Prisma Access
Juniper Mist Integration for SASE Health
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Juniper Mist Integration for SASE Health
Learn how to integrate Juniper Mist with Prisma Access to view and manage third-party
network devices and alerts directly from Strata Cloud Manager user interface.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The Juniper Mist integration with Prisma
Access allows you to view and manage third-party network devices and
alerts directly from the Strata Cloud Manager (SCM) user
interface. This integration provides you with a single pane of glass to efficiently
diagnose and resolve branch site issues. By extending LAN health and performance
visibility to the Strata Cloud Manager dashboard, this integration delivers
critical insights into access points, switches, and WAN edge devices within branch
locations, sourced from Juniper Mist. With comprehensive, end-to-end visibility
across LAN infrastructure, Prisma Access, network services, and applications,
administrators can quickly identify and address performance-impacting issues,
ensuring optimal network reliability and efficiency.
SASE Health provides a detailed view of Juniper Mist device inventory,
including switches, access points, and WAN edges. It displays the high availability
status of Juniper Mist infrastructure while highlighting the number of impacted
users and the root causes of service degradation. Additionally, it provides
real-time alerts, categorizing incidents for better visibility to aid in
troubleshooting.
Key components of this integration include:
- Enhanced site experience visualization now includes Juniper Mist service delivery segments, such as access points, switches, and WAN edge devices.
- Display of Juniper Mist device inventory and status.
- Integration of Juniper Mist alerts into the SASE Health incident view.
- Cross-launch capability to Juniper Mist user interface for detailed incident information.
To enable end-to-end visibility for this integration, orchestration must be completed
beforehand. This includes configuring tunnel setup in the Juniper Mist portal and
establishing tunnels from WAN Edge devices at the branch site to the Prisma Access
remote network. Once this setup is complete, visibility can be configured on the
Third-Party Integration page.
This integration is available only for users with a Prisma
Access Remote Network license, AI ADEM, and a
Juniper Mist license (for AP, switch, and WAN edge).
Without AI ADEM, Strata Cloud Manager (SCM) will not provide visibility for this
integration.
Before integrating Juniper Mist with Prisma
Access, you must first configure API Access in the Juniper Mist
portal.
- Configure Juniper Mist API Access.
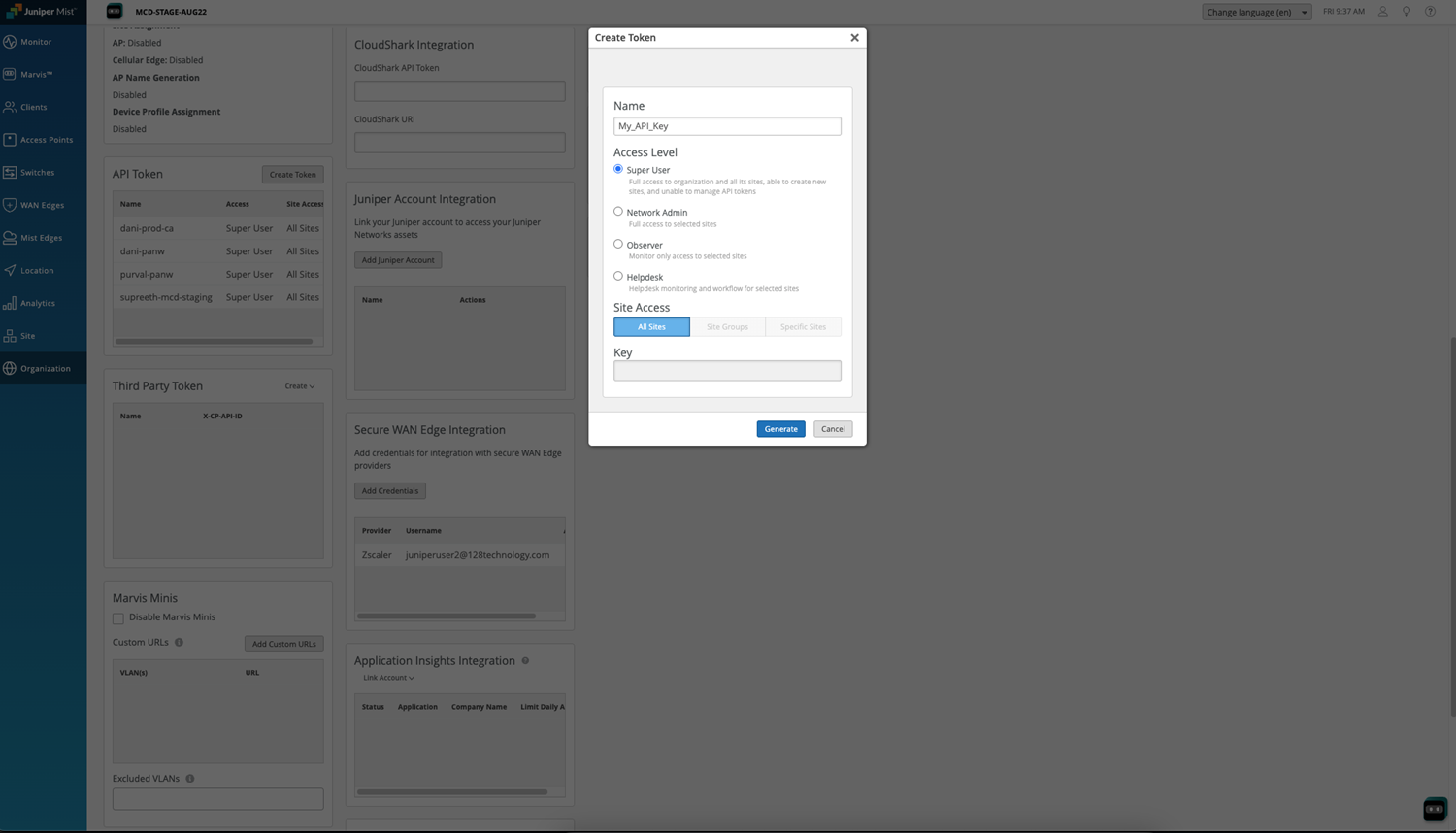
- Navigate to Organization SettingsAPI Access in the Juniper Mist portal.Generate an API token for authentication between Juniper Mist and Prisma Access.Ensure the API token has read access to necessary resources (APs, Switches, WAN Edge), and Alerts/Incidents.
![]() Copy and securely save this API token, as it will be required later in the Juniper Mist integration process. It will not be visible again after you leave this page.Configuring visibility on Strata Cloud Manager with Juniper Mist Integration in Prisma Access.
