Prisma Access
New Features in Prisma Access 5.0 and 5.0.1
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
New Features in Prisma Access 5.0 and 5.0.1
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
The following sections describe the new features that are available with Prisma Access 5.0 and 5.0.1 Preferred and Innovation, in addition to infrastructure, plugin, and
dataplane dependencies for these.
- Recommended Software Versions for Prisma Access 5.0 and 5.0.1 Preferred and Innovation
- Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.0 and 5.0.1 Preferred and Innovation Features
- Features in Prisma Access 5.0
- Features in Prisma Access 5.0.1
Recommended Software Versions for Prisma Access 5.0 and 5.0.1 Preferred and Innovation
There are two Prisma Access 5.0 and 5.0.1 versions:
- 5.0 and 5.0.1 Preferred run a PAN-OS dataplane earlier than 10.2.8. If you're running Prisma Access 4.0, 4.1, or 4.2, a dataplane upgrade isn't required.
- 5.0 and 5.0.1 Innovation run a minimum PAN-OS dataplane of 10.2.8 and unlock the features that are available with that dataplane.
For new Prisma Access 5.0 Innovation features, Palo Alto Networks
recommends that you upgrade your Prisma Access deployment to the versions listed in this section before
installing the plugin (note that the Prisma Access 5.0 release supports
the same
minimum requirements as Prisma Access 4.0). Also note that, for access
to all features, you will need to upgrade your dataplane to a minimum version of
10.2.8, which is required for Prisma Access 5.0 Innovation.
Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.0 and 5.0.1 Preferred and Innovation Features
Prisma Access 5.0 and 5.0.1 features require one of more of the following
components to function:
- Infrastructure Upgrade—The infrastructure includes the underlying
service backend, orchestration, and monitoring infrastructure. Prisma Access upgrades the infrastructure before the general
availability (GA) date of a Prisma Access release. Features that require only an infrastructure upgrade to be enabled take effect for all Prisma Access deployments, regardless of version, at the time of the infrastructure upgrade.
- Plugin Upgrade (Prisma Access (Managed by Panorama) Deployments Only)—Installing the 5.0 plugin activates the features that are available with both Prisma Access 5.0 and 5.0.1. You download and install the 5.0 plugin on the Panorama that manages Prisma Access.
- Dataplane Upgrade—The dataplane enables traffic inspection and
security policy enforcement on your network and user traffic. For Prisma Access (Managed by Panorama) deployments, you can view your dataplane version by going to PanoramaCloud ServicesConfigurationService Setup and viewing the Prisma Access Version.
![]()
This dataplane upgrade to 5.0 Innovation is optional, and is
only required if you want to take advantage of the features that require a dataplane
upgrade. For minimum Panorama and GlobalProtect versions, the Prisma Access
5.0 release supports the same versions as
Use this table to determine what features require an infrastructure, plugin, and
dataplane upgrade. A check mark (√) indicates that an upgrade is required, a dash
(—) indicates that it's not required.
| Feature | Infrastructure Upgrade Required | Plugin Upgrade Required | Dataplane Upgrade Required |
|---|---|---|---|
| 5.0 Features: | |||
| Integrate Prisma Access with Microsoft Defender for Cloud Apps (minimum 10.2.4 dataplane required) | √ | √ | — |
| Traffic Replication Remote Network and Strata Cloud Manager Support | √ | √ | √ Upgrade to 5.0 Innovation required. |
| Maximum of 500 Remote Networks Per Termination Node for 1 Gbps Remote Networks | √ | √ | √ Upgrade to 5.0 Innovation required. |
| 5.0.1 Features: | |||
| IP Optimization for Mobile Users—GlobalProtect Deployments (available for new customers only and minimum GlobalProtect app 6.1.4+, 6.2.3+, or 6.3+ version required for endpoints) | √ | √ | √ |
| App Acceleration—Dynamic Content Acceleration for Top SaaS Apps | √ | √ | √ Upgrade to 5.0 Innovation required. |
Features in Prisma Access 5.0
The following section describes the new features that are available with Prisma Access 5.0.
