Prisma Access
GlobalProtect — Customize Tunnel Settings
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
GlobalProtect — Customize Tunnel Settings
Customize the settings for the VPN tunnel the GlobalProtect app establishes to
connect to Prisma Access.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Customize the settings for the VPN tunnel the GlobalProtect app establishes to
connect to Prisma Access. Tunnel settings include split tunneling options that you
can use to define what traffic the app sends to Prisma Access and what can be routed
locally instead (like bandwidth intensive applications that aren’t required for
business use).
The Match Criteria you define for tunnel settings tell Prisma
Access the users, devices, or systems that should receive the settings. For example,
you could specify that a tunnel settings rule applies to all instances of the
GlobalProtect app in a certain region. In Prisma Access (Managed by Panorama), you can configure
split tunnel settings based on Access Route and Domain and Application.
GlobalProtect — Customize Tunnel Settings (Strata Cloud Manager)
Define tunnel settings for GlobalProtect app.
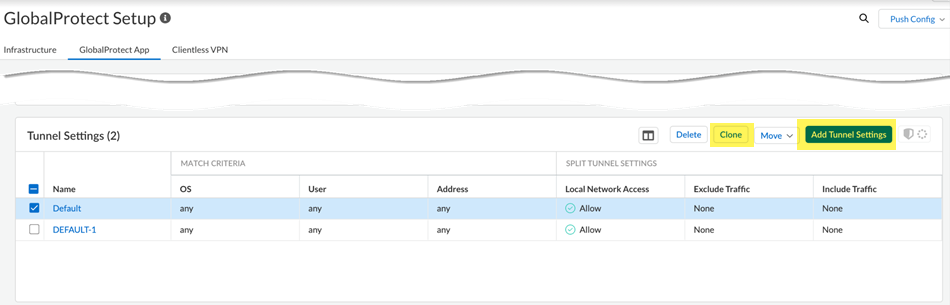
- Click ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessGlobalProtectGlobalProtect AppTunel Settings.Alternatively, you can Clone an existing app setting and modify it.
![]() Enter a name and the Match Criteria to specify the users, devices, or systems that should receive the settings. For example, you could specify that a tunnel settings rule applies to all instances of the GlobalProtect app in a certain region.Enable Authentication Override for Prisma Access to generate and accept secure, encrypted cookies for user authentication. This setting allows the user to provide login credentials only once during the specified period of time.
Enter a name and the Match Criteria to specify the users, devices, or systems that should receive the settings. For example, you could specify that a tunnel settings rule applies to all instances of the GlobalProtect app in a certain region.Enable Authentication Override for Prisma Access to generate and accept secure, encrypted cookies for user authentication. This setting allows the user to provide login credentials only once during the specified period of time.- Generate cookie for authentication override—Enables the Prisma Access to generate encrypted, endpoint-specific cookies and issue authentication cookies to the endpoint.
- Accept cookie for authentication override—Enables Prisma Access
to authenticate users with a valid, encrypted cookie. When the app
presents a valid cookie, Prisma Access verifies that the cookie was
encrypted by Prisma Access originally, decrypts the cookie, and then
authenticates the user.The GlobalProtect app must know the username of the connecting user to match and retrieve the associated authentication cookies from the user’s endpoint. After the app retrieves the cookies, it sends them to Prisma Access for user authentication.
Enable Split Tunneling to define what traffic the GlobalProtect app allows or restricts through the VPN tunnel to Prisma Access. Split Tunneling conserves bandwidth by excluding Prisma Access traffic that is not business critical or does not enable productivity.- Local Network Access—Give Windows and Mac users access to local resources, without requiring them to first connect to Prisma Access.Exclude Traffic—Specify traffic to exclude from Prisma Access policy inspection and enforcement based on application, domain, and route (like an IP address).Customize Include Traffic—By default, the GlobalProtect app routes all traffic to Prisma Access except what's in the exclude list. Specify traffic that the GlobalProtect app should always route to Prisma Access, even when it meets exclude list criteria.