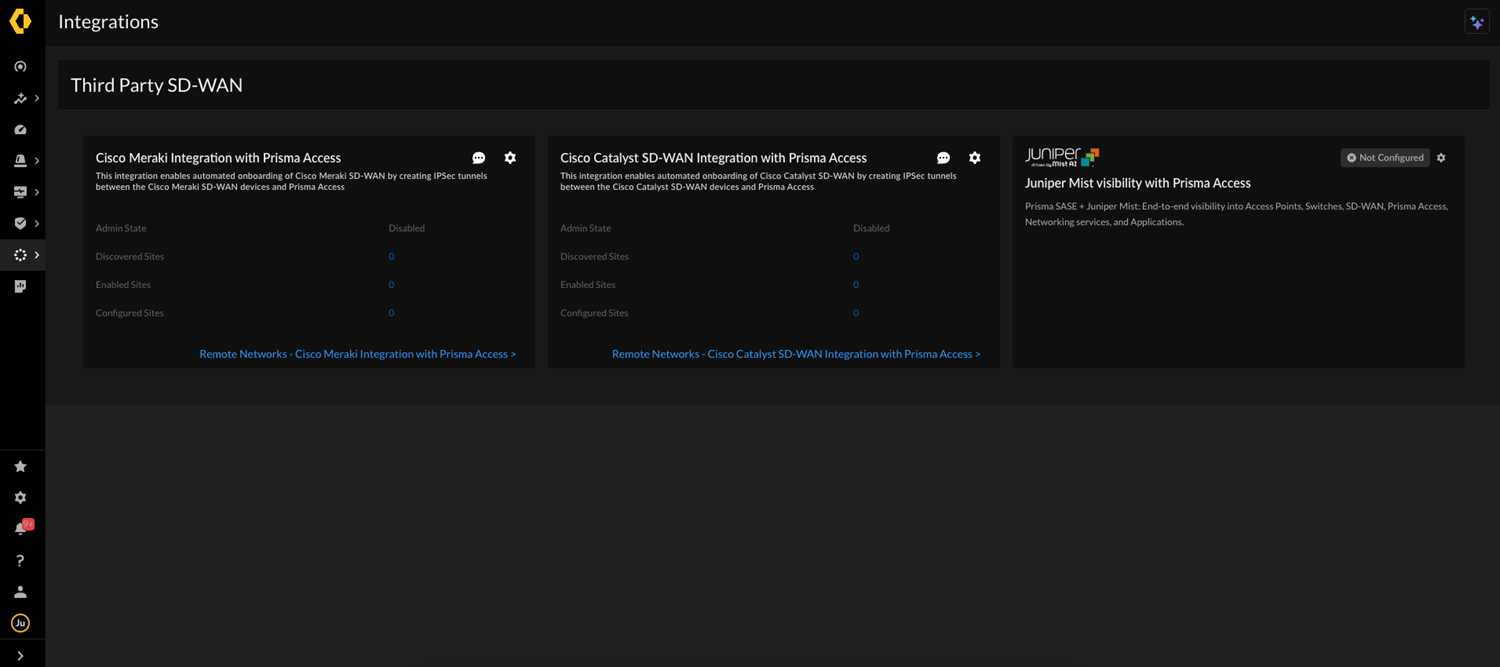
Copy and securely save this API token, as it will be required later in the Juniper Mist integration process. It will not be visible again after you leave this page.Configuring visibility on Strata Cloud Manager with Juniper Mist Integration in Prisma Access.- In Strata Cloud Manager, go to System SettingsIntegrationsPrisma Access.Locate the Juniper Mist visibility with Prisma Access application in the Third Party SD-WAN screen.
![]() Contact your Palo Alto Networks account team if you don’t see this integration option.Enter the information to establish a connection between Prisma Access and Juniper Mist by editing the Settings.
Contact your Palo Alto Networks account team if you don’t see this integration option.Enter the information to establish a connection between Prisma Access and Juniper Mist by editing the Settings.![]()
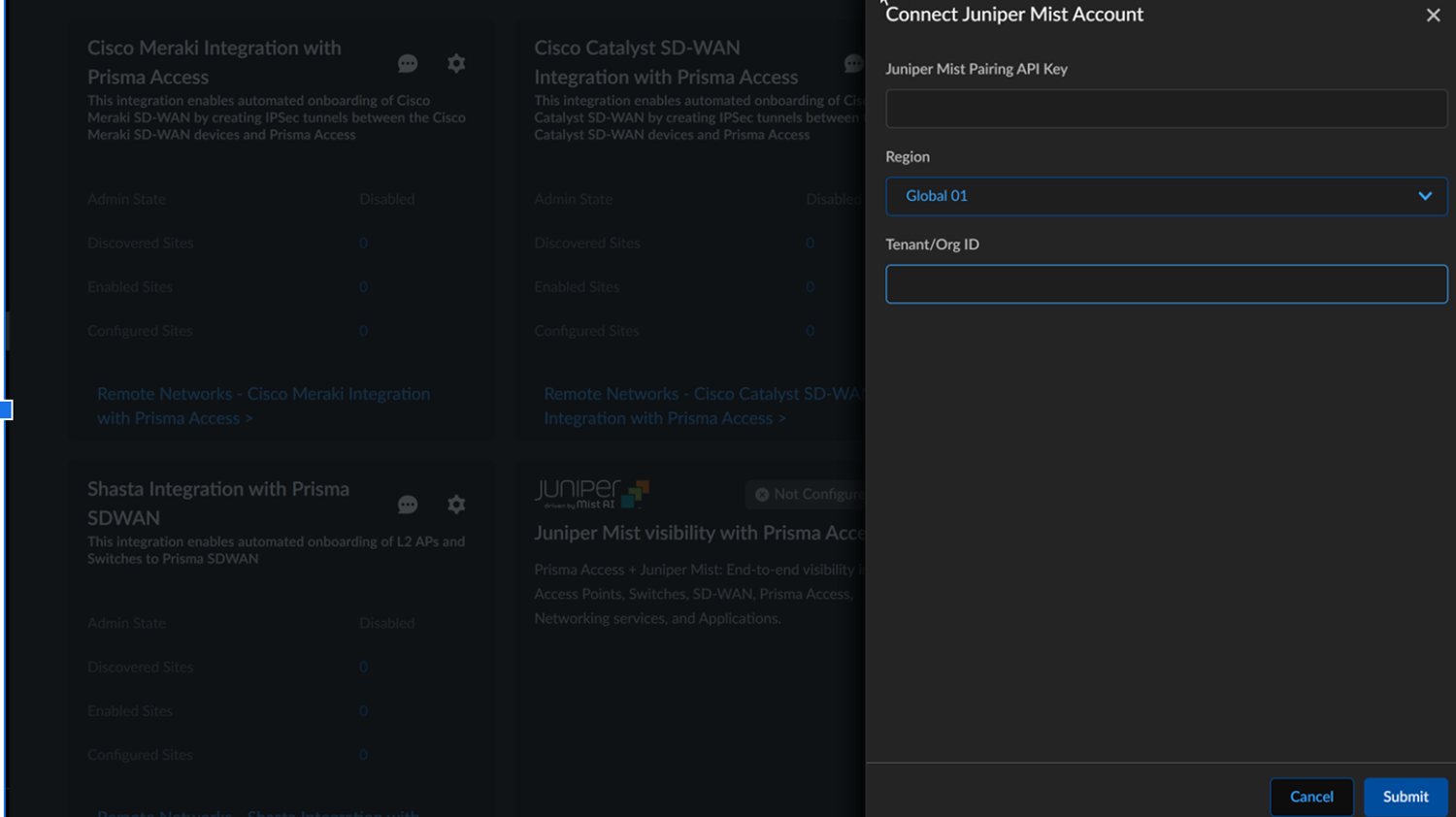
- Enter Juniper Mist Pairing API Key generated previously from the Juniper Mist dashboard, and enter the key information.
