SaaS Security
Cortex XSOAR for Data Security
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Cortex XSOAR for Data Security
Learn about how Data Security integrates with Cortex
XSOAR.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Data Security is now available on the Cortex
XSOAR Marketplace. With this SaaS Security integration, Cortex XSOAR collects incidents
from Data Security for improved security orchestration and incident
management and remediation of risks posed by data exfiltration on
your organization’s Sanctioned SaaS applications.
In addition to the incident management and incident lifecycle capabilities
that XSOAR offers, with the SaaS Security playbooks, you can take
actions on incidents just as you do now on SaaS Security web interface,
including:
- Close incidents on Cortex XSOAR using the same Closed states to which you’re accustomed.
- Remove public sharing (public links) on assets.
- Quarantine assets.
- Restore quarantined assets.
- Send email notifications to SaaS Security administrators to request remediation of incidents.
- Notify asset owners and provide remediation options to SaaS Security administrators to resolve incidents.
Get Started
Here’s how to get up and running with Data Security on Cortex XSOAR:
- Install SaaS Security Content Pack and sample playbooks.
- Review the SaaS Security description Details on XSOAR Marketplace for the SaaS Security Content Pack and the documentation in Content > Playbooks to understand the benefits of this integration and what the SaaS Security Content Pack includes.Content Pack update notifications display automatically in Cortex XSOAR. Periodically check for these notifications and update the Content Pack to receive enhancements and fixes.Log in to the Cortex XSOAR Marketplace, then install the SaaS Security Content Pack and sample SaaS Security playbooks.Customize the sample SaaS Security playbooks:
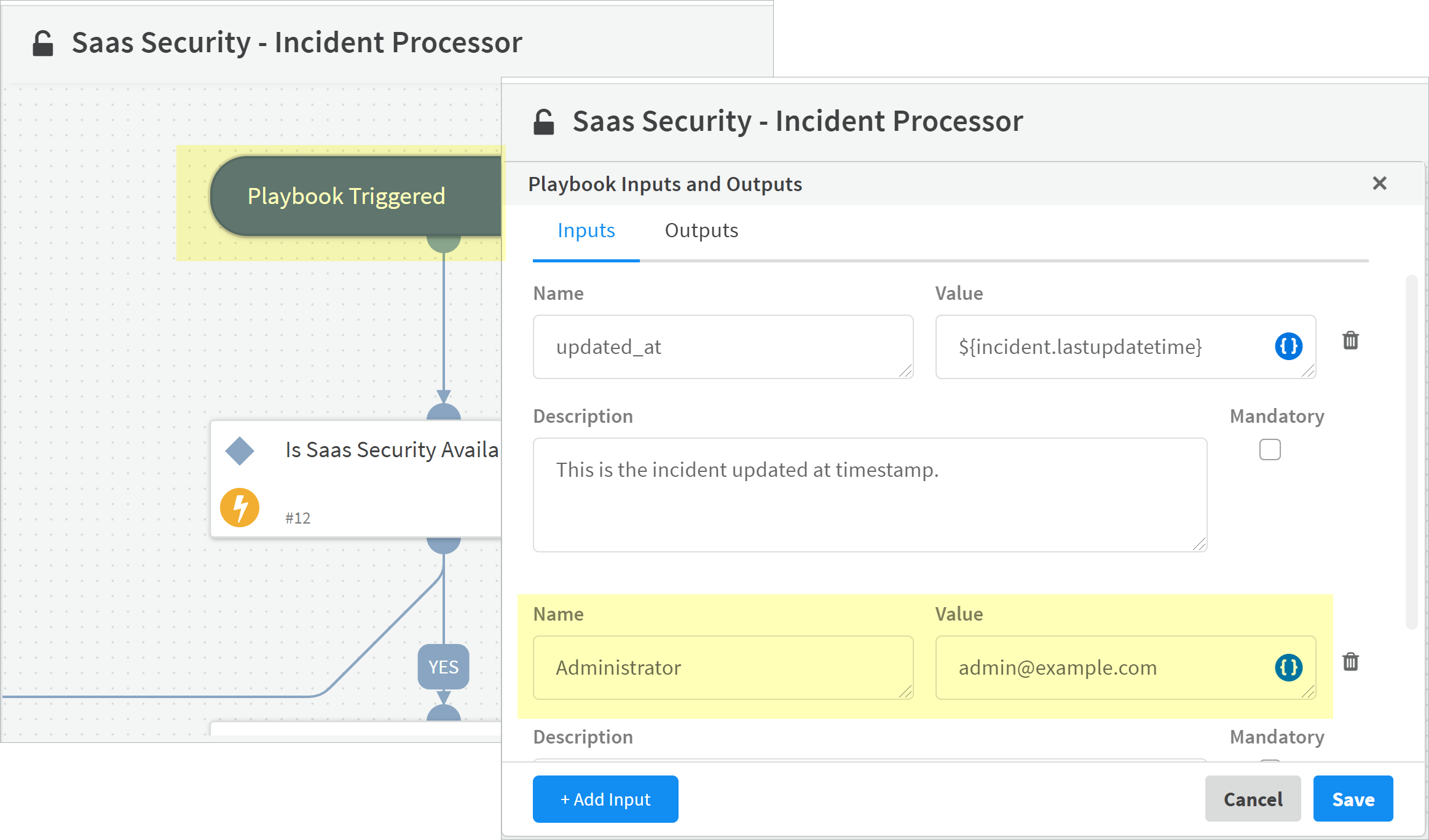
- Select Playbooks.For each sample playbook, click on the Playbook Setting gear icon to display instructions on how to modify the playbook settings.(Recommended) Select SaaS Security - Take Action on the IncidentEditRemove Public Sharing and specify if you want to enable SaaS Security Remove Inherited Sharing.(Recommended) Select SaaS Security - Incident ProcessorPlaybook TriggeredPlaybook Inputs and Outputs and specify an administrator account.If an incident is Unassigned on Data Security, XSOAR sends action requests to this backup administrator email address. Otherwise, XSOAR sends action requests to the Assigned administrator. If you do not specify this backup administrator, any action requests for Unassigned incidents fail with the following indicators:
- Workflow fails on Incident Detail.