Prisma Access Application Name Update
|
Supported in:
Prisma Access (Managed by Strata Cloud Manager) starting November 18, 2023
|
The application tile names on the hub for Prisma Access, Prisma SD-WAN, and
AIOps for NGFW (the premium app only) are now changed to Strata Cloud
Manager. With this update, the application URL has also changed to stratacloudmanager.paloaltonetworks.com, and
you’ll also now see the Strata Cloud Manager logo on the left navigation
pane.
Moving forward, continue using the Strata Cloud Manager app to manage and
monitor your deployments.
App Acceleration in Prisma Access
|
Supported in:
Prisma Access starting with release 5.0 Innovation.
|
When your users access apps, they can experience poor app performance due
to decreased throughput. This condition can be caused by degraded wireless
connectivity, network congestion, and other factors. These networking issues can
adversely affect the employee experience and can reduce their productivity.
App Acceleration directly addresses the
causes of poor app performance and acts in real-time to boost throughput while
maintaining best-in-class security, dramatically improving the user experience for
Prisma Access GlobalProtect and Remote Network users.
Without requiring any changes to your applications, App Acceleration
securely builds an understanding of:
- Device capability—The type of client endpoint
- Network capability—The type of network
- App Context— The type of app being used
Using its understanding of network, device, and application context, App
Acceleration maximizes throughput and adjusts in real-time to account for changing
network conditions.
When compared to direct internet access, App Acceleration offers a marked
throughput improvement for TCP traffic when connecting through Prisma Access.
You can view these improvements using Autonomous DEM (ADEM), which provides
you with metrics such as throughput per application and the data and apps that were
accelerated. Using this information, you can pinpoint how App Acceleration improved
the app experience for your users.
Remote Browser Isolation
|
Supported in:
Prisma Access starting with release 5.0 Innovation.
|
Browser and web-based attacks are continuously evolving, resulting in security
challenges for many enterprises. Web browsers, being a major entry point for malware
to penetrate networks, pose a significant security risk to enterprises, prompting
the increasing need to protect networks and devices from zero day attacks. Highly
regulated industries, such as government and financial institutions, also require
browser traffic isolation as a mandatory compliance requirement.
While most enterprises want to block 100% of attacks by using network security and
endpoint security methods, such a goal might not be realistic. Most attacks start
with the compromise of an endpoint that connects to malicious or compromised sites
or by opening malicious content from those sites. An attacker only needs one miss to
take over an endpoint and compromise the network. When this happens, the
consequences of that compromise and the impact to your organization can be
damaging.
Remote Browser Isolation (RBI) creates a no-code
execution isolation environment for a user's local browser, so that no website code
and files are executed on their local browser. Unlike other isolation solutions, RBI
uses next-generation isolation technologies to deliver near-native experiences for
users accessing websites without compromising on security.

RBI is a service that isolates and transfers all browsing activity away from the
user's managed devices and corporate networks to an outside entity such as Prisma
Access, which secures and isolates potentially malicious code and content within
their platform. Natively integrated with Prisma Access, RBI allows you to apply
isolation profiles easily to existing security policies. Isolation profiles can
restrict many user controls such as copy and paste actions, keyboard inputs, and
sharing options like file uploading, downloading, and printing files to keep
sensitive data and information secure. All traffic in isolation undergoes analysis
and threat prevention provided by Cloud-Delivered Security Services (CDSS) such as
Advanced Threat Prevention, Advanced WildFire, Advanced URL Filtering, DNS Security,
and SaaS Security.
Service Connection Identity Redistribution Management
|
Supported in:
|
Sometimes, granular controls are needed for user-ID redistribution in
particularly large scale Prisma Access deployments. Service Connection Identity
Redistribution Management lets you select specific service connections for identity redistribution.