- Select the Region associated with the Juniper Mist organization.
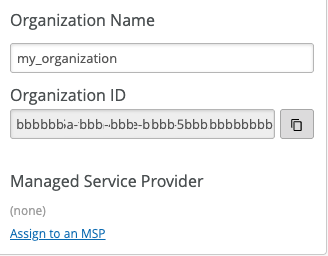
- Enter the Organization ID configured in
the Juniper Mist web interface.
![]()
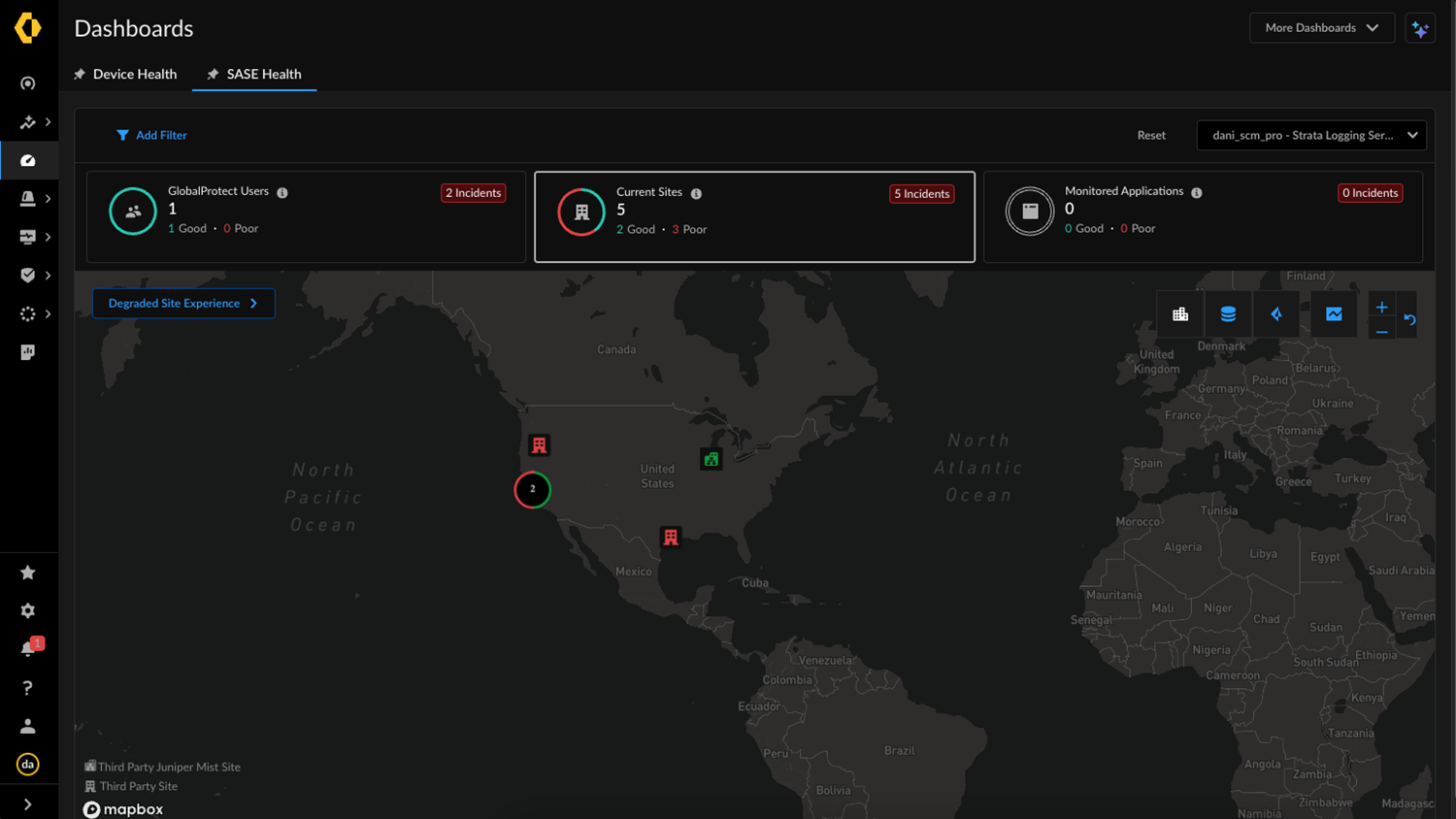
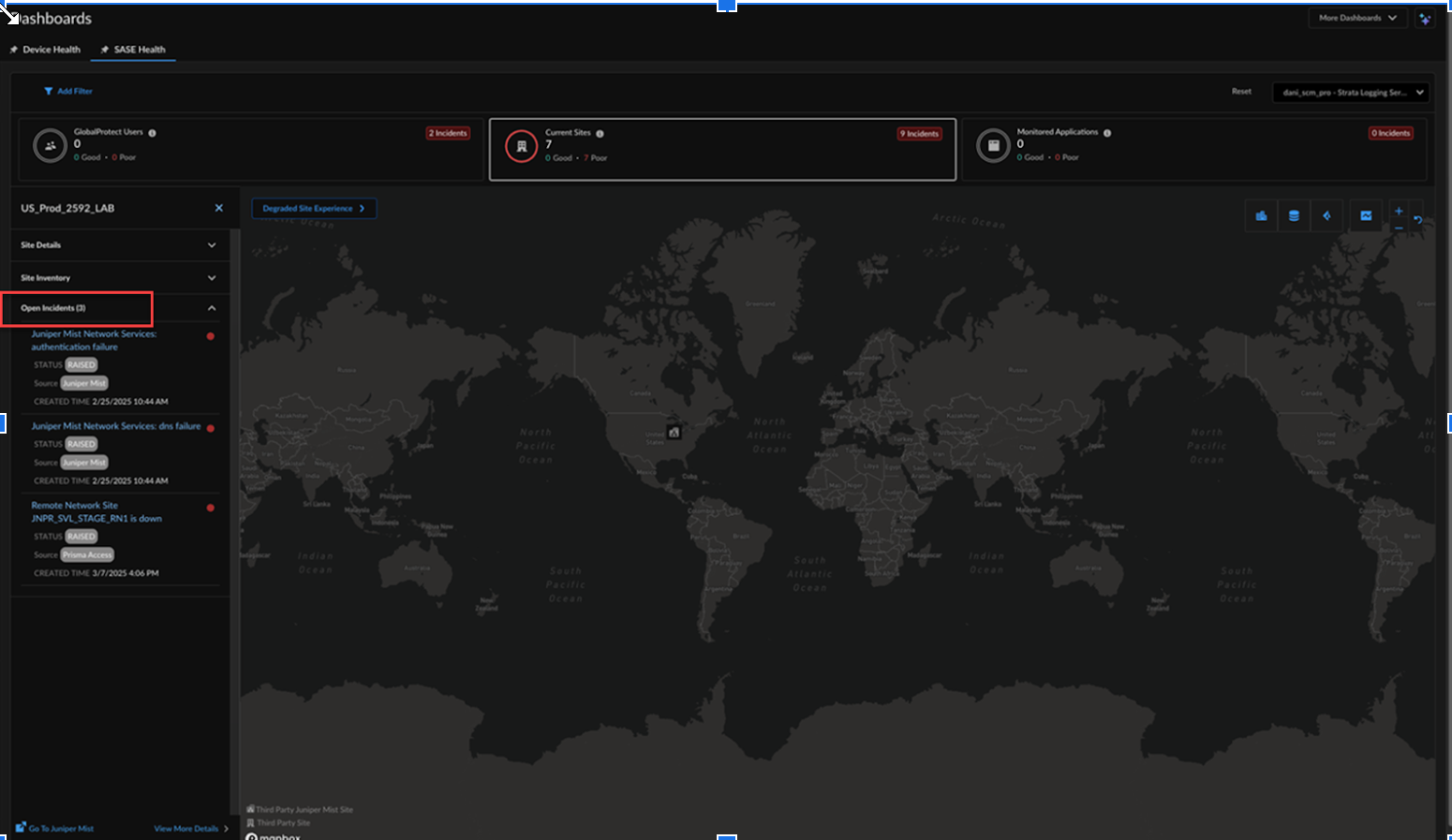
Save the changes.Once complete, the integration maps Prisma Access for Networks branch sites based on the tunnels set up between Juniper Mist site's WAN Edge and Prisma Access (PA) locations. If the tunnels are active, the site is mapped and starts appearing as a Third Party Juniper Mist Site.Monitor the Jupiter Mist Third Party Integration Sites.In Strata Cloud Manager, the SASE HealthCurrent Sites dashboard provides an overview of configured third-party sites, including Juniper Mist sites. It displays the total number of connected sites, the number of sites with a Good or Poor (degraded) experience, and the total number of incidents across all sites. A site is considered to have a Poor experience if it has any open incidents. Strata Cloud Manager primarily use green and red color coding for visual indication.![]() A site's experience may be considered degraded based on open incidents, which are categorized into infrastructure, network services, data centers (indicating unreachable data centers), and third-party sites. Additionally, new segments include Juniper Mist Access Points, Juniper Mist