- Work plan displays red instead of orange.
![]() Configure SaaS Security on Cortex XSOAR:
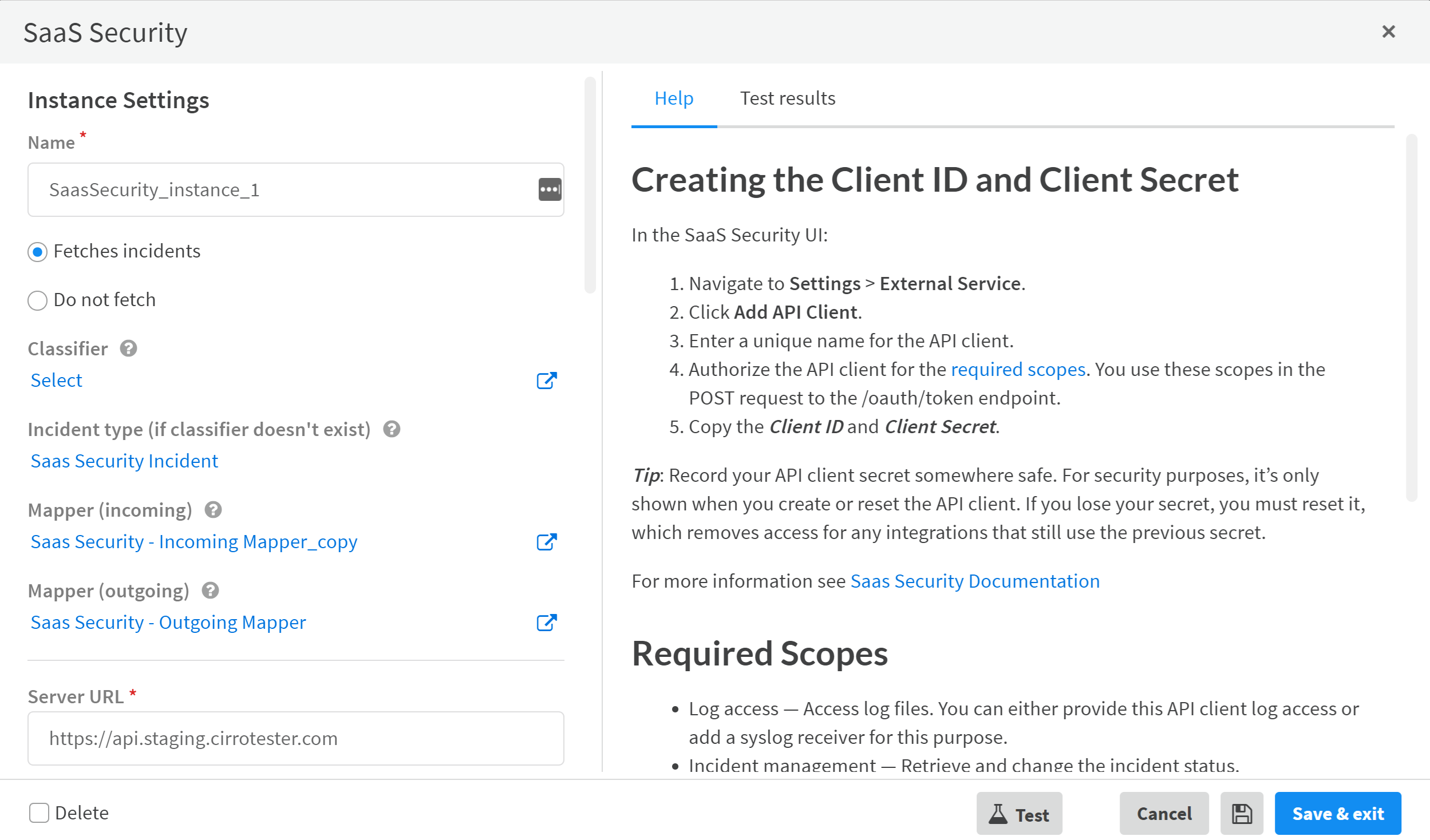
Configure SaaS Security on Cortex XSOAR:- Select SettingsIntegrationsServers & Services, then click the Instance Settings gear icon for the SaaS Security Content Pack.Observe the Instance Settings that you need to configure.SaaS SecurityInstance SettingsHelp provides instructions on how to create the Client ID and Client Secret with more detailed instructions in the SaaS Security Administrator’s Guide.Data Security supports one syslog receiver or one API client app with access to log data. Delete the existing configuration before you add a new one. If you want to use both Splunk and Cortex XSOAR, directly connect Splunk to Cortex XSOAR using the Splunk integration, and create a Client ID and Client Secret for Cortex XSOAR to directly connect to Data Security.When you enable SaaS Security Incident Mirroring, turn on Incoming and Outgoing and enable Close Mirrored XSOAR Incident.