By default, all of your service connections, in order of proximity, are
used for identity redistribution. However, you may not know which specific service
connections are being used for identity redistribution at a given moment. And,
depending on the number of service connections you have and the number of User-ID
agents you’ve configured, this method for identity redistribution can test the
limits of your system resources. To solve this, we now give you the option to decide
which service connections you want to use for identity redistribution.
Service Provider Backbone Integration Enhancements
|
Supported in:
|
Integrate Prisma Access with a service provider (SP) backbone, which
allows you (the SP) to assign specific region and egress internet capabilities to
your tenants, providing more granular control over the Prisma Access egress traffic.
Without the SP Backbone feature, Prisma Access egress traffic uses public cloud
providers for network backbone instead.
The following diagram represents Prisma Access egress traffic without SP Backbone
integration.
![]()
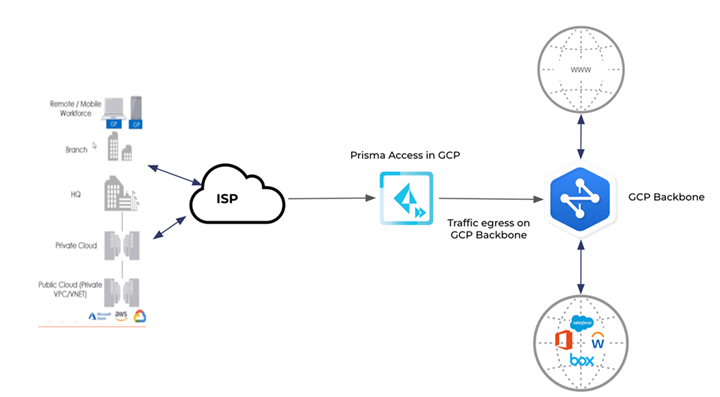
The following diagram represents Prisma Access egress traffic with SP Backbone
integration.
![]()

Traffic Replication Remote Network and Strata Cloud Manager Support
|
Supported in:
Prisma Access starting with release 5.0 Innovation.
|
In addition to providing a copy of the traffic generated by mobile users, traffic replication support for Remote
Networks provides a similar function for the traffic generated by the branches. This
support allows you to have complete visibility for all use cases, along with
consistency in the way the traffic is being captured. The copy of the remote
networks traffic is shared from the same storage buckets as the mobile users
traffic, so existing customers do not have to modify the current deployments. This
option is fully configurable and you have the ability to decide if for a certain
location you need Traffic Replication enabled for mobile users, remote networks, or
both.
Traffic Replication configuration support is added for Cloud Managed Prisma Access and Strata Cloud Manager.
ZTNA Connector Wildcard and FQDN Support for Applications and Additional Diagnostic Tools
|
Supported in:
|
ZTNA Connector offers the following enhancements:
- Applications Based on Wildcards and IP Subnets—In addition to setting up applications based on FQDNs, you can set up applications based on FQDN wildcards and IP subnets.
- For wildcard-based apps, you create an FQDN-based connector group, then
specify the wildcard to use (for example, *.example.com) for the app
target. When users access sites that match the wildcard, those apps are automatically onboarded for access from ZTNA Connector for your mobile users and remote network users. For example, given a wildcard of *.example.com, when users access the app at app1.example.com, ZTNA Connector automatically allows that app to be accessed for mobile users and users at remote network sites.
- For IP subnet-based apps, you create an IP subnet-based Connector group, then enter the IP subnet to use for the app target.
- For wildcard-based apps, you create an FQDN-based connector group, then
specify the wildcard to use (for example, *.example.com) for the app
target.
- Additional Diagnostic Tools—In addition to the existing ZTNA Connector diagnostic tools, more
diagnostic tools are available to help you troubleshoot ZTNA Connector
issues:
- Dump Overview—Allows you to collect a dump of the ZTNA Connector's status.
- Packet Captures—Allows you to capture packets from the ZTNA Connector internal, external, or tunnel interface.
- Tech Support—Allows you to generate and download a tech support file.
