Prisma Access
Multitenancy Configuration Overview
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Multitenancy Configuration Overview
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Enabling multitenancy allows you to host multiple instances of Prisma Access on a
single Panorama appliance. Each instance is known as a Tenant.
Prisma Access tenants get their own dedicated Prisma Access instances and they are
not shared between tenants.
Use the following workflow to configure the ability to manage multiple tenants in a
single Panorama appliance:
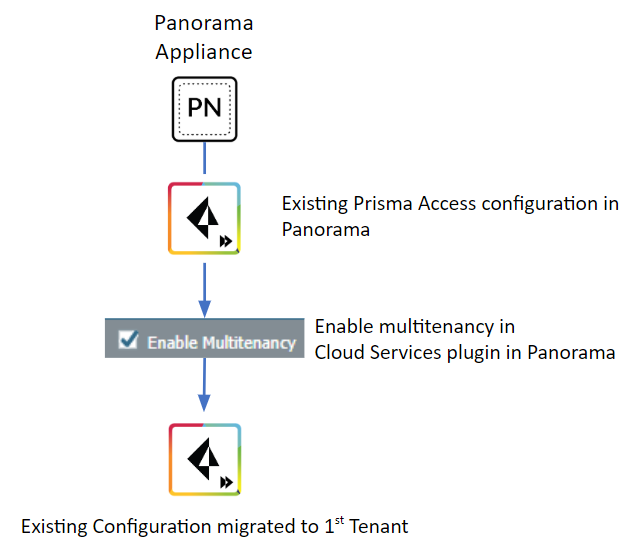
- Enable multitenancy. If you have an existing Prisma Access instance, enabling multitenancy automatically migrates your existing Prisma Access configuration to the first tenant.You give the first (migrated) tenant a name and specify an access domain. Prisma Access migrates the templates, template stacks, and device groups associated with the existing configuration and associates them with the access domain you create.After you migrate your initial configuration, the administrative user in Panorama becomes a superuser with the ability to create and manage all Prisma Access tenants.
![]() Then, add tenants to Prisma Access.To deploy multiple tenants, make sure that you have the following license minimums:To determine the type of Prisma Access license you have from Panorama, select PanoramaLicenses.
Then, add tenants to Prisma Access.To deploy multiple tenants, make sure that you have the following license minimums:To determine the type of Prisma Access license you have from Panorama, select PanoramaLicenses.- If you have a Business, Business Premium, Zero Trust Network Access (ZTNA) Secure Internet Gateway (SIG), or Enterprise license, use the following minimums as a guideline:Prisma Access for Networks and Prisma Access for Users:The minimum quantity for all tenants is 200.Units correspond to bandwidth in Mbps for Prisma Access for Remote Networks and the number of mobile users for Prisma Access for Users.
- If your license type starts with GlobalProtect Cloud Service, use the following minimums as a guideline:Prisma Access for Networks—You must have a minimum of 200 Mbps available in your license for each tenant.Prisma Access for Users—You must have a minimum of 200 mobile users available in your license for each tenant.In both types of Prisma Access configurations, you can add additional licensing (above these minimums) of either type. You can increase or decrease the bandwidth or mobile user allocation for any tenants after onboarding, as long as you keep the minimum required allocation per tenant, and the overall licensed capacity is not exceeded.
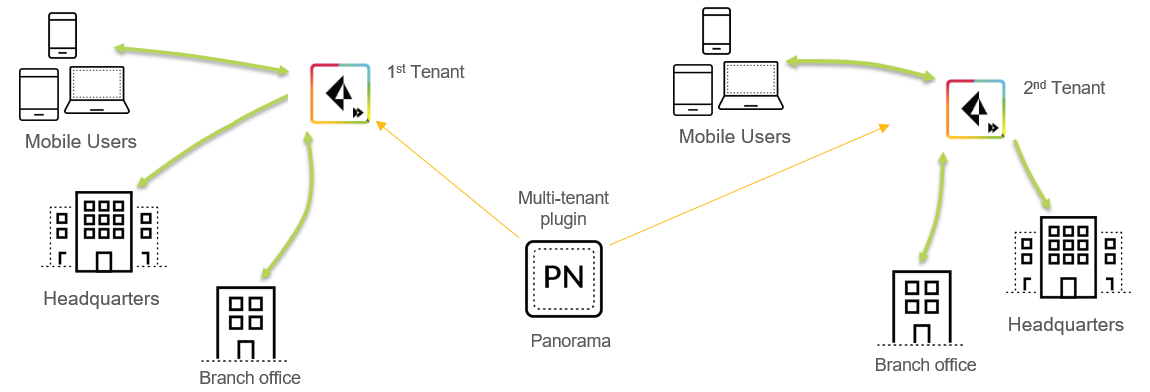
You can set up a multitenant configuration for only remote networks, only mobile users, or both. You allocate licenses accordingly to each tenant when you enable multitenancy.If you have a license for remote networks and mobile users, you can set up an individual tenant with only mobile users or only remote networks.For each tenant you create after the first, Prisma Access automatically creates templates, template stacks, and device groups for each tenant and associates them to the access domain you create. Prisma Access creates this environment to allow you to create a tenant-level administrative userusing an administrative role based on the tenant’s device groups and templates, then creating an administrative user based on that role. In this way, you create an administrative user that has access to a single tenant without allowing that user access to the other tenants that are managed by the Panorama appliance.Prisma Access creates template stacks, templates, and device group using the following naming convention:- A service connection template stack with the name of sc-stk-tenant, where tenant is the tenant’s name.