Switches, Juniper Mist WAN Edges, and Juniper Mist Network Services. Juniper Mist branch sites are marked with a Juniper Mist icon. While there can be multiple sites, at least one site must have tunnels to a Prisma Access location for a third-party site to be mapped as a Juniper Mist third-party site.
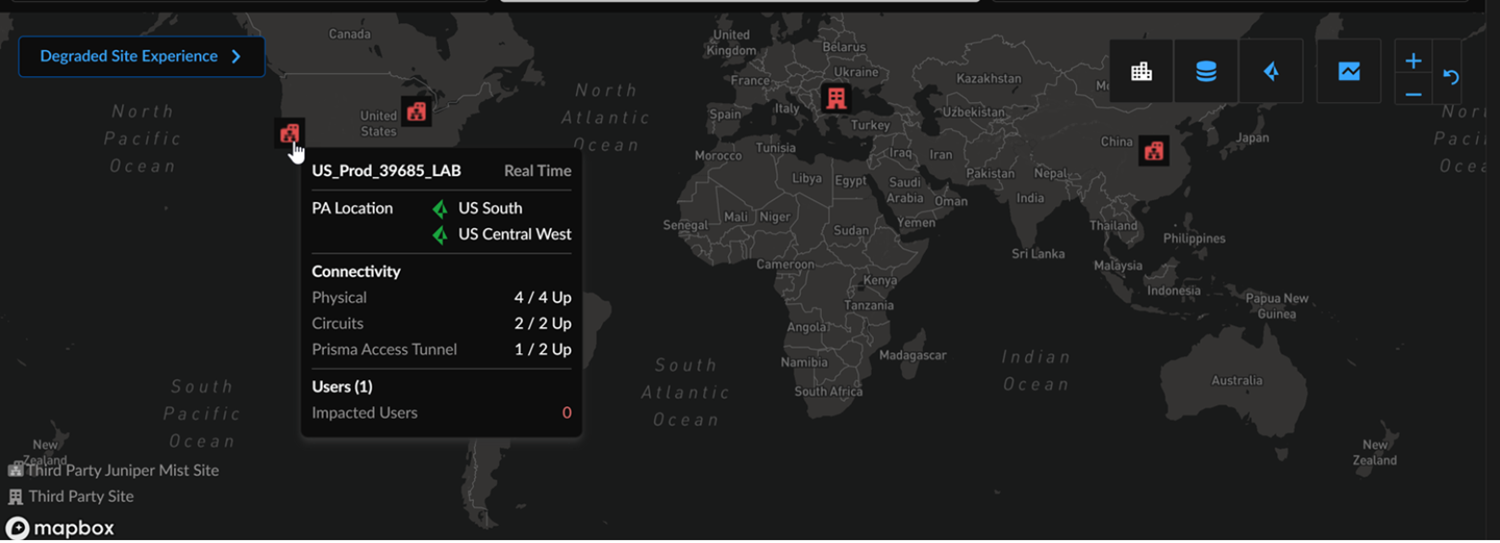
A site's experience may be considered degraded based on open incidents, which are categorized into infrastructure, network services, data centers (indicating unreachable data centers), and third-party sites. Additionally, new segments include Juniper Mist Access Points, Juniper Mist Switches, Juniper Mist WAN Edges, and Juniper Mist Network Services. Juniper Mist branch sites are marked with a Juniper Mist icon. While there can be multiple sites, at least one site must have tunnels to a Prisma Access location for a third-party site to be mapped as a Juniper Mist third-party site.- Hover over a Juniper Mist branch site to view site details, including the Prisma Access locations (Primary and Secondary), connectivity information (physical/circuits and Prisma Access tunnel status), and user information.Polling data may have up to a 10-minute delay. An approximate count of connected and impacted users is shown for the given site. An impacted user count greater than 0 is derived from Juniper Mist Network Services type incidents.
