want to upgrade.A window displays to verify your choice.
 After the app has been activated, you receive a success message.
After the app has been activated, you receive a success message.
- View the System Status page to verify that the GlobalProtect app version you selected as active is the Active GlobalProtect App version.
Manage Users’ Access to GlobalProtect App Updates
To manage mobile users' access to the active
GlobalProtect app version that is hosted by Prisma Access, complete
the following steps.
- In Panorama, select NetworkGlobalProtectPortals.
- Select the Mobile_User_Template from the Template drop-down.
- Select GlobalProtect_Portal to edit the Prisma Access portal configuration.
- Select the Agent tab and select the app configuration.
- Select the App tab.
- In the App Configurations area, select a choice in Allow User to Upgrade GlobalProtect App to specify whether mobile users can upgrade their GlobalProtect app version to the active version that is hosted on Prisma Access and, if they can, whether they can choose when to upgrade:
- Allow with Prompt (default)—Prompt users when a new version is activated and allow users to upgrade their software when it is convenient.
- Disallow—Prevent users from upgrading the app software.
- Allow Manually—Allow users to manually check for and initiate upgrades by selecting Check Version in the GlobalProtect app.
- Allow Transparently—Automatically upgrade the app software whenever a new version becomes available on the portal.
- Internal—Automatically upgrade the app software whenever a new version becomes available on the portal, but wait until the endpoint is connected internally to the corporate network. This prevents delays caused by upgrades over low-bandwidth connections.
Perform Staged Updates of the GlobalProtect App
If you manage a large organization, you might
want to update mobile users to the latest version of the GlobalProtect
app in stages. For example, you could assign a smaller group to
update their GlobalProtect app before rolling out the update to
everybody in your organization. To do so, complete the following
task.
- If you have not yet created it, create a user group for the first group of users to which you want to roll out the GlobalProtect app update.You can use User-ID to map users to groups, or select DeviceLocal User DatabaseUser Groups to manually create a group.
- Create a new GlobalProtect agent configuration to use for the first group of users.
- In Panorama, select NetworkGlobalProtectPortals.
- Select the Mobile_User_Template from the Template drop-down.
- Select GlobalProtect_Portal to edit the Prisma Access portal configuration.
- Select the Agent tab.
- Select the DEFAULT configuration and Clone it.You can also Add a new configuration; but cloning the existing configuration copies over required information for the new configuration.
- Specify a Name for the configuration.

- Select the Config Selection Criteria tab.
- In the User/User Group area, select the user you created in Step1.

- Select the App tab.
- Change Allow User to Upgrade GlobalProtect App to either Allow with Prompt or Allow Transparently.Allow with Prompt prompts users when a new version is activated and allows them to upgrade their software when it is convenient; Allow Transparently automatically upgrades the app software whenever a new version becomes available on the portal.

- Click OK to save your changes.
- Select Move Up to move your configuration above the default configuration.When an app connects, the portal compares the source information in the packet against the agent configurations you have defined. As with security rule evaluation, the portal looks for a match starting from the top of the list. When it finds a match, it delivers the corresponding configuration to the app.

- Repeat these steps for the DEFAULT configuration, but change Allow User to Upgrade GlobalProtect App to Disallow to prevent users from updating to the latest GlobalProtect app software.
- When you want to let the rest of the users update their apps, change Allow User to Upgrade GlobalProtect App in the DEFAULT configuration to a selection that allows it (either Allow with Prompt or Allow Transparently).