- A service connection template with the name of sc-tpl-tenant.
- A service connection device group with the name of sc-dg-tenant.
- A mobile user template stack with the name of mu-stk-tenant.
- A mobile user template with the name of mu-tpl-tenant.
- A mobile user device group with the name of mu-dg-tenant.
- A remote network template stack with the name of rn-stk-tenant.
- A remote network template with the name of rn-tpl-tenant.
- A remote network device group with the name of rn-dg-tenant.
- An Explicit Proxy template stack with the name of ep-stk-tenant.
- An Explicit Proxy template with the name of ep-tpl-tenant.
- An Explicit Proxy device group with the name of ep-dg-tenant.
- A Clean Pipe template stack with the name of cp-stk-tenant.
- A Clean Pipe template with the name of cp-tpl-tenant.
- A Clean Pipe device group with the name of cp-dg-tenant.
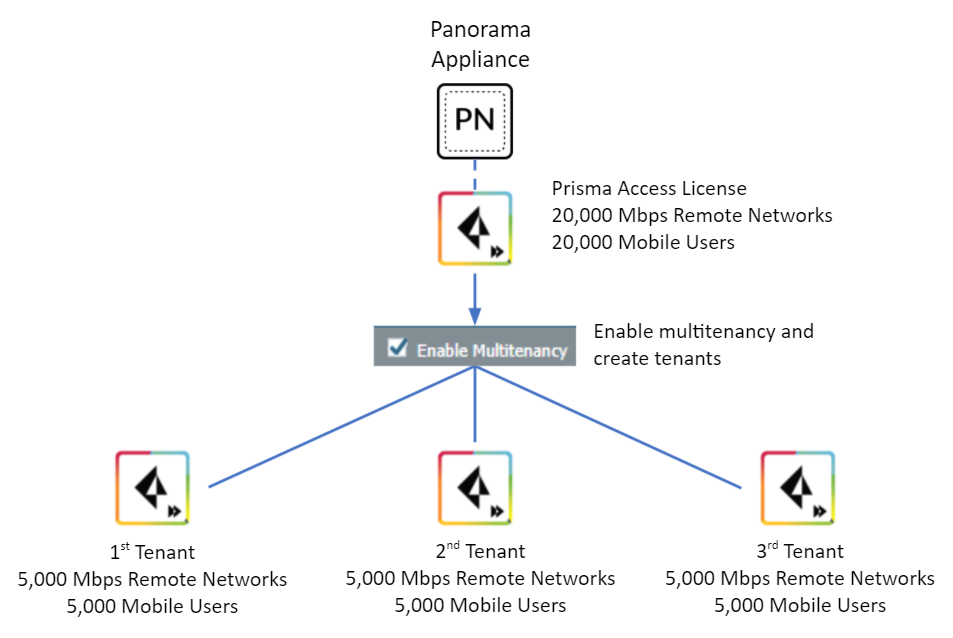
Template stacks, templates, and device groups are created for all Prisma Access types, even those for which you might not be licensed. For example, if you purchase a license for remote networks, Prisma Access automatically creates template stacks, templates, and device groups for remote networks, mobile users, and Clean Pipe.If you add custom templates, they cannot take precedence over the Prisma Access-created templates.You allocate remote network and mobile user license resources for each tenant based on the license that is associated with the Cloud Services plugin in Panorama.The following figure shows a sample Prisma Access deployment using a license with a 20,000 Mbps remote network bandwidth pool and 20,000 mobile users. The administrator allocated 5,000 Mbps in remote network bandwidth and 5,000 mobile users for the existing configuration. After the administrator enabled multitenancy, the license allocation migrated along with all other configuration to the first tenant. The administrator then created additional tenants, each with a 5,000 Mbps bandwidth pool for remote networks and 5,000 mobile users for each tenant. Prisma Access allocates the license resources from the overall license allocation. After you complete this configuration, there is 5,000 Mbps of remote network bandwidth and 5,000 mobile users available in the license.![]()