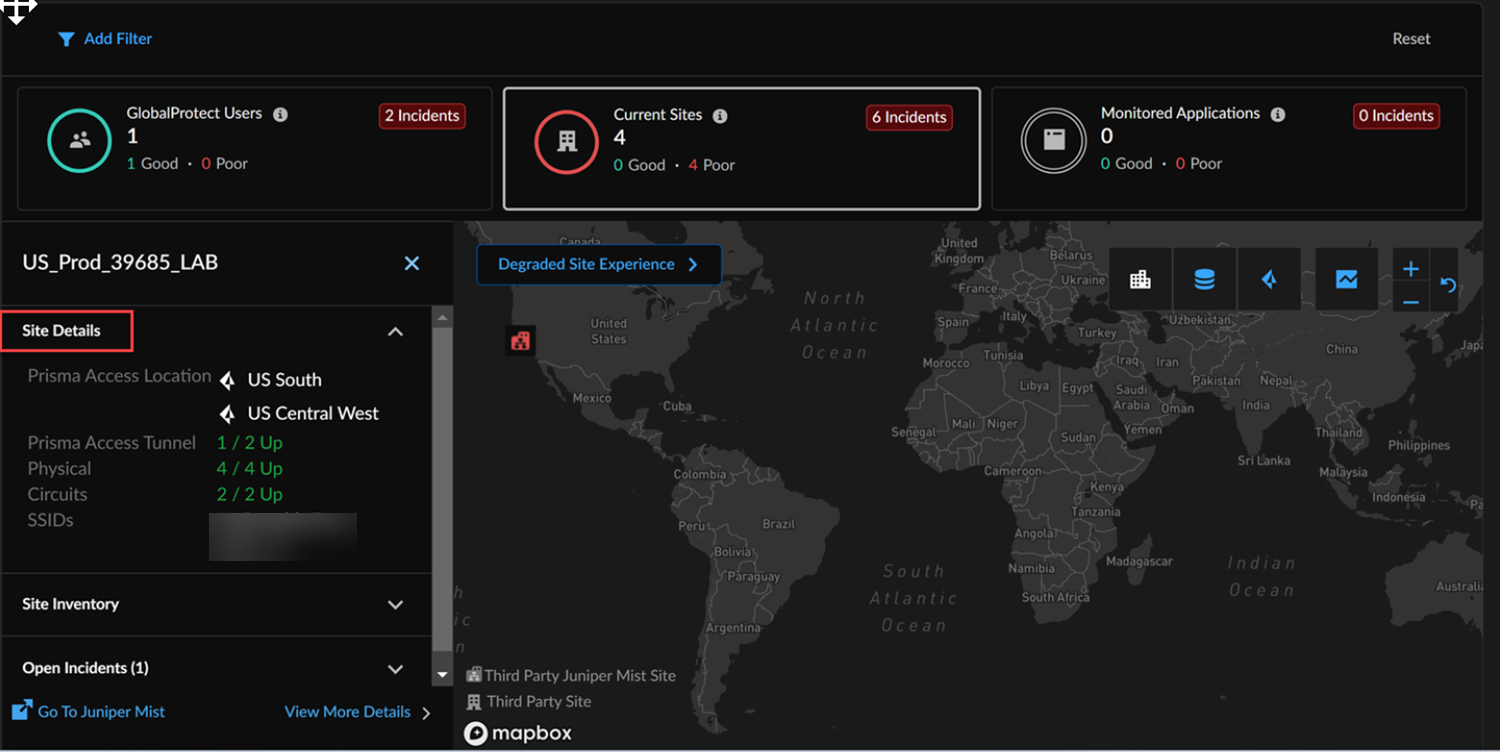
![]() Select a Branch Site to view the Site Details in the left panel, including Prisma Access locations, tunnel status, physical/circuit WAN Edge device information, and available networks by hovering over SSIDs. These details are sourced from Juniper Mist and Prisma Access.