![]() Wait while XSOAR populates with SaaS Security incidents.Completion time depends on the amount of incident data XSOAR needs to load. Also, the value you specified for the Fetch Interval setting determines how frequently XSOAR loads new data.Investigate SaaS Security incidents on XSOAR:
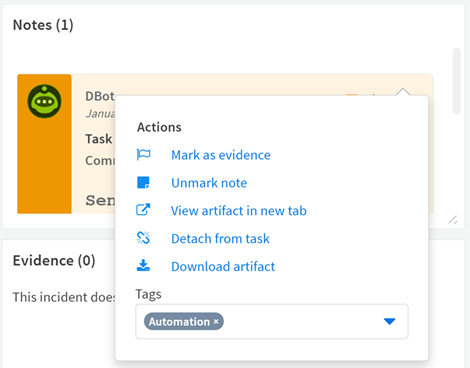
Wait while XSOAR populates with SaaS Security incidents.Completion time depends on the amount of incident data XSOAR needs to load. Also, the value you specified for the Fetch Interval setting determines how frequently XSOAR loads new data.Investigate SaaS Security incidents on XSOAR:- Select Dashboards & ReportsIncidents and browse the metrics for newly discovered SaaS Security Incidents.Select IncidentsTable ViewIncidents, then click the ID to investigate the asset that triggered the incident.For a description of each column in the table, go to the Content Pack documentation and click ContentIncident FieldsFrom Summary View, select Notes, then Download or View the asset for inspection.
![]() Manage and remediate SaaS Security Incidents on XSOAR:Before you assess, manage, or remediate incidents, learn about Incident Management on XSOAR. However, chances are you’re already using XSOAR to manage incidents for other applications and are familiar with XSOAR capabilities. In that case, consider the following management and remediation capabilities that are unique to SaaS Security on XSOAR.
Manage and remediate SaaS Security Incidents on XSOAR:Before you assess, manage, or remediate incidents, learn about Incident Management on XSOAR. However, chances are you’re already using XSOAR to manage incidents for other applications and are familiar with XSOAR capabilities. In that case, consider the following management and remediation capabilities that are unique to SaaS Security on XSOAR.- From Summary View, select Work Plan, then click Send Ask Question Email and Complete task, Assign owner, or Set due date to request that an administrator remediate an incident or Close incidents that are not threats using the supported method.