- FQDN DNS Resolution to Multiple IP Addresses—If an application FQDN resolves to multiple private IP addresses, the ZTNA connector performs an application probe to determine the status of all resolved IP addresses and load balances the FQDN access to multiple resolved IP addresses that have an application status of Up.
BGP MRAI Configuration Support
|
Supported in:
|
BGP routing offers a timer you can use to tailor BGP routing convergence in your
network called the Minimum Route Advertisement Interval (MRAI).
MRAI acts to rate-limit updates on a per-destination basis, and the BGP routers wait
for at least the configured MRAI time before sending an advertisement for the same
prefix. A smaller number gives you faster convergence time but creates more
advertisements in your network. A larger number decreases the number of
advertisements that can be sent, but can also make routing convergence slower. You
decide the number to put in your network for the best balance between faster routing
convergence and fewer advertisements.
You can configure an MRAI range of between 1 and 600 seconds, with a default value of
30 seconds.
Support for Strata Logging Service Switzerland Region
|
Supported in:
|
Prisma Access supports the Switzerland Strata Logging Service region.
Prisma Access (Managed by Strata Cloud Manager)/Strata Cloud Manager Support for Prisma Access China
|
Supported in:
|
Prisma Access deployments in China provide
you with the following enhanced functionalities:
- To provide you with greater management flexibility, Cloud Managed Prisma Access
is added, allowing you to use either Cloud Managed or Panorama Managed Prisma
Access to manage your deployment in China. Cloud Managed Prisma Access includes the ability to manage your Prisma Access deployment using Strata Cloud Manager. With Strata Cloud Manager, you can easily manage and monitor your network security infrastructure from a single, streamlined user interface. The new platform gives you:
- Best practice recommendations and workflows to strengthen security posture and eliminate risk.
- A common alerting framework that identifies network disruptions, so you can maintain optimal health and performance.
- Enhanced user experience, with contextual and interactive use-case driven dashboards and license-aware data enrichment.
Using cloud management, you can quickly onboard branches and mobile users through task-driven workflows that allow you to set up and test your environment in minutes. Cloud management with Strata Cloud Manager simplifies the onboarding process by providing predefined internet access and decryption policy rules based on best practices. You can quickly set up IPSec tunnels using defaults suitable for the most common IPSec-capable devices and turn on SSL decryption for recommended URL categories. - Cloud managed deployments provide you access to the Prisma SASE Multitenant Portal, allowing you to access Common Services for multiple tenants such as subscription and tenant management and identity and access management.
Integrate Prisma Access with Microsoft Defender for Cloud Apps
|
Supported in:
|
Integrate Prisma Access with Microsoft Defender
for Cloud Apps to sync unsanctioned applications and block them inline
using Prisma Access automatically.
After you integrate Microsoft Defender for Cloud Apps with Prisma Access, Prisma
Access creates a block security policy for URLs that are blocked in Microsoft
Defender for Cloud Apps. You can view the list of unsanctioned applications after
configuring the integration settings. The Prisma Access-Microsoft Defender for Cloud
Apps integration enables you to gain visibility and to discover all cloud
applications and shadow IT applications being used as well as provide closed loop
remediation for unsanctioned applications.
Maximum of 500 Remote Networks Per Termination Node for 1 Gbps Remote Networks
|
Supported in:
Prisma Access starting with release 5.0 Innovation.
|
If your IPSec termination node that you use for
remote network onboarding is configured to
support 1 Gbps of bandwidth, the maximum number of remote networks those IPSec
termination nodes can support is increasing from 400 to 500. You must allocate a
minimum of 501 Mbps for the compute locations associated with the IPSec termination
nodes to have it support up to 1 Gbps of bandwidth.
Deployments using remote networks to onboard Prisma SD-WANs
cannot take advantage of this enhancement.