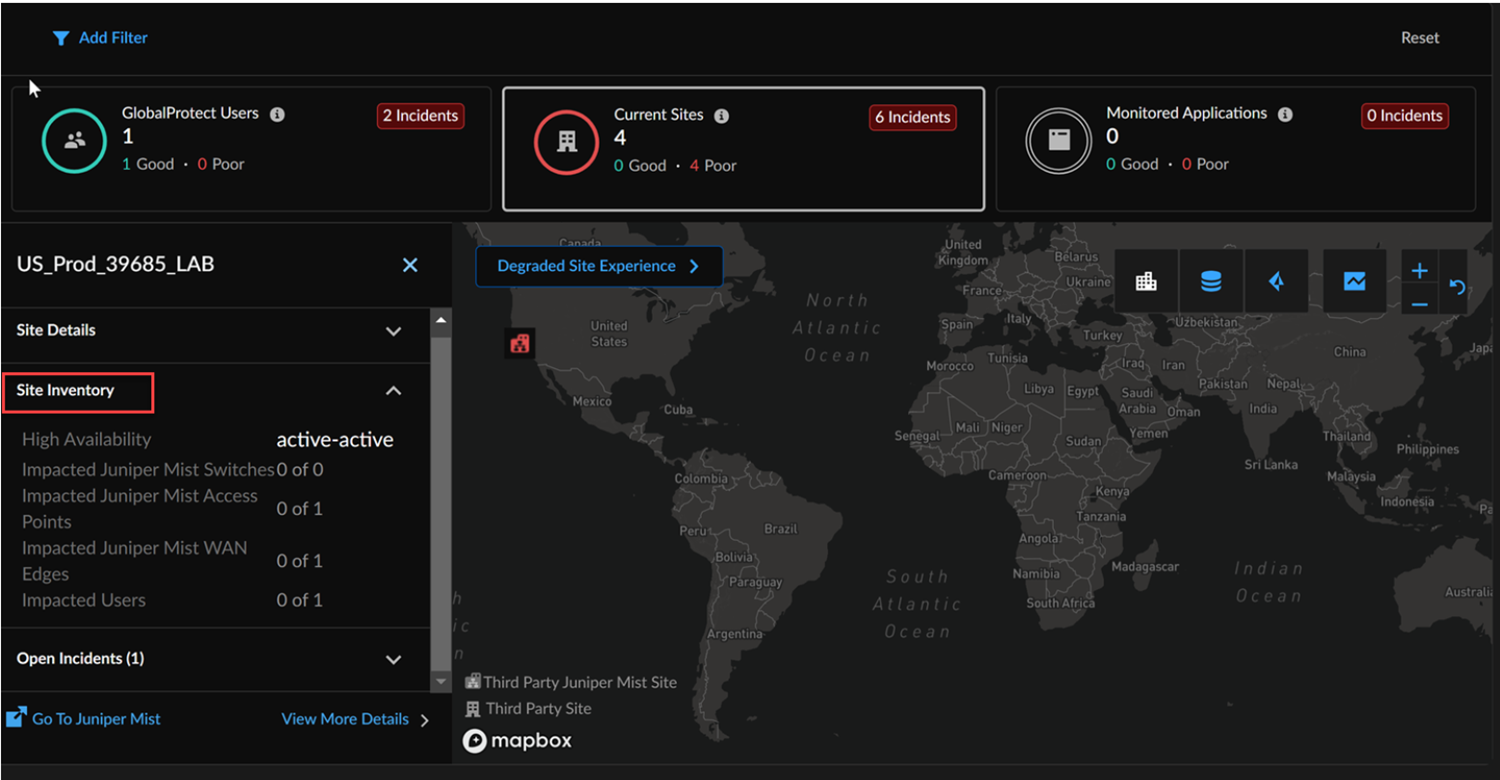
Select a Branch Site to view the Site Details in the left panel, including Prisma Access locations, tunnel status, physical/circuit WAN Edge device information, and available networks by hovering over SSIDs. These details are sourced from Juniper Mist and Prisma Access.![]() Select Site Inventory to view high availability of the Juniper Mist site configuration. It also shows the number of impacted users along with the impact reason.
Select Site Inventory to view high availability of the Juniper Mist site configuration. It also shows the number of impacted users along with the impact reason.![]() The following are the alert categories in Juniper Mist:
The following are the alert categories in Juniper Mist:- Access Point (AP): Alerts related to the status and performance of wireless access points.
- Switch: Notifications concerning switch operations and connectivity.
- WAN Edge: Alerts pertaining to WAN edge functionality issues.
- Connectivity: Warnings about network connectivity problems, including authentication failures, DHCP issues, ARP anomalies, and DNS resolution failures.
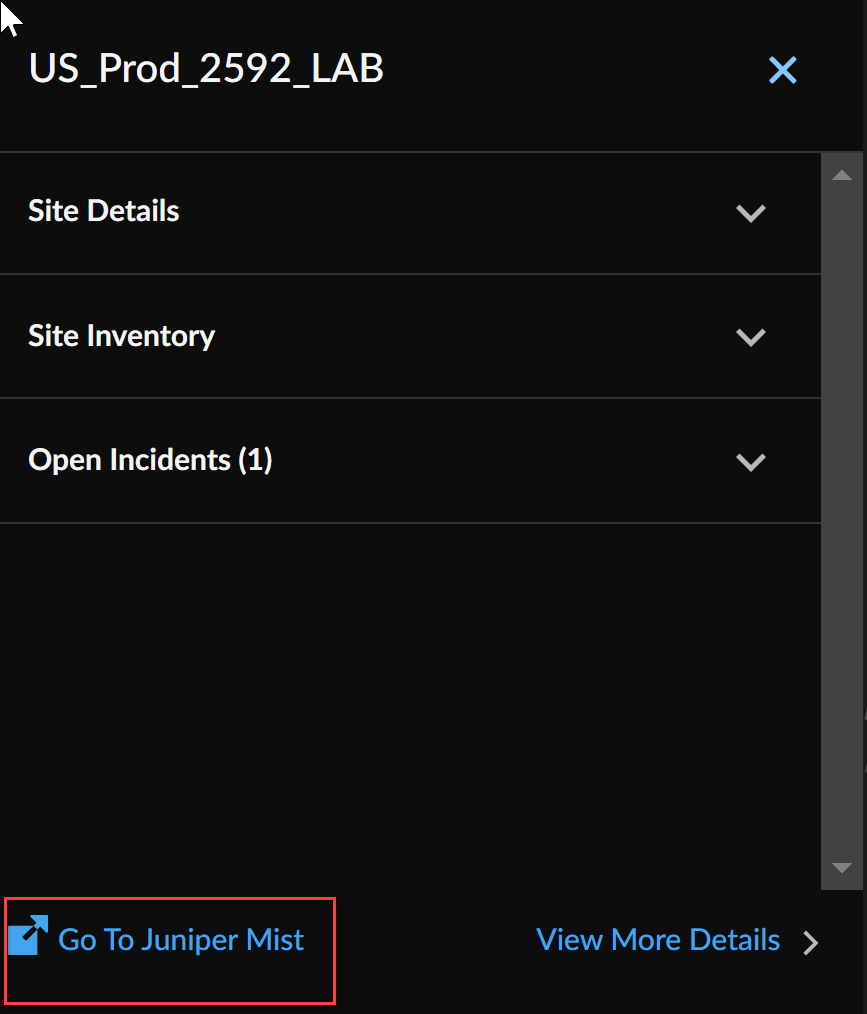
This document has the complete list of all available Juniper Mist Marvis alerts.Select Open Incidents to view details such as incident status, source, and time of incident creation. Clicking on a Juniper Mist source type incident opens the Juniper Mist Incident View for more information, while Prisma SASE incidents redirect to the Incidents & Alerts page on Strata Cloud Manager.![]() Select Go to Juniper Mist to navigate to the Juniper Mist page, pre-filtered for the specific branch site.