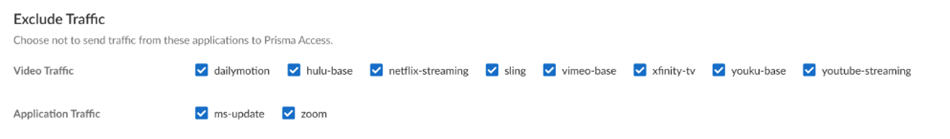
(Optional) Exclude Traffic to not send Video Traffic and Application Traffic from the listed applications to Prisma Access.By excluding lower risk video streaming traffic (such as YouTube and Netflix) and applications (such as Microsoft updates (ms-updates)) from the VPN tunnel, you can decrease bandwidth consumption. The video streaming exclusions are applied to all traffic the GlobalProtect app sends to Prisma Access, not just the match criteria you've defined for this rule.![]() Save the settings. Repeat the above steps to add more tunnel settings.(Optional) Move to set the order of priority in which the VPN tunnel setting is used while connecting to Prisma Access.
Save the settings. Repeat the above steps to add more tunnel settings.(Optional) Move to set the order of priority in which the VPN tunnel setting is used while connecting to Prisma Access.GlobalProtect — Customize Tunnel Settings (Panorama)
Define tunnel settings for GlobalProtect app.You can configure split tunnel settings based on either Access Route or Domain and Application.- Configure split tunnel settings based on Access Route.
- Click Panorama > Network > GlobalProtect > Gateways and select the gateway you want to customize.
- Click Agent > Client Settings and select the config.
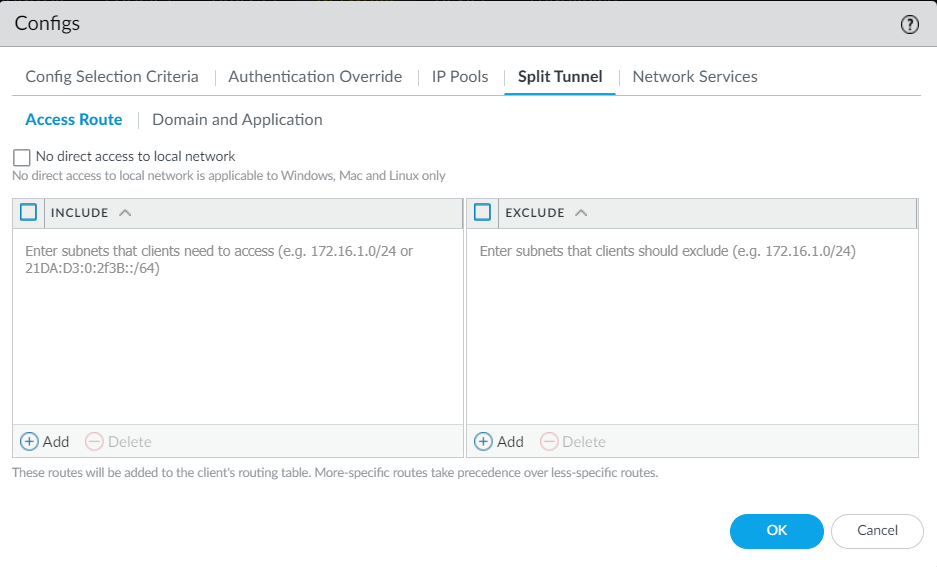
- Click Split Tunnel > Access Route. The split tunnel settings
are assigned to the virtual network adapter on the endpoint when the
GlobalProtect app establishes a tunnel with Prisma Access. You can
include or exclude specific destination IP subnet traffic from being
sent over the VPN tunnel.
![]()
- Enable No direct access to local network option to
stop users from sending traffic directly to proxies or local
resources while connected to GlobalProtect. Enable the No direct access to local network setting to reduce risks in untrusted networks such as rogue Wi-Fi access points.This setting is applicable to Windows, Mac and Linux endpoints only.
- Select Include and Add the destination subnets or address object (of type IP Netmask) to route only certain traffic destined for your LAN to GlobalProtect. You can include IPv6 or IPv4 subnets. To include all destination subnets or address objects, Include 0.0.0.0/0 and ::/0 as access routes.