Enhanced SaaS Tenants Control
|
Supported in:
Prisma Access starting with release 5.0 Innovation.
|
Prisma Access allows you to granularly manage and apply distinct policies for
specific tenants for an extended list of SaaS applications (for example, Github or
Bitbucket). The complete list of apps is documented at https://docs.paloaltonetworks.com/saas-security/saas-security-admin/saas-security-inline/remediate-risks-saas-security-inline/manage-saas-security-inline-policy/create-saas-policy-rule-recommendations
This functionality allows you to enforce use cases where you might need to allow all
actions (for example, uploads and downloads) for a corporate Github account, but
block uploads for a partner instance of the same Github SaaS application.
Enhanced IoT Policy Recommendation Workflow for Strata Cloud Manager
|
Supported in:
|
Rapid IoT adoption is creating new attack vectors and implementing policy
recommendations to apply least privilege Zero Trust policies to secure your
organization's devices is key. If you use Strata Cloud Manager to configure Prisma
Access, you can use enhanced IoT policy recommendation
workflows to accomplish these goals and keep your devices and users
secure.
View and Monitor App Acceleration
|
Supported in:
|
App Acceleration addresses the causes of poor app performance and acts in real-time
to boost throughput while maintaining best-in-class security, improving the user
experience for Prisma Access GlobalProtect and Remote Network users. You can view and monitor App Acceleration to see
details about accelerated applications in your environment. In Strata Cloud Manager,
select MonitorApplications to view details about all accelerated applications.
View and Monitor Remote Browser Isolation
|
Supported in:
|
Remote Browser Isolation (RBI) creates a no-code execution isolation environment for
a user's local browser, so that no website code and files are executed on their
local browser. Unlike other isolation solutions, RBI uses next-generation isolation
technologies to deliver near-native experiences for users accessing websites without
compromising on security.View and monitor RBI to get comprehensive
visibility across your network traffic and for RBI. Gain visibility into your RBI
deployment by viewing metrics such as the number of active RBI users, trends,
connectivity status, RBI location status, traffic measurements, and license
consumption.
View and Monitor ZTNA Connector Access Objects
|
Supported in:
|
View and monitor private apps that were added
through ZTNA Connector access objects by viewing data such as the number
of apps added by FQDNs, IP subnets, and wildcards, each access object's connectivity
status, and the Connector Groups and Connectors associated with each access
object.
The private apps in the data centers connect to Prisma Access through your Connector
virtual machines (VMs). You can add apps based on these access objects—FQDNs, FQDN
wildcards, or IP subnets.
- FQDNs—Prisma Access resolves the FQDNs of the applications you onboard to ZTNA Connector to the IP addresses in the Application IP address block.
- Wildcards—For wildcard-based apps, create an FQDN-based connector group, then specify the wildcard to use (for example, *.example.com) for the app target. When users access sites that match the wildcard, those apps are automatically onboarded for access from ZTNA Connector for your mobile users and remote network users.
- IP Subnets—Create an IP subnet-based Connector group, and then enter the IP subnet to use for the app target.
Features in Prisma Access 5.0.1
The following section describes the new features are available with Prisma Access 5.0.1.
License Enforcement for Mobile Users (Enhancements)
|
Supported in:
|
Prisma Access enforces policies for mobile user licenses
over 30 days instead of 90 days. Though there is no strict policing of the mobile
user count, the service tracks the number of unique users over the last 30 days to
ensure that you have purchased the proper license tier for your user base, and
stricter policing of user count may be enforced if continued overages occur. This
change is applicable for all types of mobile user licenses.
Saudi Arabia Compute Location
|
Supported in:
|
New deployments have the new remapping applied automatically. If you have
an existing Prisma Access deployment that uses one of these locations and you want
to take advantage of the remapped compute location, follow the procedure to add a new compute location to a deployed Prisma
Access location.
Native SASE Integration with Prisma SD-WAN (Strata Cloud Manager Only)
|
Supported in:
|
Effortlessly integrate Prisma SD-WAN with Prisma Access through a native onboarding process. With previous
Prisma Access versions, you needed to configure the additional component — Prisma
Access for Networks (Cloud Managed) CloudBlade to onboard Prisma SD-WAN sites to
Prisma Access. With the native SASE integration between Prisma SD-WAN and Prisma
Access, we have further simplified the onboarding without the need to set up the
CloudBlade.