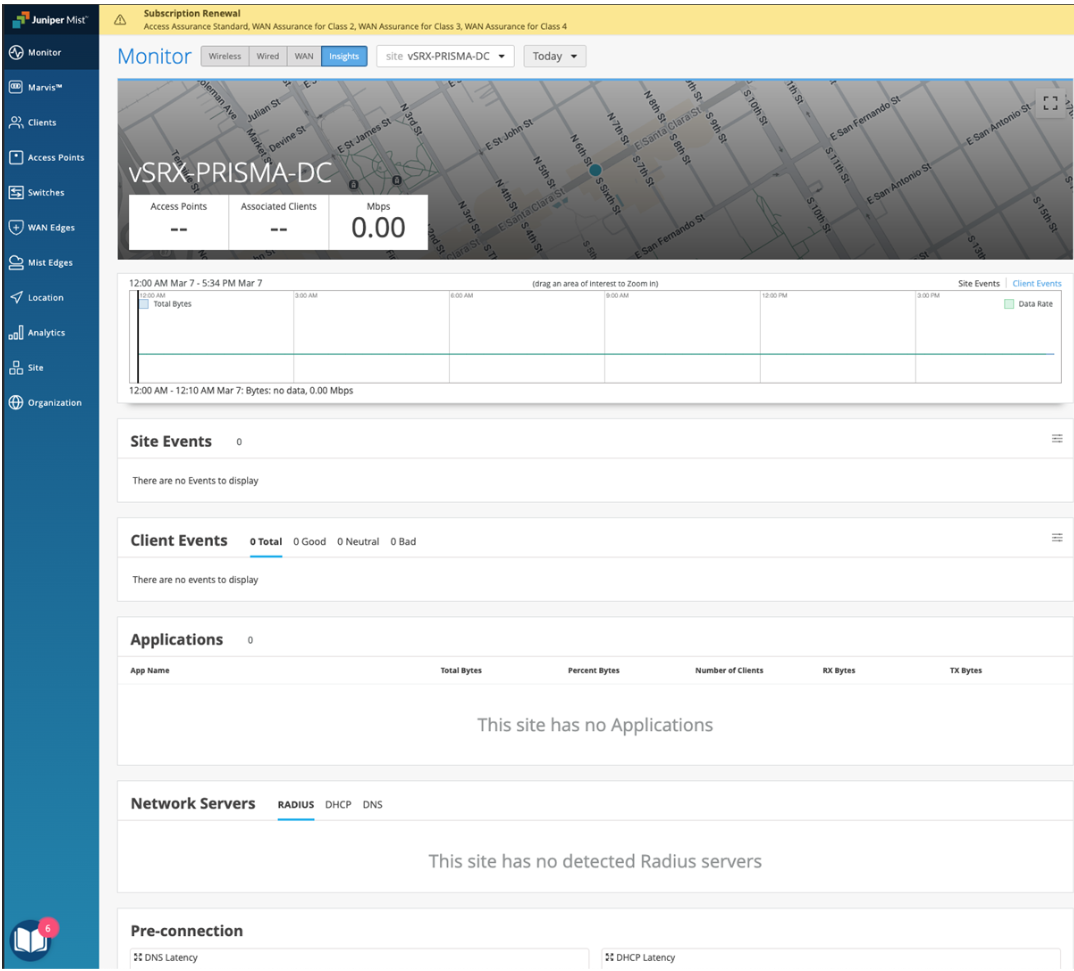
Select Go to Juniper Mist to navigate to the Juniper Mist page, pre-filtered for the specific branch site.![]()
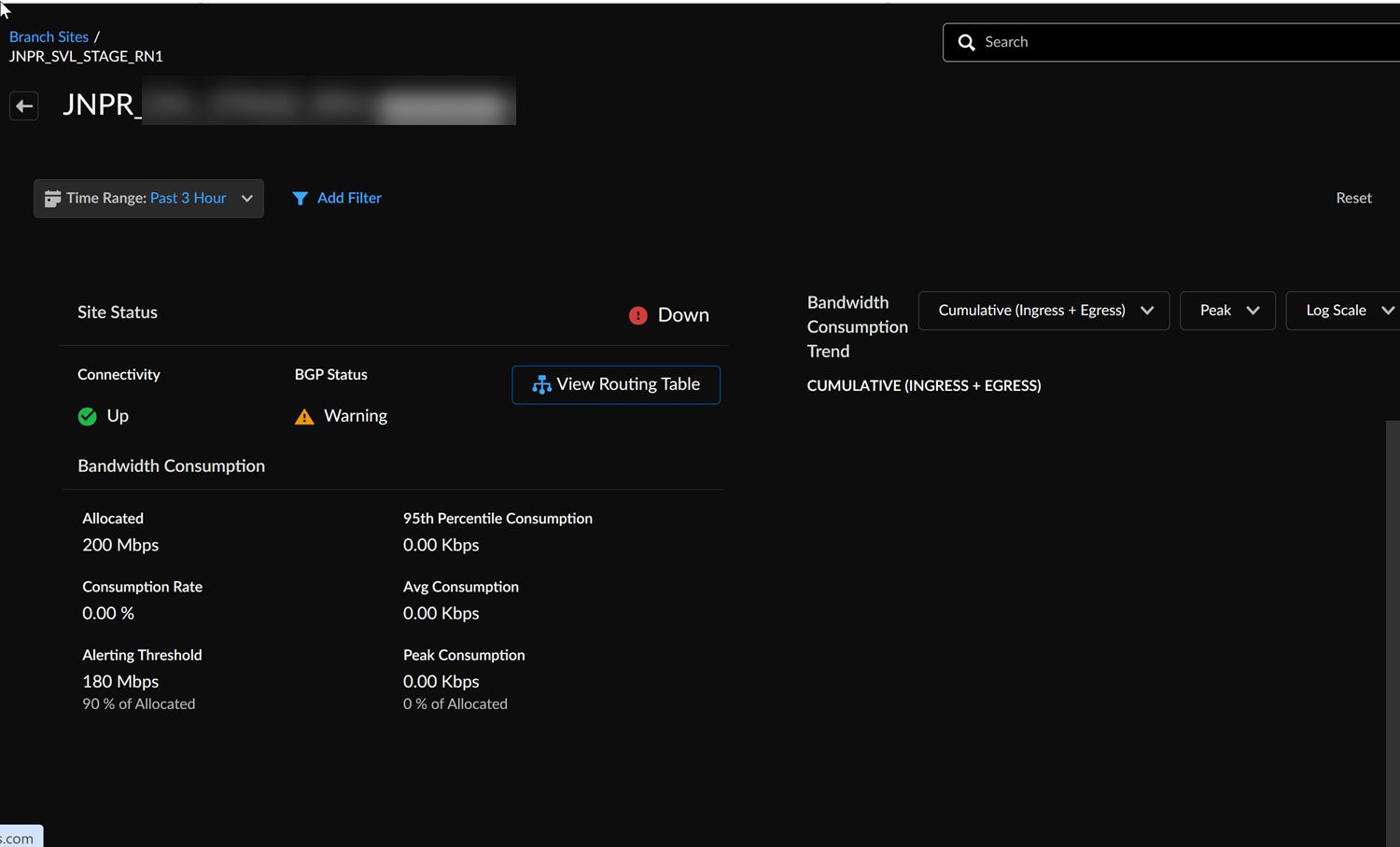
![]() Click View More Details to view the Prisma Access for Networks branch site details.