- Select Exclude and Add the destination subnets or address object (of type IP Netmask) that you want the app to exclude. Excluded routes should be more specific than the included routes; otherwise, you may exclude more traffic than intended. You can exclude IPv6 or IPv4 subnets.You cannot exclude access routes for endpoints running Android on Chromebooks. Only IPv4 routes are supported on Chromebooks.
- Click OK to save the tunnel settings.
- Alternatively, configure split tunnel settings based on Domain and Application.
- Click Panorama > Network > GlobalProtect > Gateways and select the gateway you want to customize.
- Click Agent > Client Settings and select the config.
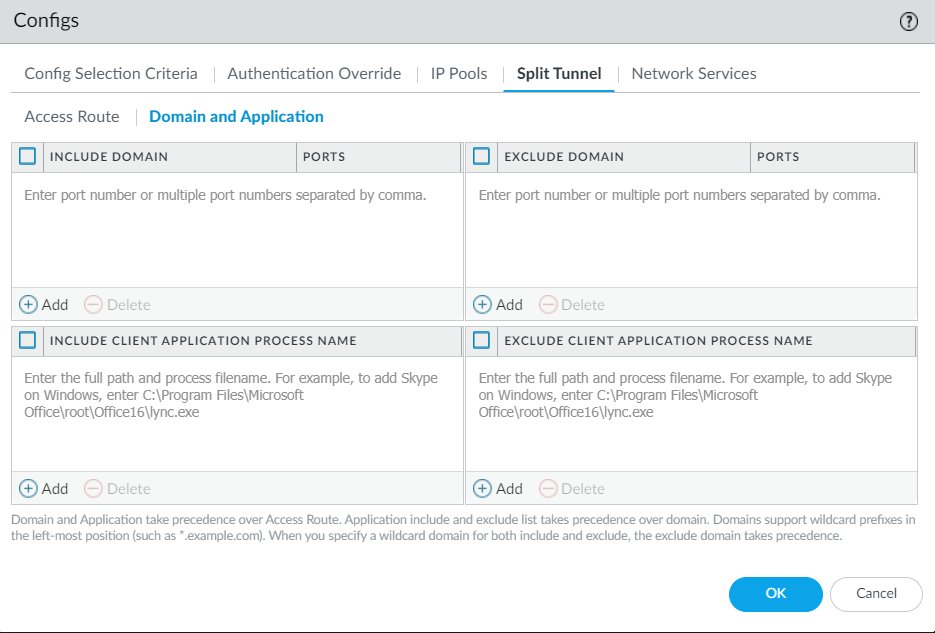
- Click Split Tunnel > Domain and Application tab to configure
split tunnel settings based on the destination domain. You might experience some incompatibility issues when using a third-party endpoint security product such as Sophos on macOS endpoints.
![]()
- (Optional) Select Include Domain and Add the SaaS or public cloud applications that you want to route to GlobalProtect through the VPN connection using the destination domain and port. You can add up to 200 entries to the list. For example, add *.gmail.com to allow all Gmail traffic to go through the VPN tunnel.
- (Optional) Select Exclude Domain and Add the SaaS or public cloud applications that you want to exclude from the VPN tunnel using the destination domain and port. You can add up to 200 entries to the list. For example, add *.target.com to exclude all Target traffic from the VPN tunnel.
- Configure split tunnel settings based on the application.Safari traffic cannot be added to the application-based split tunnel rule on macOS endpoints.You can use environment variables to configure a split tunnel based on the application on Windows and macOS endpoints.
- (Optional) Select Include Client Application Process Name and Add the SaaS or public cloud applications that you want to route to GlobalProtect through the VPN connection using the application process name. You can add up to 200 entries to the list.
- (Optional) Select Exclude Client Application Process Name and Add the SaaS or public cloud applications that you want to exclude from the VPN tunnel using the application process name. You can add up to 200 entries to the list.
- Save the tunnel settings.