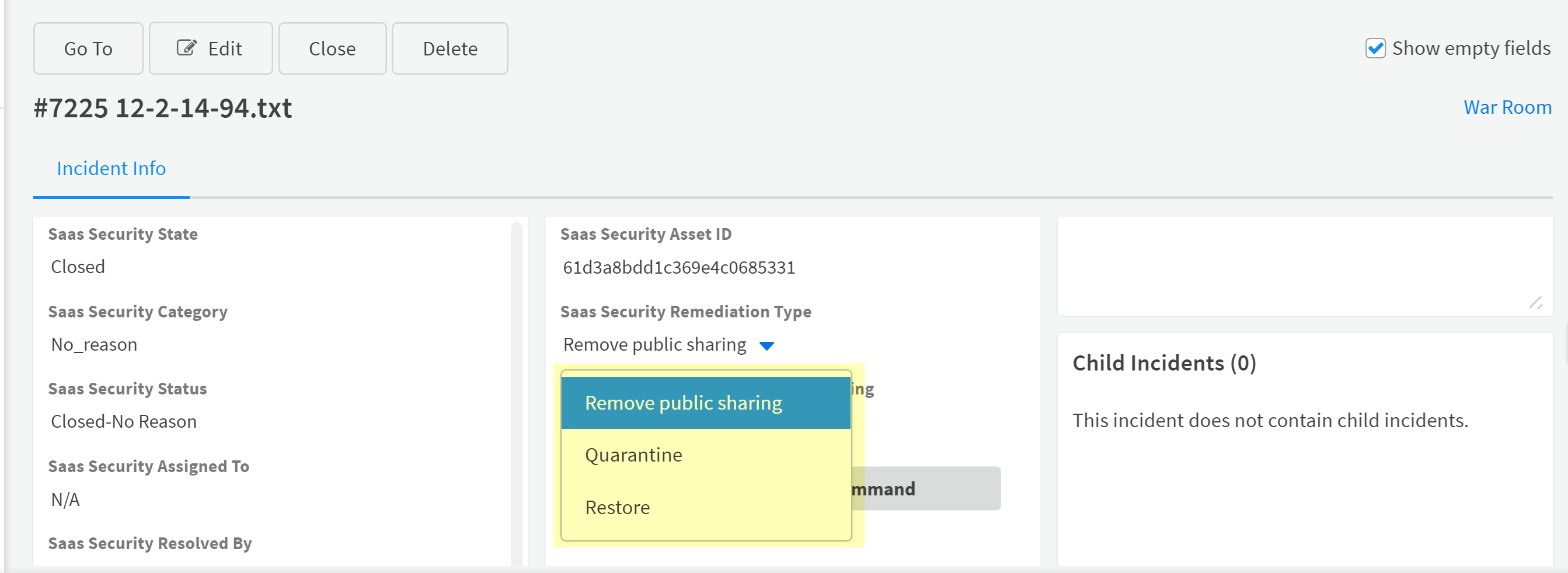
![]() SaaS Security playbooks support the same Closed states that are available directly on Data Security.From Summary View, select Remediation Action, then remediate the incidents by using the supported Run Commands or by clicking on the SaaS Security Remediation Type actions.The remediation actions listed behave just as you’d expect if you performed the action directly on SaaS Security. If the action doesn’t display, it is not supported for the SaaS application on which the asset resides.
SaaS Security playbooks support the same Closed states that are available directly on Data Security.From Summary View, select Remediation Action, then remediate the incidents by using the supported Run Commands or by clicking on the SaaS Security Remediation Type actions.The remediation actions listed behave just as you’d expect if you performed the action directly on SaaS Security. If the action doesn’t display, it is not supported for the SaaS application on which the asset resides.![]()
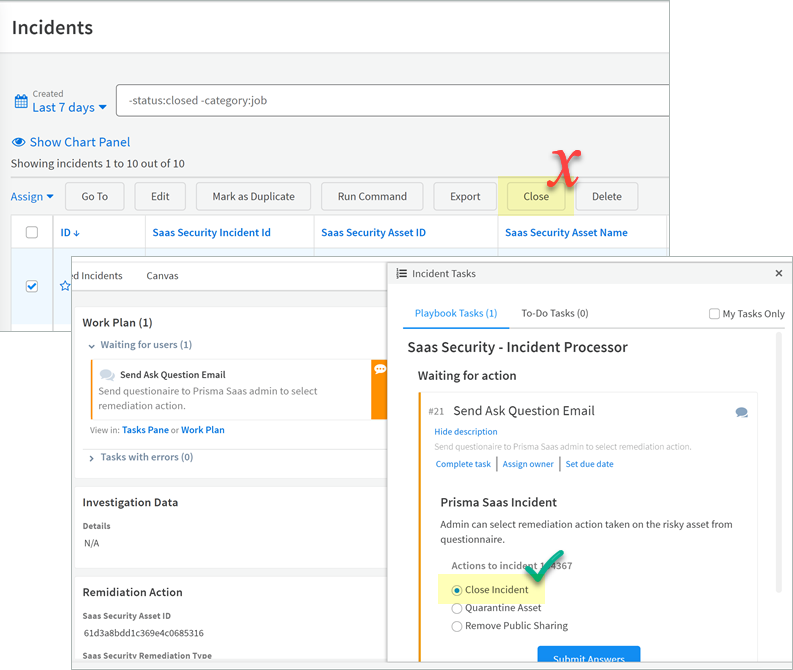
Close Incidents on XSOAR
When you Close an incident, you must do so from the Summary View, not Table View. An incident has both a unique ID on XSOAR and a unique SaaS Security Asset ID on XSOAR. Table View controls the closing of the XSOAR incident only and Summary View closes both the SaaS Security incident (SaaS Security State) and the XSOAR incident (State), if you have the recommended Close Mirrored XSOAR incident setting selected.![]()