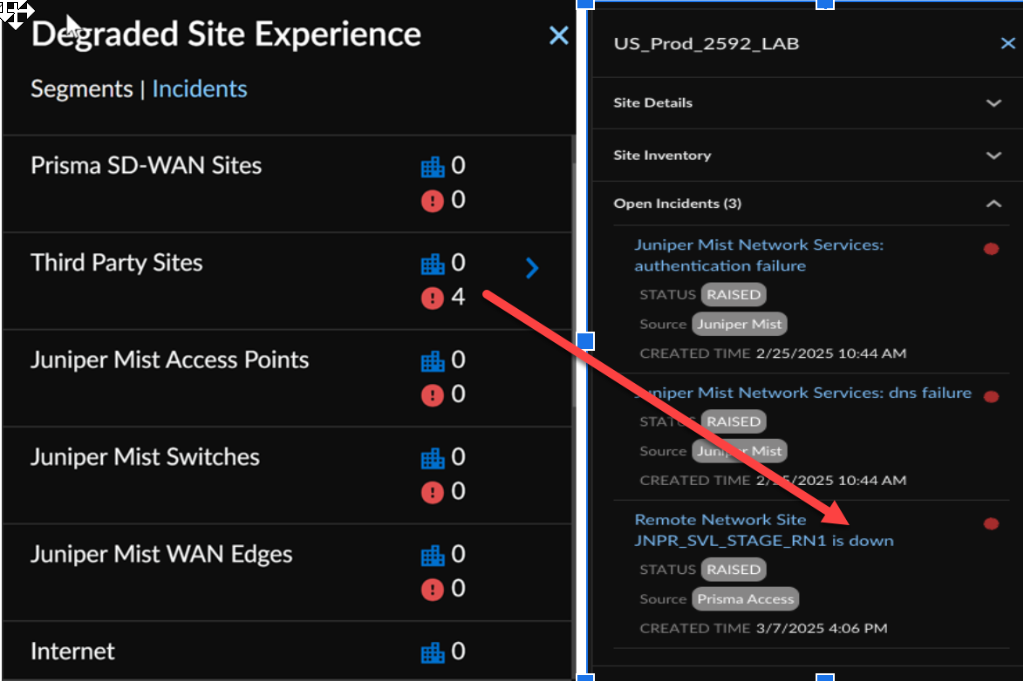
Click View More Details to view the Prisma Access for Networks branch site details.![]() Select Degraded Site Experience to view data categorized by Incidents and Segments. When navigating from SegmentsIncidents, only incidents related to that segment are displayed. Selecting Incidents directly will show a complete list of all incidents. You can further drill down into a specific incident by selecting the one you want to investigate.
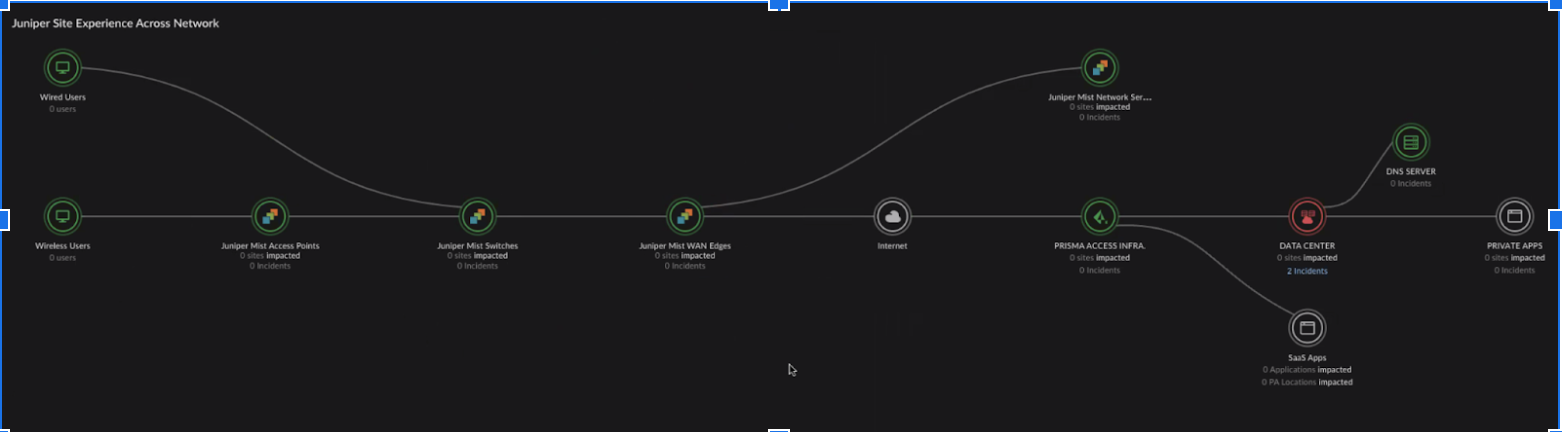
Select Degraded Site Experience to view data categorized by Incidents and Segments. When navigating from SegmentsIncidents, only incidents related to that segment are displayed. Selecting Incidents directly will show a complete list of all incidents. You can further drill down into a specific incident by selecting the one you want to investigate.![]() Select the Experience Trends & Network Topology icon to view a time series, followed by the end-to-end topology chart for Prisma SASE and Juniper Mist.
Select the Experience Trends & Network Topology icon to view a time series, followed by the end-to-end topology chart for Prisma SASE and Juniper Mist.![]()