Prisma Access currently supports this integration only for new Prisma SASE (Strata
Cloud Manager) deployments. For Panorama Managed Prisma Access deployments, continue
using CloudBlades for integration with Prisma SD-WAN.
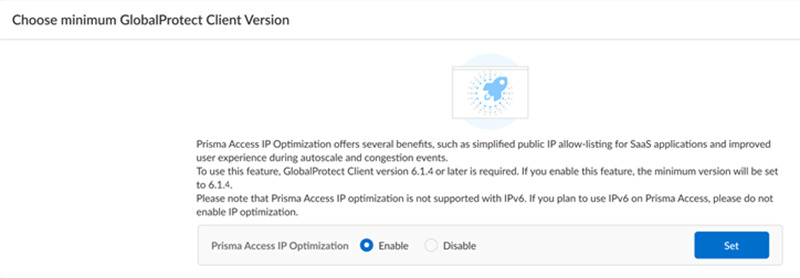
IP Optimization for Mobile Users—GlobalProtect Deployments
|
Supported in:
This functionality is for new Prisma Access GlobalProtect
deployments only. Existing Global Protect deployments are not
eligible, including new tenants you create from an existing
multitenant deployment. In addition, if you are migrating your
GlobalProtect deployment from using on-premises gateways and
portals to Prisma Access, be sure that all users are running
a minimum GlobalProtect app version of 6.1.4+, 6.2.3+, or
6.3+ before enabling this functionality.
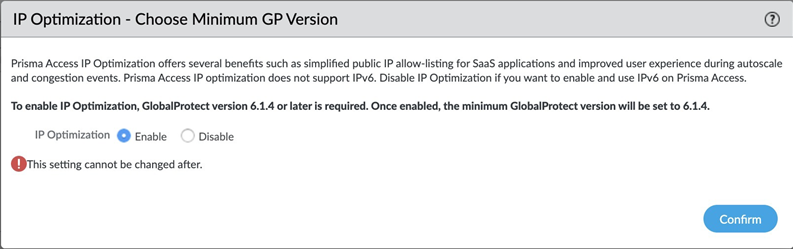
|
IP Optimization is a set of architectural
enhancements that reduce the overall number of IP addresses in your deployment,
simplifying your allow-listing workflows while improving resiliency and enabling
faster onboarding of Prisma Access tenants.
Simpler Public IP Address allow-listing–Adding a Prisma Access location or
experiencing a scaling event at an existing Prisma Access
location could lead to new IP addresses being allocated to the mobile user security
processing node (MU-SPN). It's a best practice to retrieve the new egress, gateway, and network
load balancer IP addresses that Prisma Access assigns and add them to an allow list in your network
to avoid SaaS application or corporate firewall disruption. This can result in a
situation where you're managing a large number of IP addresses. IP Optimization
reduces the number of IP addresses you have to manage.
The API to retrieve Prisma Access IP addresses
continues to work as it always has, even with IP Optimization enabled.
App Acceleration—Dynamic Content Acceleration for Top SaaS Apps
|
Supported in:
|
You can accelerate traffic for top SaaS apps including Salesforce, Google Drive, SAP,
Ariba, and more. The enhancement speeds up dynamic content (for example, dashboards)
up to 5 times faster than direct-to-internet access. If you have already purchased
App Acceleration, you receive this enhancement automatically.
Normalized Username Formats
To better standardize usernames across your organization, all usernames in Prisma
Access have been normalized.
The usernames are standardized based on the following examples.
| Original Username | Normalized Username |
|---|---|
| test.User@abc.com | test.user |
| abc/Test.User | test.user |
| abc//Test.useR | test.user |
This functionality does not affect security policies based on user groups and members
configured using the Cloud Identity Engine.